The business world has come full circle when it comes to finding skilled computer technology staff. Now, more than ever, with cybercrime growing at a projected annual rate of 15%, staffing your cyber team requires not just time, but also an understanding of specific traits to review.
Basically, whether you’re planning to hire full-time employees or are moving in the direction of a co-managed IT model with a consulting partner, it’s important to conduct a cybersecurity talent assessment when selecting such critical members for your team.
Sixty years ago when computers began infiltrating the business world, what we currently know as Information Technology (IT) was a mathematical domain. Engineers were involved in designing and building hardware, and mathematicians were the computer scientists. It wasn’t until the 1980s that Computer Science and Information Technology became their own fields of study. 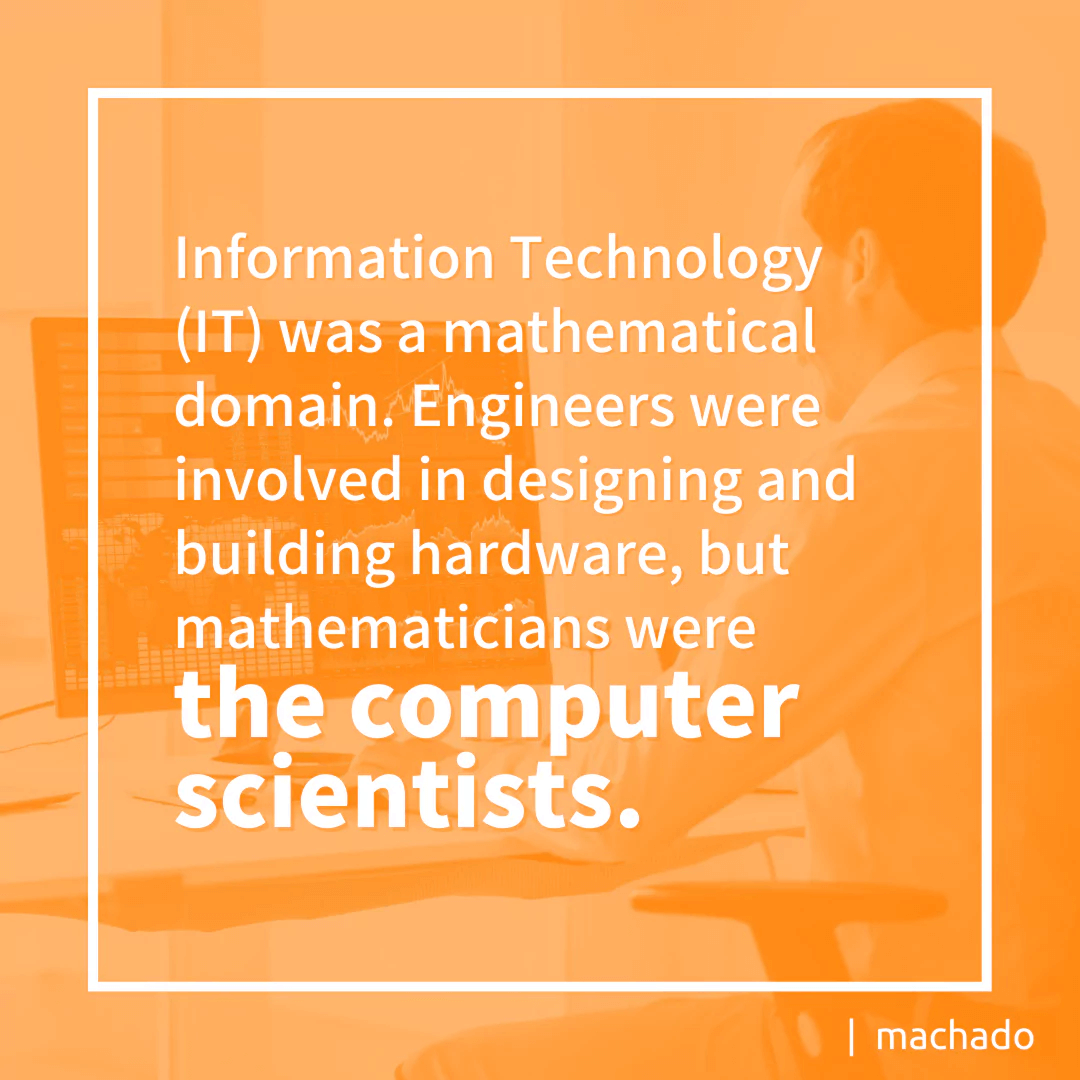
As a result, many businesses hired employees based on their skills and experience, and not on their formal education. Companies looked to government employees, especially former military personnel, as valuable candidates. The government provided on-the-job training in computer technology. After all, it was its largest user in the mid-to-late 20th century. Other candidates were self-taught with no consistent educational background or degree. Yet, businesses hired them because they needed their skills to stay competitive.
Sound familiar? The reasons may be different and the skills more specialized, but the result is the same. If you’re experiencing the challenge of hiring or retaining top-notch cybersecurity talent, you’re not alone. It’s time to take a lesson from the past and think outside the box.
A Perfect Storm
A recent survey found that 62% of security teams were understaffed and 63% had unfilled positions. This lack of applicants comes at a time when cybercrime is projected to increase at a rate of 15% per year. Still, survey respondents indicated it took more than six months to find qualified candidates. The respondents were looking for individuals with hands-on cybersecurity experience, security credentials, and training. 
A final component of this perfect storm is the change in work environments and employee priorities. With more companies looking at hybrid work environments, employers are also looking for candidates who are dependable, can communicate effectively, and solve problems.
Dependability has become a leading factor as more technology positions can be performed remotely. However, remote workers need strong communication skills to be contributing team players. Problem-solving skills have always been needed, but the changes in how and when work gets done have made communication skills a priority.
Employees have become bolder with communicating their priorities recently. After many were forced to work from home for the past two years, many have become more focused on work-life balance after experiencing the flexibility with work-from-home opportunities. Younger employees also value environmental, social, and governance (ESG) issues and are looking at companies that reflect their ESG concerns.
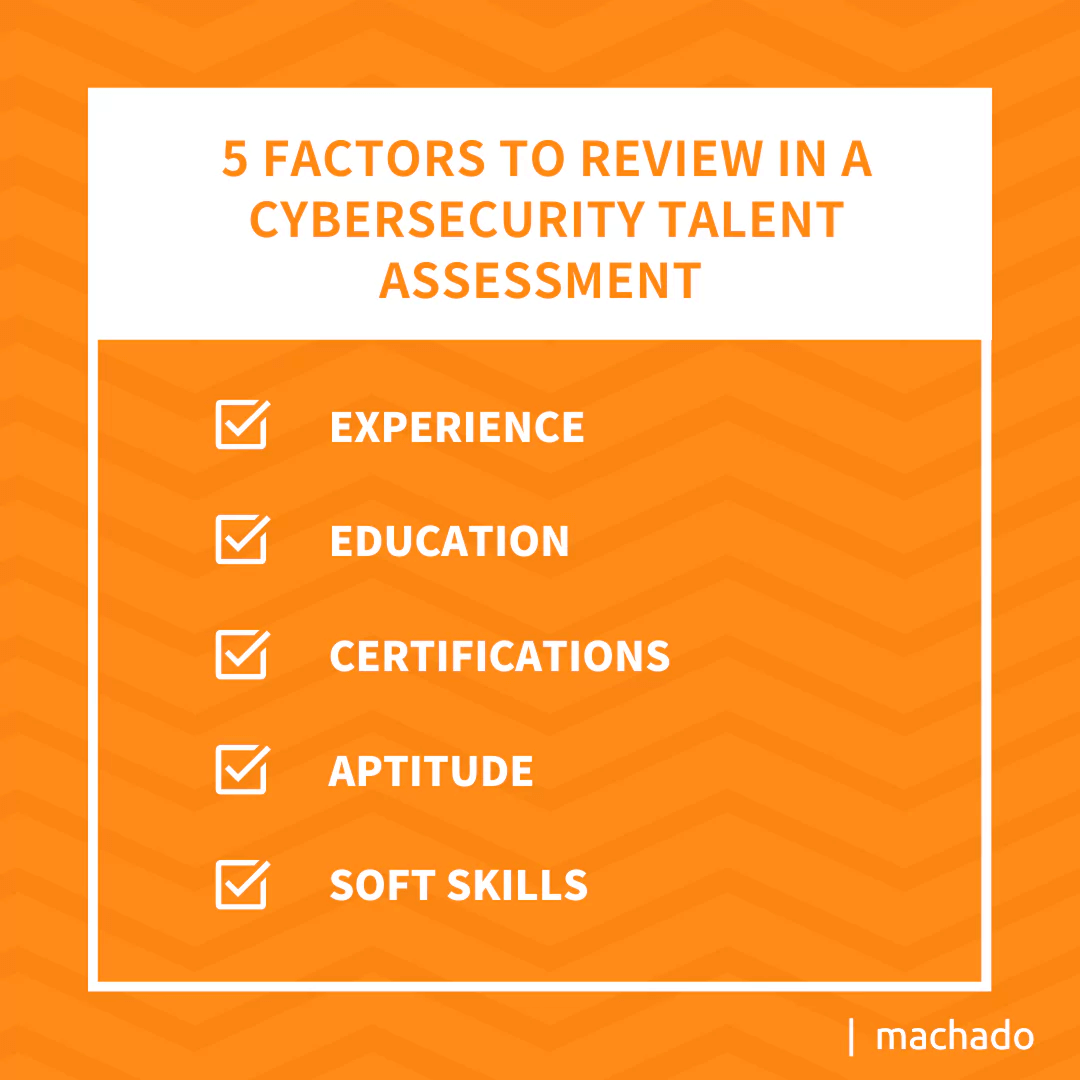
So, how can you fill the gap in qualified cybersecurity talent? Whether you choose to pursue hiring new employees or go the route of creating a co-managed IT partnership, you need to evaluate these five factors when building your cybersecurity team.
- Experience
- Education
- Certifications
- Aptitude
- Soft Skills
Companies should broaden their algorithms when screening resumes and perform a cybersecurity talent assessment to know exactly what skills are needed for each position. If employers want top cybersecurity talent, they will need to look beyond a four-year degree or what’s highlighted on a resume.
5 Factors to Review when Selecting Your Cyber Team
1. Experience
The most frustrating phrase for any entry-level cybersecurity applicant is “Degree + ‘x’ years of experience.” How exactly do applicants gain experience if no one will hire them? Businesses should consider looking outside corporate environments when evaluating experience. Today, more high school and community college programs offer internships where students gain work experience.
Many companies have screenings in place that dismiss non-work-related experiences. Individuals who volunteer their cybersecurity skills are often eliminated when they may have the perfect combination of skills for the position. For example, someone who uses their free time volunteering to help with cybersecurity threats for a local nonprofit may have a strong commitment to lifelong learning which is a critical component of a successful cybersecurity specialist.
The same concept applies to those who have gained experience through military service. Cybercriminals do not discriminate. They use the same tools to compromise a government network as a corporate one. If military personnel have applicable experience, businesses should embrace their capabilities even though they come from outside the business world. 
2. Education
A four-year degree may not be necessary for every cybersecurity position; yet, most HR departments continue to use that as a screening factor. Cybersecurity changes at internet speed, meaning hackers are finding new ways to compromise a system faster than security specialists can contain them.
A recent article suggested that higher education has a responsibility to prepare students for securing the future and suggested that foundational cybersecurity skills should be taught across all computer science specialties. It was suggested that cybersecurity concepts should be part of every degree program because it impacts every industry from banking to healthcare. Finally, higher education faculty need to have access to tools and training on all the latest cyber threats.
Community colleges and vocational training programs often have an edge when it comes to current technology. Many partner with local businesses to develop programs that meet the needs of the community. This collaboration enables educators to address the current cybersecurity environment while providing a foundation in basic cybersecurity theory. In these relationships, the vision of faculty experiencing what is happening outside the classroom is a reality.
High school and vocational schools often work with businesses to provide students with on-the-job experience while in school. This cooperative effort exposes students to cybersecurity threats early. For some, it is the beginning of an educational opportunity partially funded through a local business.
According to the World Economic Forum, closing the gap means “connecting the dots between early STEM education, cybersecurity career training, hiring methods, and ongoing skill development.” The traditional path through higher education can no longer be the only viable option.
3. Certifications
Cybersecurity is constantly evolving. When you evaluate either potential candidates or consulting partners, do take their certifications into account. The following are the top certifications for a cybersecurity specialist according to leading professionals.
- CompTIA Security+. A global certification to validate baseline skills for core security functions granted by the Computing Technology Association.
- Certified Information Systems Security Professional (CISSP). A certification granted by the International Information System Security Certification Consortium (ISC2) covering eight domains within Information Systems and Security.
- Certified Cloud Security Professional (CCSP). A certification granted by the ISC2 related to cloud security.
- ISACA Certified Information Security Manager (CISM). A certification covering information security governance, program development, and incident and risk management.
- CompTIA Pen Test+. A certification covering how to configure, run and interpret penetration tests.
Vendors such as Microsoft, Amazon, and Google offer certifications related to their products and services. Certifications are a way for professionals to demonstrate value-added skills in cybersecurity. Ignore certifications at your own peril. They are a key indicator of the depth of knowledge of your applicant or consultant as they show their commitment to their profession.
4. Aptitude
Not everybody is destined to be a cybersecurity specialist., let alone an expert. Even if they have the technical skills, they may lack the aptitude needed to thrive in the field. A recent article suggests your business should look for individuals or consulting practices that show these attributes:
- Curiosity. Cybersecurity specialists need to ask why. They should have a desire to investigate beyond the superficial and be willing to explore possibilities.
- Problem-solving. Ultimately, cybersecurity is about solving problems using scientific methods that are analytical and methodical.
- Disciplined. For cybersecurity staff and consultants to retain their skills, they need to be constantly learning, which takes self-discipline.
- Ethical. Cybersecurity is about protection. Individuals need to be dependable and transparent in delivering that protection.
- Flexible. Security personnel often function as consultants, making recommendations and offering guidance.
Digging into these attributes is central to a cybersecurity talent assessment. Some people enjoy computer science because of its systems. They like programming languages with their structure and syntax. The flexibility and collaborative nature of cybersecurity may not be a good fit despite their technical skills.
5. Soft Skills
Soft skills may be as important as technical skills depending on the specialty. Not everyone who works in cybersecurity has programming skills or knows how to design a network’s infrastructure. With the right soft skills, they can not only secure a network and explain how the security works to upper management. You need to consider soft skills, like these, when conducting a cybersecurity talent assessment.
- Communication. Whether written or verbal, communication is a critical skill for cybersecurity talent, whether on your staff or a consultant. Incident reports or security processes require documentation. Non-technical audiences will need to understand technical concepts without all the technical terms. Communication also involves listening, and cybersecurity specialists will need those skills to understand what non-technical and technical staff are trying to explain.
- Collaboration. Cybersecurity is a team effort. Whether it is a team of two or 20, professionals need to share their expertise to build a stronger community of cybersecurity talent.
- Adaptability. Technology changes. With each technical advance comes a new cyber threat. That requires individuals who can adjust to a changing environment and be willing to learn how to protect against emerging cybersecurity threats.
- Critical Thinking. Security personnel must ask the right questions and evaluate the answers to determine how to effectively combat cyber threats. They must be willing to let go of assumptions and look at data before coming to a conclusion.
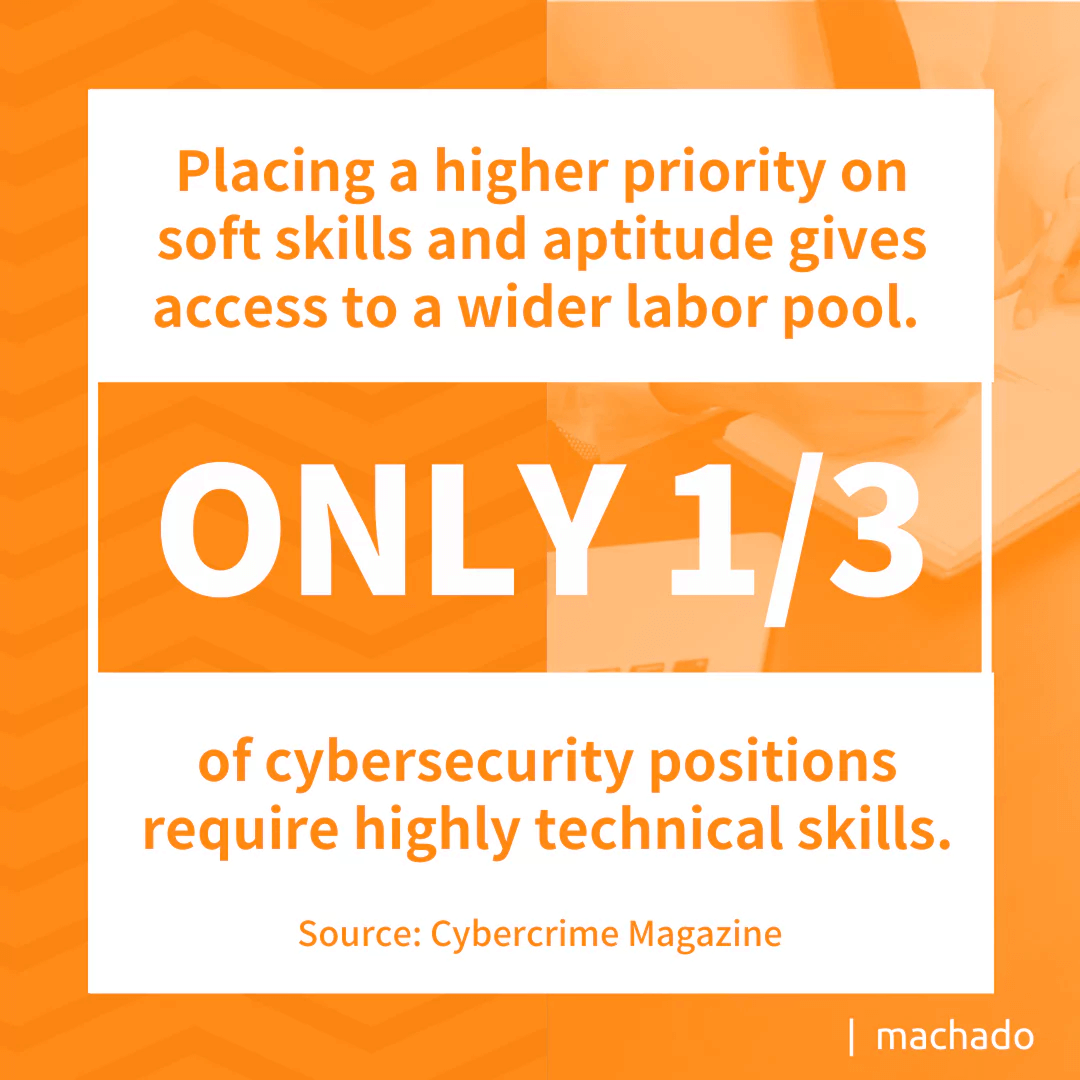
Placing a higher priority on soft skills and aptitude gives greater access to cybersecurity talent. A recent article in Cybercrime Magazine stated that only one-third of cybersecurity positions require highly technical skills and even suggested looking outside IT for potential cybersecurity staff. If going in that direction, talent with fewer technical skills may benefit by working in a co-managed IT arrangement by having access to a team of experts to fill that technical gap.
Weathering the Storm
Weathering the perfect storm requires innovative thinking. It means looking beyond the traditional degree plus experience to find candidates with the right mix of technical and soft skills. Rather than waiting for the storm to pass, consider pursuing the following:
- Consider partnerships with local educational institutions that provide a pipeline of future candidates.
- Develop growth paths for employees that have the aptitude to become cybersecurity specialists.
- Encourage existing security employees to pursue ongoing development through certifications.
- Automate routine security functions to free staff to perform more challenging tasks.
- Partner with a consultant with expertise in cybersecurity to support your business objectives.
One path is not enough to combat the labor shortage. Organizations need partnerships to ensure a sustainable pipeline. Now is a good time to evaluate your operations to determine what tasks can be performed without human intervention. Finally, consider outsourcing either specific areas of your cybersecurity to a trusted advisor that can provide the expertise you need.
Contact us today to learn about the benefits of working with a trusted cybersecurity partner.
Selecting a partner with the cybersecurity expertise to support your business can seem as challenging as finding a viable in–house candidate. Let’s talk about how working with a consultant with 20 years of experience serving the Massachusetts market can help you. Our team has decades of combined cybersecurity experience, along with the certifications, business skills, and professional acumen to do more than just weather the storm you’re experiencing in today’s hiring environment.