As more companies implement hybrid work environments, cybersecurity experts warn of the increased security risks involved with a combination of both on-premise and remote workforces. Hybrid workplaces often require hybrid infrastructures that balance cloud-based applications with in-house operations. Gone are the days when IT departments could draw a circle around their network, knowing that everything inside the circle was secure.
Today’s networks have to contend with fluctuating endpoints and 24-hour access. Hybrid work environments allow employees to work in an office, work remotely, or alternate between the two. According to Gartner, 53% of the American workforce will work remotely at least one day a week by 2022. This statistic is about double of what was seen in 2019. Clearly, the hybrid model is here to stay. So how do businesses secure their web-like corporate networks? 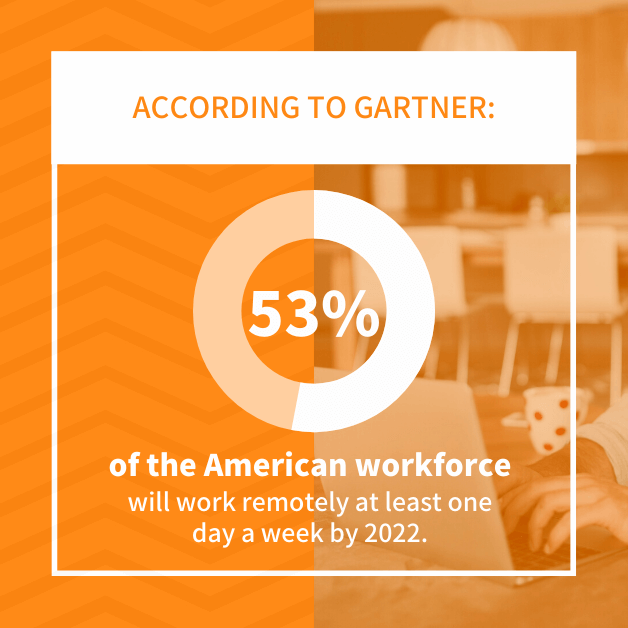
1. Unsecured Endpoints
Every device connected to a network is a potential access point for a cybercriminal. Whether it is a sensor on the factory floor or a remote worker’s laptop, each endpoint presents an attack opportunity if not secured. Companies can easily secure a sensor on a factory floor; after all, they control the network, the factory, and the sensor. It’s not so easy when employees use their own devices and networks to do their work.
IT departments do not have access to an employee’s home network, which makes it difficult to monitor what is happening at the network’s edge. Instead, they have to depend on remote workers to be alert to suspicious activity or implement policies in line with a zero-trust network. Unless businesses provide the laptop or workstation that the employee uses, it’s important to protect the network through authentication and authorization policies. For example, IT departments should have zero tolerance for unrecognized connection requests.
Company policy should require that all endpoint devices be registered to minimize the risk of a hacker connecting using stolen credentials. In the same way, organizations should implement multi-factor authentication for all user access. When everyone worked in the office, IT could update software to minimize potential security vulnerabilities. With remote workers, IT security no longer has that ability. Whether it’s reminding employees to update software or letting IT provide remote updates, companies must find a process to minimize remote vulnerabilities.
2. Avoidance of Virtual Private Networks (VPNs)
VPNs establish a point-to-point connection between a corporate server and a remote device over a public network. Data is encrypted before it is sent through a VPN connection, making it difficult to decrypt the data without the encryption keys. Because of its security features, many companies require remote workers to use a VPN. Sometimes employees try to bypass the VPN connection because it is too slow or the connection drops.
These interruptions can be frustrating to remote workers; however, trying to avoid using a VPN connection exposes a corporate network to added security risks. Without a VPN connection, remote workers connect over a home network with limited security protocols or a public network, like in an airport or coffee shop. While home networks may have more security than a public network, the level of protection depends on the devices and their configurations. Even with maximum protection, information is still being transmitted in the clear, giving bad actors access to sensitive information.
3. Uncontrolled Network Access in Hybrid Work Environments
If employees bypass VPN connectivity on mobile devices or computers connected to a public network, their activities are transparent to anyone looking for a vulnerability. Employees may think that no one is interested in a boring inventory email, but hackers aren’t looking for data. They want to acquire user credentials that can give them access to an entire network. That doesn’t mean they won’t use the opportunity to deliver malware.
Networks are not secure because they ask for a password. Password-protected networks merely limit the number of individuals who can connect. Once a user is on the network, the data transmitted is accessible to anyone with the skills and desire to capture it. For example, many hotels require a password to access their network. The password is only designed to limit access to paying guests. A VPN connection would be needed to secure the data sent over such a network.
4. Lack of Policies for Company Provided Equipment
Company-provided smartphones, workstations, or laptops are IT security risks if they are lost or leave with a terminated employee. If remote workers allow other family members to use their business computers, the potential for a cybersecurity incident increases.
It’s imperative for organizations to ensure policies are in place not only for the business use of equipment, but also for disabling lost or stolen equipment. For experienced cybercriminals, breaking a password-protected device is rarely a deterrent.
5. Employee Behavior
What do the previous four security risks have in common? Employees. Your most important asset can also be your biggest liability. According to Verizon’s latest DBIR, 85% of data breaches are attributable to a “human element.” Most employees are not purposely trying to compromise the company’s network.
They simply become distracted and accidentally click on a link they shouldn’t. Maybe, they misread an email address and sent sensitive data to a bad actor. However it happens, that lapse results in a compromised network. 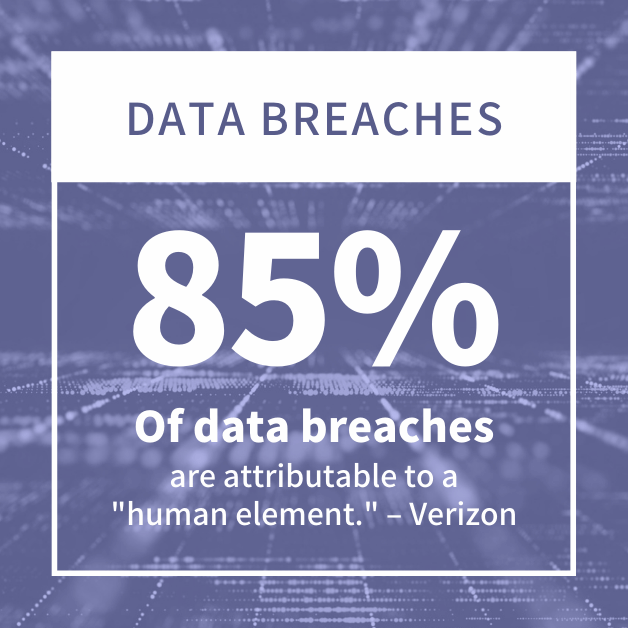
Training your staff on what to look for while working from home helps establish a cybersecurity culture where employees know who to contact when they detect something suspicious. Let people know that reporting an event that isn’t a threat is better than not reporting an event that turns into a breach. Keep employees prepared by alerting them to phishing and social engineering scams as they arise. Unfortunately, insider threats have increased, according to IBM’s latest Insider Threats Report.
Employee negligence contributed to almost half of the insider threat cases. That statistic is an indication that preparing your employees for a hybrid work environment is central to maintaining a strong security posture. As hybrid work environments become a permanent part of the business world, companies are faced with a different set of cybersecurity concerns. The network perimeter is no longer a simple circle. It has become an amoeba that can change shape overnight.
Get a Free, No-Risk Network Assessment
Are you concerned about the IT security risks across your organization’s hybrid work environment? Request your free, independent network assessment today.






