TL;DR:Securing server data is crucial in today’s digital world due to rising cyber threats. Protecting this data ensures smooth business operations and the safety of sensitive details. Small to medium-sized businesses (SMBs) are particularly at risk and should prioritize this aspect of their IT. Proactive steps, rather than reactive approaches, offer the best defense against potential breaches. Seeking expert assistance can boost both security and performance.
The data that lives on the servers within professional services firms is both an invaluable—and irreplaceable—asset.
It’s not just a matter of bytes and bits; it’s the driving force behind decision-making, innovation, and growth.
For example, healthcare providers analyze patient data to improve outcomes and personalize care, while law firms might utilize data analytics to predict litigation outcomes or streamline legal research. Banks and financial institutions heavily rely on data to assess credit risk, detect fraud, and offer personalized financial products.
In essence, data helps you tailor your services, improve efficiency, and anticipate the needs of your clients. Data is important—it might be one of the most valuable assets your business has.
And just as you would secure your valuable personal belongings, it’s equally crucial to safeguard your business data.
Think of protecting your business data like making sure your house is locked up tight. If you lived in a neighborhood where break-ins were common, you’d definitely make sure to lock up, maybe even get a security system.
You wouldn’t just do it after someone tried to break in; you’d do it beforehand to avoid any trouble.
It’s the same with businesses.
The threats to your business data aren’t abstract risks; they have tangible implications on your operations, reputation, and bottom line and it’s essential to address these threats head-on. Being online is like living in that neighborhood, you need to protect your business, and your data.
We wrote this article to provide you with a comprehensive understanding of data protection and the crucial role a proactive Managed Service Provider (MSPs) like Machado plays.
The Intrinsic Value of Data in Your Company
The significance of data in our day to day becomes unmistakably clear.
But what makes this data so indispensable to your business?
Data, in its various formats and contexts, underpins the strategic and operational frameworks of SMB firms across the globe. Let’s explore 4 facets that elevate its significance:
1. Value of Data:
At its core, data controls every pivotal decision, embedding its influence from strategic planning to daily operations.
Data is not just a resource; it’s an asset.
An asset which shapes the trajectory of innovations, strategies, and market penetrations. From enhancing customer experiences with tailored offerings to streamlining operational processes, data’s potency in driving business objectives is undeniably profound.
2. Regulatory Compliance:
The importance of global and regional data protection regulations cannot be understated. GDPR, CCPA, and a list of other acronyms not only symbolize regulatory frameworks but also represent a pact of trust between businesses and their stakeholders.
These regulations require a strategic alignment of data management practices to safeguard against punitive repercussions and to fortify operational legitimacy.
3. Trust and Reputation:
In a climate where consumers wield the power to make or break reputations, securing server data becomes pivotal. A single breach can cascade into a reputational avalanche, dismantling trust and impacting customer loyalty.
In a recent report 94% of consumers said they would not purchase from a business with unsafe data storage. Here, safeguarding data translates into safeguarding the organizational image, where every byte protected is a step towards solidifying trust with consumers.
4. Competitive Advantage:
Picture this – two businesses, parallel in capacity and market presence.
The differential? Their approach to server data protection.
The business that guards its data not only shields itself from disruptive breaches but also fortifies its market position. This protective shield safeguards its trade secrets, ensures uninterrupted operations, and acts as an enhanced customer trust, thereby cementing its competitive standing in the digital arena.
Having established the undeniable value of server data within your day to day, it’s crucial to turn our attention to the threats that lurk, seeking to exploit any vulnerability in our server data protection measures.
Decoding Data Threats Proactively
Threats to data have turned from isolated incidents to complicated, multi-faceted challenges. As you expand, you inadvertently grow your vulnerability footprint. Let’s dissect 4 of the pressing threats:
1. Supply Chain Vulnerabilities:
Complex supply chains mean that firms are rarely isolated entities; they’re part of an intertwined web of vendors, partners, and collaborators. A chink in the armor of one partner can turn into a full-blown breach for the industry. A singular vulnerability at a third-party vendor can lead to unauthorized access to systems, causing ripple effects that compromise data integrity across the supply chain.
2. Ransomware Attacks:
Gone are the days when cyber threats were just about accessing data. Now, they’re about holding it hostage. Ransomware, a malicious software that encrypts data and demands a ransom for its release, has seen a stark upsurge. The repercussions aren’t just monetary; they involve operational standstills, potential data loss, and an undeniable hit to an organization’s reputation.
3. Cloud Security:
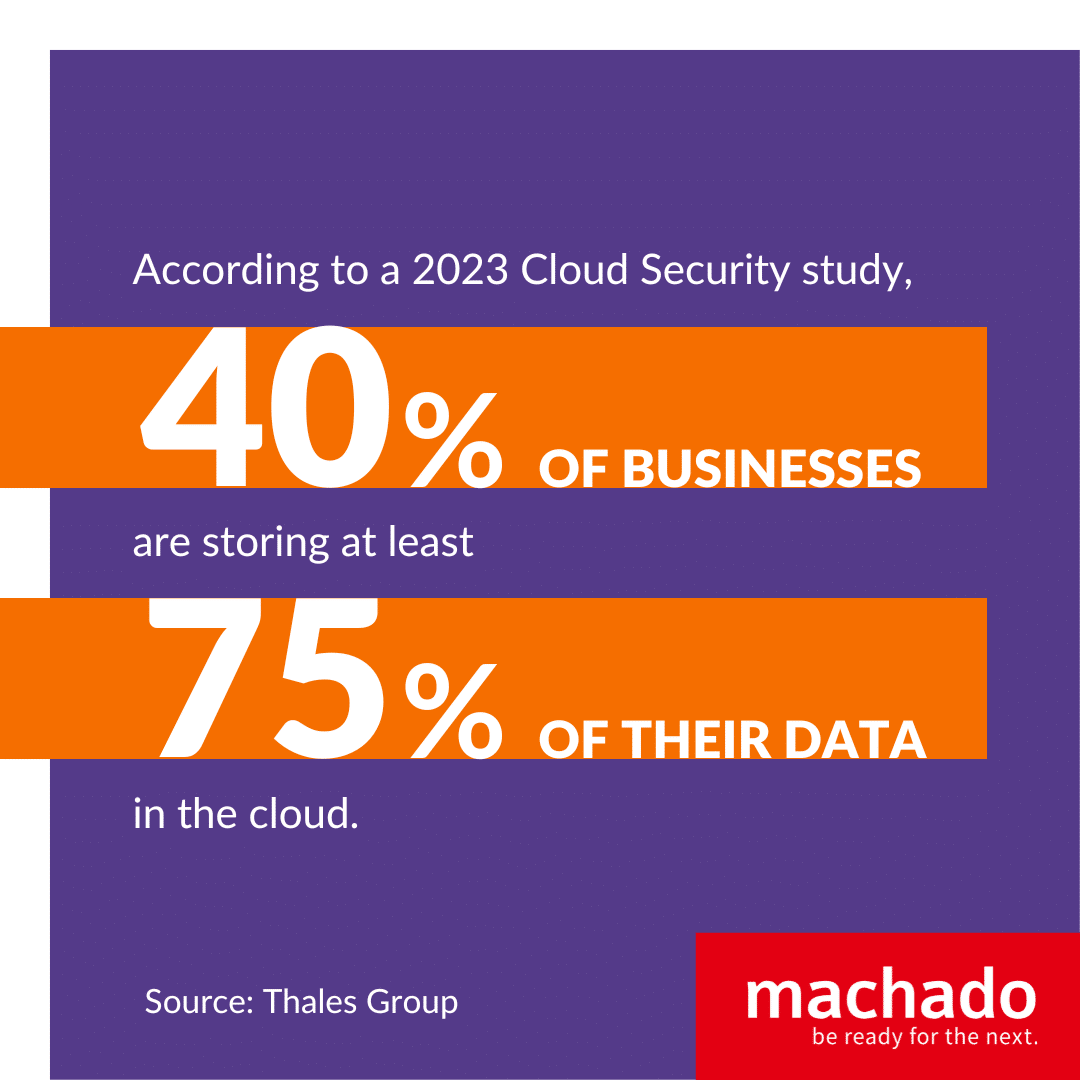
The allure of the cloud is undeniable: scalable, efficient, and cost-effective. Reports like this show that 40% of businesses are storing at least 75% of their data in the cloud.
But as more small to medium businesses migrate their server data reservoirs to cloud infrastructures, your firm may encounter problems. Inadequate access controls, misconfigured settings, or even shared technology vulnerabilities can compromise cloud data, leading to unauthorized access or server data leaks.
4. IoT Threats:
The future, they say, is interconnected. But with the rise of the Internet of Things (IoT) – from smart thermostats to interconnected production machinery – comes a fresh set of vulnerabilities. Each connected device is a potential entry point for cyber adversaries. The sheer volume of these devices, combined with inconsistent security protocols, makes IoT an emerging area for server data threats.
We’ve outlined the various threats targeting valuable server data. These challenges are challenging, evolving, and constant. It begs the question: How well-prepared are our reactive IT defenses? Are the teams we’ve trusted for years equipped to handle these new-age challenges? Let’s evaluate the limitations of standard IT setups, and how we can better prepare our teams.
Recognizing the Limitations of Reactive IT Teams
As cyber threats evolve, so do the challenges they present. Reactive IT teams, while integral to the operations of many companies, sometimes grapple with these modern hurdles. Here are some of the core challenges:
1. Lack of Specialized Knowledge:
Cyber threats are becoming increasingly sophisticated, requiring a depth of knowledge that goes beyond the standard IT curriculum. While reactive IT teams excel in day-to-day operations and general troubleshooting, the nuanced expertise required to combat advanced cyber threats might be lacking.
2. Resource Constraints:
Modern Cyber Security demands a suite of specialized tools, software, and continuous training. Budgetary constraints or a lack of focus on IT can hinder the team’s ability to stay updated with the latest security measures or to invest in essential tools.
3. Reactive Approach:
Historically, many IT teams operated on a reactive model – responding to issues as they arose. In today’s threat-laden environment, a proactive approach is crucial. Waiting for breaches to happen and then addressing them can lead to significant data loss and reputational damage.
Having shed light on the challenges IT teams face, it becomes evident that a more specialized and proactive approach might be the answer. How do Proactive Managed Service Providers (MSPs) fit into this narrative? And more importantly, what advantages do they offer to counteract the limitations we’ve discussed? It’s time to explore the vital role of proactive MSPs in navigating and neutralizing modern Cybersecurity hurdles.
The Elevated Role of Proactive MSPs in Modern Cybersecurity
The dynamic nature of today’s Cybersecurity challenges calls for an equally dynamic response. This is where proactive MSPs step in, bridging the gap left by reactionary IT setups. Let’s dive into the distinct advantages they bring to the table:
1. 24/7 Monitoring:
The internet doesn’t operate on a 9-to-5 schedule, and neither do cyber threats. Proactive MSPs deploy advanced tools and systems that offer round-the-clock surveillance, ensuring any irregularities are swiftly detected and addressed.
2. Focused Expertise:
With a primary mandate centered on IT security and infrastructure management, MSPs harbor expertise that’s both deep and broad. This specialized knowledge becomes crucial when navigating cyber threats and setting up defense mechanisms. With ransomware attacks increasing, and DDoS attacks costing somewhere from $20-$10,000 per day according to this report, enlisting an MSP can save on these timely and expensive attacks.
3. Regular Backups:
Server data loss can be catastrophic. Recognizing this, MSPs prioritize routine server data backups, ensuring that, in the face of unforeseen contingencies, server data restoration is seamless.
4. Patch Management:
In the vast world of software applications and systems, vulnerabilities can emerge over time or when faced with newer threats. MSPs don’t just apply patches; they systematically monitor, test, and deploy these updates across the infrastructure. This diligence ensures that software isn’t just current, but also optimally secure against known vulnerabilities.
5. Employee Training:
Recognizing that technology alone can’t guarantee security, MSPs emphasize the human aspect to protect your server data. Regular and targeted training sessions are orchestrated to keep employees abreast of the latest threat vectors, safe practices, and protocols. This approach not only empowers staff but also fortifies the organization’s first line of defense against potential breaches.
6. Strategic Planning:
Beyond the immediate, Proactive MSPs collaborate to craft long-term IT strategies. This foresight ensures that the IT infrastructure evolves in tandem with the organization’s growth and changing needs.
Having explored the proactive measures and strategies implemented by MSPs, the next logical question is: What concrete benefits can firms expect when they make the leap to partner with these providers? Let’s examine the tangible rewards that this collaboration can bring.
Tangible Benefits of Partnering with MSPs
Engaging with a Managed Service Provider offers more than just enhanced security; it offers your firm an opportunity to streamline operations, optimize investments, and ensure sustainability. Here’s a deeper look at the myriad benefits:
1. Business Continuity:
In an era where downtime can lead to significant financial and reputational losses, MSPs play a crucial role. They implement multi-layered security protocols, backup solutions, and disaster recovery plans to ensure that, come what may, your business operations face minimal interruptions.
2. Focus on Core Operations:
With the complexities of IT security handled by experts, you can redirect your energies. Executives can concentrate on what they do best: innovating, strategizing, and driving core business functions, without the constant looming threat of cyber-attacks.
3. C-Suite Reporting:
Information is power, especially at the executive level. MSPs understand this and, hence, craft detailed, yet concise, reports tailored for the C-suite. These reports distill complex security metrics into actionable insights, enabling executives to make informed decisions, gauge risk factors, and allocate resources effectively.
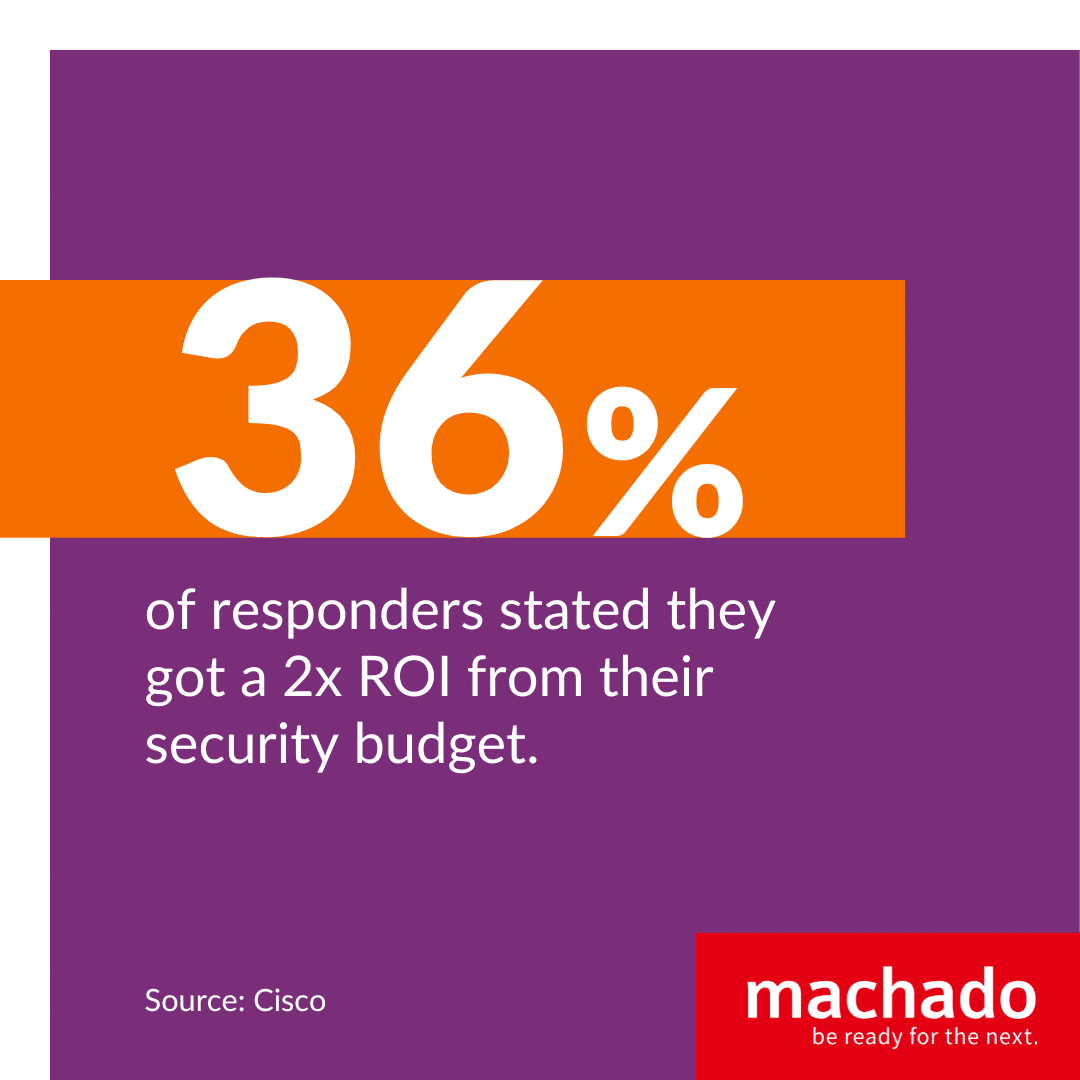
4. ROI on Security:
Financial prudence in IT spending is a delicate balance. MSPs provide a solution by meticulously optimizing the security infrastructure. Infact, 36% of responders to this report stated they got a 2x ROI from their security budget.This ensures that companies get the maximum bang for their buck, deploying state-of-the-art security without unnecessary redundancies or overlaps.
5. Cyber Insurance Optimization:
As Cybersecurity threats grow, so does the market for cyber insurance. Engaging with an MSP can provide an edge here. By meeting and often exceeding the stringent criteria required for Cybersecurity insurance, MSPs can play a pivotal role in not just securing a policy but potentially driving down premiums. This creates a financial incentive for businesses, making Cybersecurity both a protective and economically prudent choice.
With a comprehensive understanding of the intrinsic role of server data, the myriad threats looming large, the limitations of reactive IT defenses, and the tangible advantages of collaborating with MSPs, it’s pivotal to reflect on the broader implications for businesses in this digital age.
The Proactive Approach: Safeguarding Your Organization’s Future
Powerful Cybersecurity is not just about repelling threats—it’s about ensuring the sustained growth and viability of an organization. As we’ve dissected, server data stands as the lifeblood of modern operations, and its protection goes hand-in-hand with the trust stakeholders place in a business.
Choosing a proactive Managed Service Provider is not a mere IT decision; it’s a strategic move that resonates with an organization’s commitment to excellence, diligence, and foresight. By aligning with experts who continuously monitor, innovate, and anticipate challenges, businesses not only secure their present but also chart out a resilient path for the future.
As the complexities of server data protection grow, so should our defenses. It’s time to think ahead, prioritize Cybersecurity, and embrace the unparalleled expertise of proactive MSPs. Machado is here to guide, protect, and optimize, ensuring that your organization not only survives but thrives. Reach out to us, and let us help you be ready for the next.
Download our guide to learn how you can get more done with your current IT staff.Be Ready for the Next IT Opportunity