Originally published in 2022, this article on PHI & PII has been updated for 2024.
When it comes to understanding the value of the data your business manages, there are two types of information that are most prized by cybercriminals: PHI & PII. Protected Healthcare Information (PHI) and Personal Identifiable Information data are especially prone to hackers and fraud because they bring big money to cybercriminals.
Let’s start with PII. This data is considered public because it’s available from public sources such as social media, websites, and directories. Some examples are a person’s full name, home address, or telephone number. However, it can become sensitive PII, depending on the circumstances.
Sensitive PII is protected data that your organization must defend against cybersecurity threats. It includes data that can be used alone or in combination to determine an individual’s identity, such as the following:
- Bank Accounts
- Social Security Cards
- Credit Cards
- Passports
- Driver Licenses
When it comes to PHI, this is considered private data and can include personal health information such as insurance details, medical information, and biometric data. For the healthcare industry, protected data also includes an individual’s healthcare information. The protected healthcare information (PHI) is defined under HIPAA’s Privacy Rules. PHI may include:
- Patient names, addresses, telephone numbers, and email addresses
- Identifying numbers such as Social Security, Medical Record identifiers, or Medicare Cards
- Insurance numbers and beneficiary data
- Medical device numbers, vehicle registration, and digital identifiers
- Biometric data and facial images
With both PHI & PII, context is the defining element. If stored data has the potential to identify an individual, it must be protected. According to a 2022 study, a health record can have up to 18 identifiers that can be sold individually or packaged into an “identity kit.” 
From these ID kits, criminals can engage in illegal immigration, social engineering, and identity theft. Some hackers use the information to blackmail individuals.
Data Durability & Data Diversity
Hackers have a small window to use a stolen credit card. People will quickly cancel their cards if they see unauthorized activity. Some card issuers have fraud detection capabilities that block transactions before the cardholder knows the number was stolen. The added protection shortens the life cycle of a stolen card.
Stolen healthcare records contain multiple identifiers that do not change quickly. Insurance numbers, birthdates, and social security numbers don’t change. The data durability gives criminals time to use the data without detection. 
For cybercriminals, targeting healthcare providers and insurance companies makes business sense. With the same amount of effort, they can steal data that provides a greater return on their time investment than a breach of credit card numbers.
What is the Cybersecurity Landscape in Healthcare?
Cybersecurity attacks increased 31% from 2020 to 2021 with 43% of those attacks directed at small to mid-sized businesses. Although manufacturing supply chains were the primary target in 2021, healthcare remained among the top three targeted industries. 
- East Tennessee Children’s Hospital experienced a service disruption on March 13, 2022, that closed X-Ray services and forced the rescheduling of appointments. As of March 21, 2022, the facility was still experiencing IT security issues.
- Taylor Regional Hospital in Kentucky experienced a service disruption beginning in January 2022. The hospital confirmed that a cyber incident began in November 2021 and continued through January 2022, culminating in a week-long disruption.
The impact of the Tennessee incident is unknown. However, Taylor Hospital in Kentucky found a bad actor obtained protected patient information. The hospital has notified all impacted individuals. Other cyberattacks in the healthcare sector involve tactics such as:
- Email Breach. Catholic Hospice determined that three employee accounts were compromised in December 2021, exposing protected health information.
- Data Breach. Priority Health reported unauthorized access to accounts through its member portal.
- Malware. Cross Timbers Health Clinics reported a malware incident that exposed protected health information and a denial of service.
Given the increase in cyberattacks, it’s only a matter of time before your facility becomes a target.
What Does a Data Breach Cost?
IBM’s 2021 Cost of a Data Breach Report placed healthcare breaches as the most expensive with an average cost of $9.23 million. According to the report, costs can be divided into four categories:
- Detection and Escalation
- Notification
- Business Loss
- Post Response
Loss of business was 38% of the total cost, followed by detection and escalation at 29% and post response at 27%. Notification was only 6% of the overall cost. 
Notification costs come from preparing and distributing information. They also include costs associated with determining regulatory requirements and contacting the appropriate agencies. You may have to hire third parties to help with containment and assessment. Then you need to understand that there will be a loss of business, the most costly of all categories. It encompasses revenue losses due to disruption of service and downtime. The report attempts to quantify the cost of losing customers and acquiring new ones. For healthcare, that cost is significantly impacted by reputation loss and community standing. The impact on a healthcare facility’s reputation can be long-ranging.
The post-response category includes regulatory fines and recertification of compliance. It may include added public relations costs. In some cases, the percentage may be higher depending on the size of the fines and penalties.
Although HIPAA is the first regulation that comes to mind in a healthcare breach, PCI-DSS regulations may apply if the facility accepts credit card payments. Dual regulatory penalties and fines can significantly increase post-response costs.
What Compliance Penalties and Fines Apply?
Penalties and fines for HIPAA violations can range from $120.00 to several million. The amount depends on which tier the violation falls under. HIPAA violations can be classified as civil or criminal.
Criminal
HIPAA violations are considered criminal if an individual or organization benefited from the information. If they profited from the information, they may be required to refund all financial gains as well as pay a fine. Based on the tier, a violator may serve jail time, up to a maximum of ten years.
Civil
Civil violations are the most common, but healthcare providers have witnessed an uptick in criminal actions by employees. For a civil violation, financial penalties or fines are based on tiers as shown in the following table: 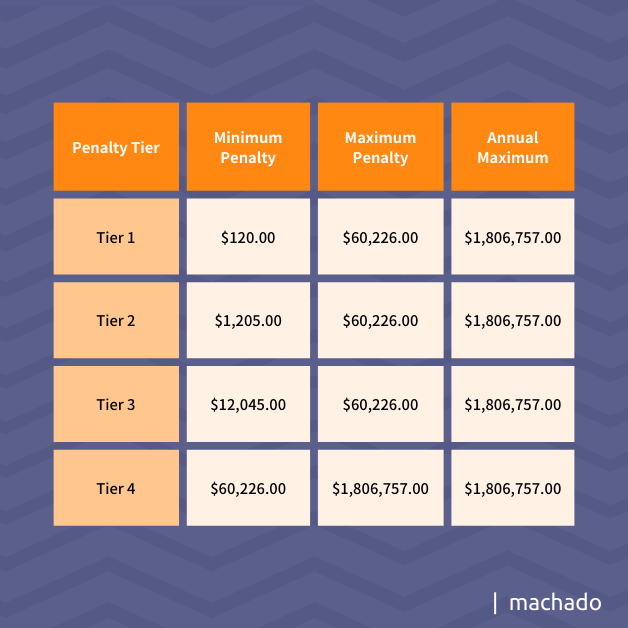
PCI
If your business signed an agreement to accept VISA, MasterCard, or American Express as a form of payment, you have agreed to comply with the PCI-DSS regulations. That includes the fines and penalties that may be levied in case of a security breach.
Non-Compliant
Non-compliant companies can expect fines based on the number of months it takes to bring them into compliance. For example, it takes your business between one and three months to become compliant. You will be fined between $5,000 and $10,000 per month until you are certified as compliant.
The cost increases the longer it takes your business to become compliant. The fine increases to $25,000 per month if it takes four to six months to be certified with the option of increasing the monthly fine to $50,000 per month. If it takes more than six months, the fine increases from a minimum of $50,000 per month to $100,000. During the non-compliance period, no credit card payments can be accepted.
Compliant
Your business can be fined even if it is in compliance. The penalty is usually a per record fine of $50.00 to $90.00 for each compromised record. Your contract with a payment processor may be terminated, and your business will most likely be audited. If an area of non-compliance is found during an audit, the penalty may be as high as $500,000.
Now that you know more about PHI & PII, and how valuable this data is, let’s review some recommendations and best practices to protect your business from hackers.
5 Best Practices to Protect Your PHI & PII
As cyberattacks increase, the odds of becoming a victim increase as well. The National Institute of Standards and Technology (NIST) issued guidelines in 2010 to help organizations protect individuals’ data privacy. You need to:
1. Identify Your Data
Before you can protect PHI and PII, you have to know what you have and where it’s located. You will also need to know how it is stored. Is it encrypted while at rest?
To do this, conduct a full audit of your data storage capabilities. This usually includes your full network, as data can reside in multiple places (and beyond the typical deep analysis, we offer a free dark web scan for businesses).
2. Classify Your Information & Minimize Your Stored Data
Once you identify your stored data, evaluate its potential impact on an individual should it be breached or stolen. Determine if the separation of data elements reduces the risk and minimizes the impact.
Your computers prefer to store an entire record rather than a few elements. As a result, your company may store more data than you need because it’s faster and easier. Existing processes should be reviewed to ensure that only a minimal amount of data is retained.
Removing data should be controlled. Storage devices need to remove all stored data. If the hard drive or a flash drive is being removed, be sure a special erasing program is used to ensure the data is erased before disposing of the device. The same process applies to devices that are being repurposed within your business.
3. Restrict Access
Multi-Factor Authentication (MFA) should be used to reduce the odds of unauthorized access to your business’s data. Adopt a least-privilege model for user access. This model sets controls on a per-user basis, so individuals cannot have access to areas that are outside their daily duties.
4. Have a Plan
Your business needs a plan that defines how you plan to create a robust security program throughout your organization. It should include what equipment, software, and technologies are needed to ensure strong cyber defenses. Part of your plan should include how to respond to a possible cyberattack. Time is crucial when trying to contain an attack, so you need to know what to do from the minute a breach is suspected. While creating such a plan might seem overwhelming depending on the size of your IT department, this is where a trusted partner with expertise in cybersecurity can help your business.
5. Talk to Experts
With the increase in cyberattacks and the growing complexity of defending against them, your business may benefit from talking to a managed services provider that is also a cybersecurity expert who can help you plan and protect your sensitive data. Key parts of your plans should include assessments like a cybersecurity audit, server health checks, and network assessment.
Contact us today to learn about the benefits of working with a trusted cybersecurity partner.





