The global connectivity that levels the information playing field among small and mid-sized businesses attracts thieves. Commonly known as “hackers” and “cybercriminals,” these nefarious individuals have the skills to breach business networks almost anywhere on the planet. That reality creates significant adversity for you, someone who works diligently to earn an honest living. By using a cyber-insurance checklist, you can help your business stay safe.
Digital thieves have caused regulatory bodies to issue cybersecurity mandates resulting in companies, like yours, now being tasked with the responsibility of compliance. Despite concerted efforts to thwart hackers, data breaches seem to only increase year-over-year as more businesses purchase cybersecurity insurance. Navigating these complicated insurance policies and staying in compliance has become a job unto itself. But, when you partner with a trusted professional, you can lower cyber-insurance premiums and build robust defenses that obstruct hackers.
Have You Kept Pace with Evolving Cyber-Insurance?
Cybersecurity insurance was once considered something of an afterthought. Company decision-makers and insurance carriers viewed the coverage as low-risk. Even in the event your small or mid-sized company’s data was compromised, the monetary losses were not necessarily significant.
Much has changed as hackers sitting halfway around the world rarely — if ever — get prosecuted for digital crimes. Coupled with online thieves effectively possessing a license to steal, a growing dark web is like a flea market where cybercriminals can easily sell you digital assets. Even a cursory glance at a recent joint IBM and Ponemon Institute report highlights a fast-escalating and expensive crime wave.
- It takes up to 197 days to identify a breach and 69 days to contain one.
- Losses associated with a data breach rose by 10 percent from 2020 to 2021.
- Lost business comprised 38 percent of an organization’s hacking setbacks.
According to a State of Cybersecurity Report, small and mid-sized businesses experience at least one cyberattack within 12 months. Criminal efforts have risen by 20 percent since 2016. Two-thirds of business owners and operators indicate data breach attempts grow more targeted. And upwards of 45 percent admit their cybersecurity defenses are insufficient to hold hackers at bay. 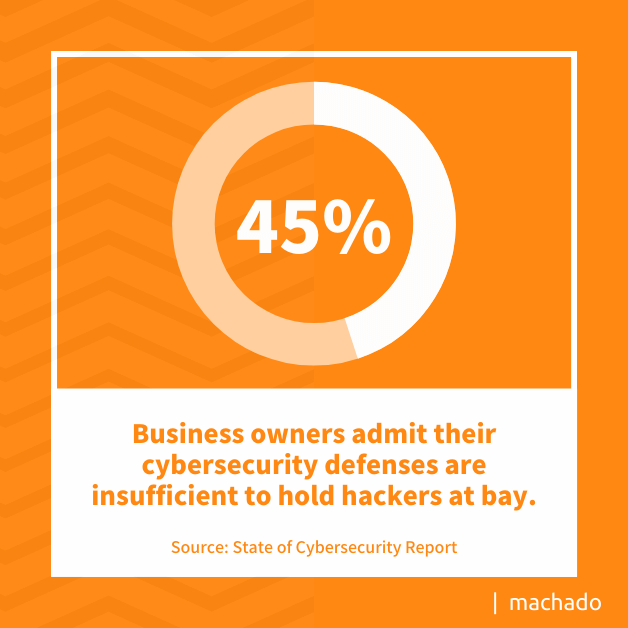
The number of cyber-insurance policies in force skyrocketed from 2.1 million in 2016 to more than 4 million in 2020. Particularly telling is that cyber-insurance policy costs spiked by 21.3 percent from 2019 to 2020, according to the National Association of Insurance Commissioners. As hackers ramp up attacks and businesses sustain greater losses, the cybersecurity insurance market has changed dramatically.
Cybersecurity Insurance Trends
Experienced business professionals like you, typically understand that industries such as lending and insurance integrate risk metrics. The bank reviews your FICO score, debt-to-income ratio, and repayment history when considering a loan application. The same essentially holds true for the insurance sector. Low risk generally results in lower premiums when compared to high-risk policies. For all intents and purposes, hackers are costing you money in the following ways.
- Supply and Demand: The rapid increase in organizations securing cyber-insurance and the rising number of losses has reportedly caused the market to tighten. Insurance carriers are not necessarily writing policies as freely as they did before cyberattack losses spiked.
- Rising Premiums: Insurance corporations continue to manage risk through policy costs. According to a National Law Review report, cyber-insurance renewal rate increases of 100-300 percent are not uncommon.
- Reduced Coverage: Taking out $10 million in cyber-insurance coverage was once a relatively common business practice. But the high price of insurance now has decision-makers weighing the expense against the risk. Reducing coverage to $5 million or less appears to be a troubling trend.
A 2021 Fitch insurance industry report highlights many of the cyber-insurance pressure points. Findings published in Sharply Rising Cyber Insurance Claims Signal Further Risk Challenges provide a comprehensive understanding of market trends. The piece also provides insight into ways you can lower premiums. 
Cyber-Insurance: How to Select a Policy
Although the cost of cyber-insurance continues to rise, more business leaders are purchasing policies or adding riders. A 2020 Cyber Readiness Report published by Hiscox states that 58 percent of cybersecurity professionals polled indicated their organization purchased cyber-insurance. That figure rose from only 41 percent the previous year.
Unlike other business protections, familiarity with cyber-insurance typically lags. By understanding some of the nuances of cyber-insurance, you can be proactive and secure a policy that fits your needs. 
The second cyber-insurance coverage involves “third-party claims.” These stem from entities and people in your digital orbit who suffer a loss due to hackers infiltrating your network. A less-than-secure user profile of an intern can open doors for persistent threats to exploit. Once inside your network, cybercriminals can take their time and expand their knowledge. This may include discovering login credentials for other companies and stakeholders.
Third-party claims often result in civil lawsuits, with the initial victim compensating others. Adding insult to injury, the originally hacked organization suffers a diminished reputation. That’s why it’s crucial that you secure first- and third-party claims cyber-insurance. The following are other items to pay close attention to when purchasing coverage.
Be Mindful of Duty to Defend Clause
This provision tasks the insurance company with protecting your organization from costly litigation. The insurance provider generally selects legal counsel while the hacked organization focuses on recovering from the incident.
Ransomware Coverage or Rider Remains Necessary
Hacks such as the Colonial Pipeline made national news after cybercriminals infected the fuel distribution outfit with ransomware. Portions of the eastern seaboard experienced gasoline and diesel shortages. Colonial reportedly paid digital thieves millions to regain control of their system. Insurance companies may be inclined to offer policies that exclude ransomware attacks or require an additional rider.
One of the ways providers are re-imagining cybersecurity insurance coverage is by requiring improved cyber-hygiene from policyholders. Much like homeowners insurance involves fire codes, occupancy permits, and routine inspections, industry leaders may be tasked with hardening their cybersecurity defenses. 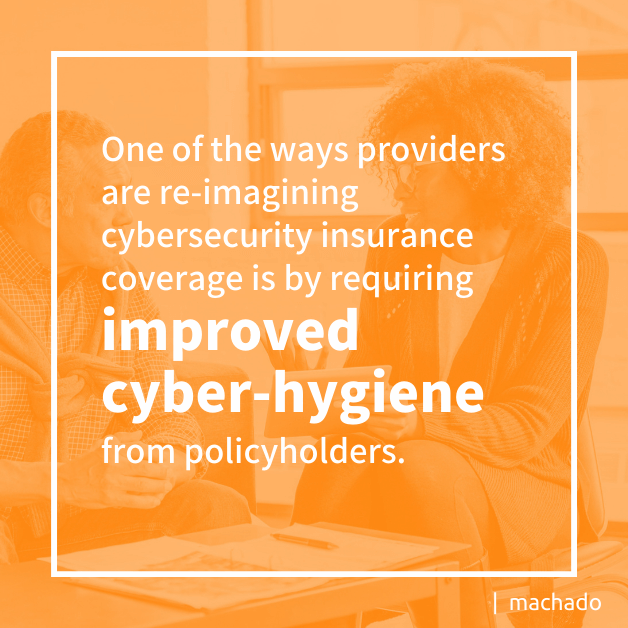
How Can Business Leaders Maintain Cyber-Insurance Compliance?
Thought leaders tend to understand cybersecurity insurance as a key piece of a much larger business landscape. In its simplest form, cybersecurity insurance is purchased to offset risk. Individual coverage decisions weigh the cost against potential benefits. But from a holistic perspective, insurance also brings issues involving regulatory compliance and front-line cybersecurity defenses into focus.
Failing to meet industry standards or those imposed within the policy could have a chilling effect on your organization. Oversight agencies could level fines or suspend licenses, and an insurance claim following a data breach could be denied. Even worse, you could inadvertently quash your duty to defend protection.
These potential harms are just the tip of the spear and a good reason to take a look at a cyber-insurance checklist. By enlisting the support of a cybersecurity expert and hardening your defenses, you’ll be able to secure digital assets and lower premiums. The following cyber-insurance checklist provides 10 recommendations to help you with your compliance requirements.
Cyber-Insurance Checklist
1. Hire a Professional
Federal and state agencies provide detailed security and privacy expectations for wide-reaching industries. Remaining compliant with the Health Insurance Portability and Accountability Act, Federal Information Security Management Act, General Data Protection Regulation, or Payment Card Industry Security Council’s Data Security Standard, is not a mystery to a cybersecurity consultant. By working with a professional who possesses niche expertise, you can outsource a complicated business necessity.
2. Secure Broad Cyber-Insurance Coverage
If your budget is tight, you may try to cut costs by omitting insurance riders or lowering claims limits. In terms of cybersecurity insurance policies, a higher claims threshold and comprehensive coverage are generally advisable. One successful ransomware attack could cripple your organization and dash your livelihood.
3. Enforce Password Policies
Everyday people have dozens of online profiles, and they tend to repeat usernames and passwords. Remembering these login credentials also leads some to use simple and predictable passwords. Require your entire workforce to change passwords four times each year and only use ones rated as “strong.”
4. Implement Zero-Trust Measures
The term “zero trust” seems to indicate business leaders hold a low opinion of their employers. This cybersecurity strategy has nothing to do with your feelings about others. When a persistent threat actor targets one of your valued employees, the chances of unveiling the person’s login credentials increase. But zero trust measures limit each team member’s access to only the information they require to complete tasks. Even if a hacker triumphs, the cybercriminal’s access is limited.
5. Cybersecurity Awareness Training
Loyal employees do their level best to protect and defend your network from incursions. But unlike a certified cybersecurity consultant, their knowledge of the latest hacking techniques is quite limited. Proactive cybersecurity leadership involves educating people about commonly used hacking strategies and emerging threats. Once team members understand how to detect phishing schemes and ransomware deployments, they can receive remote briefings and alerts. Integrating an awareness training program also galvanizes a company-wide cybersecurity culture.
6. Develop a Safe Data Backup System
It’s not unusual for people to click on a backup icon and assume their files are safe and secure. Nothing could be further from the truth. Ordinary backups simply save the latest version of work products for later access. Should a cybercriminal infiltrate your system or level a ransomware attack, those files are in the thief’s hands. Secure backup protocols typically call for digital assets to be saved in multiple locations. Hard drives, more than one Cloud platform, and storage devices that are not connected to your network or the internet may be the only truly secure backups. A cybersecurity consultant can walk you through best practices.
7. Build Remote Cybersecurity Infrastructure
The pandemic accelerated wide-reaching industries’ willingness to employ remote workforces. When people’s movement was initially restricted, organizations found themselves scrambling to create or expand remote capabilities. In too many instances, cybersecurity measures took a backseat to immediate productivity. With the virus seemingly in retreat, it’s time to build robust cybersecurity throughout the work-from-anywhere landscape. For example, establishing virtual private networks (VPNs) allows field workers to securely connect to your network. A VPN allows your employees to remain unseen, unlike those connecting to coffee shop chain Wi-Fi.
8. Data Encryption Protocols
Electronic messages remain a focal point for hackers to beach your systems. Phishing schemes and ransomware deployment leverage email and other forms of digital communication. But sophisticated hackers can also intercept messages and gather valuable information from your communications. Encryption acts as a strong deterrent to cybercriminals targeting employee email. Even if they manage to lay their greedy hands on an email, they cannot read its contents. A cybersecurity consultant usually urges industry leaders to include encryption protocols to ensure privacy measures consistent with HIPAA and other regulations.
9. Third-Party Penetration Testing
The value of tasking a cybersecurity consultant with testing your organization’s defenses cannot be understated. Hackers tirelessly look for backdoors and cracks in your system that allow them access. Penetration testing effectively simulates what a bad actor would attempt to pilfer off your digital assets or seize control over your operation. By conducting a blind penetration testing effort without staff members’ knowledge, you will discover precisely where vulnerabilities exist. That information allows you to circle back and resolve cybersecurity deficiencies.
10. Develop a Comprehensive Cybersecurity and Response Plan
An increased number of industry leaders are formalizing their cybersecurity policies and integrating incident response plans. These efforts send a message throughout your organization that cybersecurity is part of the team’s daily responsibilities. Crafting a detailed document and making it accessible to the entire workforce offers specific methods and best practices that further goals.
In the event a bad actor infiltrates your operation, a select group of department heads and leaders must minimize the damage. The cybersecurity response plan empowers them to carry out defensive duties in real-time and guide co-workers through the attack. A forward-thinking incident response plan also lays out next steps to bring a system back online and resume operational control. Having a comprehensive policy and incident response plan in place usually alleviates risk concerns when taking out a cybersecurity insurance policy.
Benefits of Working with a Trusted Cybersecurity Consultant
The technology sector has grown highly specialized, and thought leaders see heightened value in outsourcing cybersecurity efforts. That’s largely because your in-house IT staff members typically have a full plate keeping your network functioning efficiently and employees digitally connected. Few have enough time to adequately address cybersecurity, and staying apprised of emerging threats is virtually impossible.
By contrast, a third-party cybersecurity consultant maintains a laser focus on enhanced protections, regulatory compliance and walks you through the essential items on a cyber-insurance checklist. Firms with cybersecurity experts are keenly aware of the latest hacking tricks and help your workforce become a front line of defense. Because a third-party cybersecurity consultant can be onboarded within a budget, your organization can build the determined defenses necessary to deter and respond to threat actors.
Contact us today to learn about the benefits of working with a trusted cybersecurity partner.
If you are considering cybersecurity insurance or are looking over your current coverage, let’s talk!. By shoring up your network protections, achieving compliance, and making insurance carriers aware you’ve enlisted the support of an experienced professional, you may gain access to better rates and a more comprehensive policy.