Successful cyberattacks that hold companies hostage for millions of dollars may receive extensive media coverage, but they are no longer the primary target for most hackers. It takes significant resources and time for cybercriminals to successfully breach the security defenses of large corporations. It’s faster to compromise soft targets with fewer resources. This is why the FBI is sharing that small businesses need cybersecurity. Your business is a new and growing target for cyber attacks.
Cybercrime is a business, and like any business, it looks at its return on investment. If hackers can compromise ten systems in five days for half a million dollars of marketable data, they could net about $26 million in 52 weeks and have weekends off.
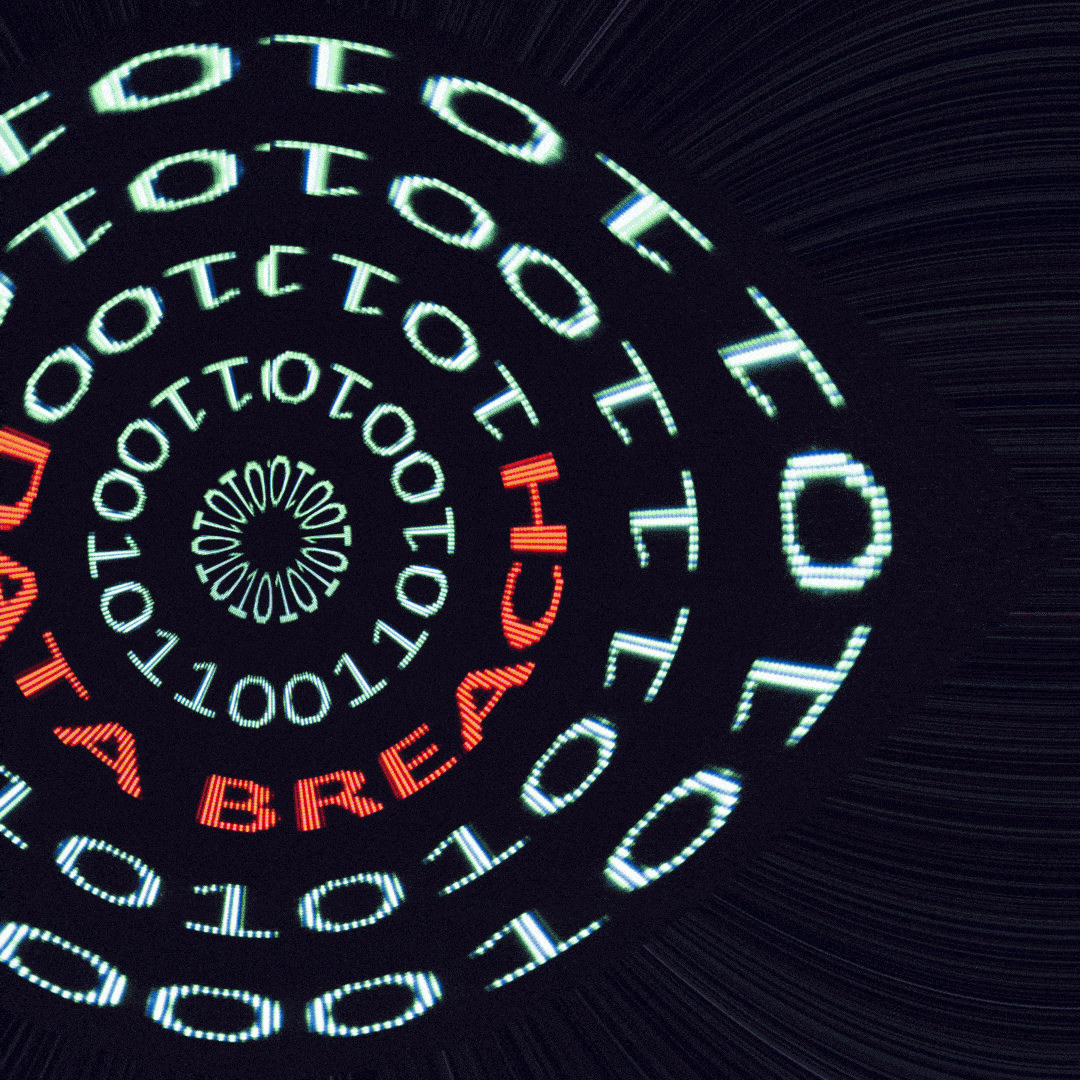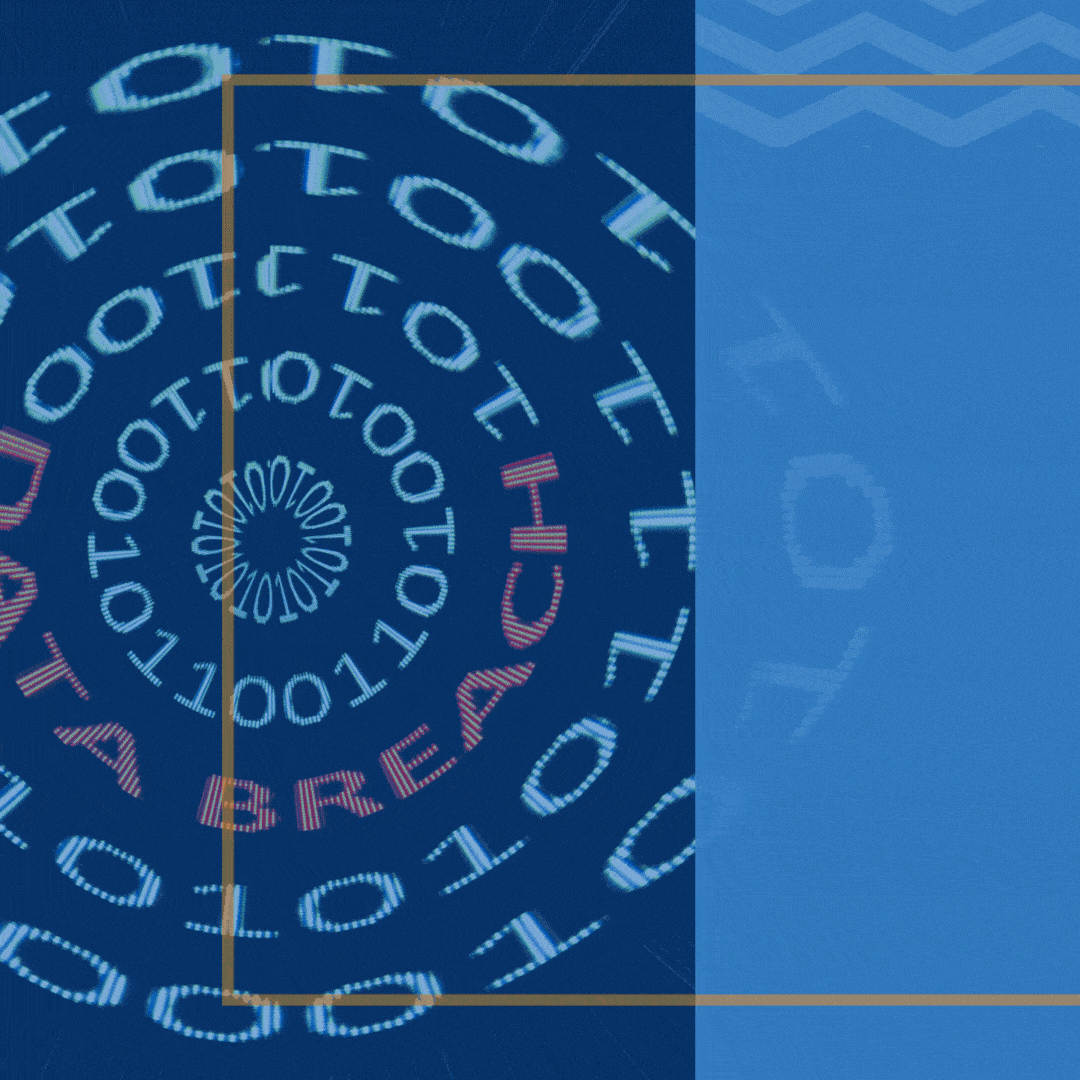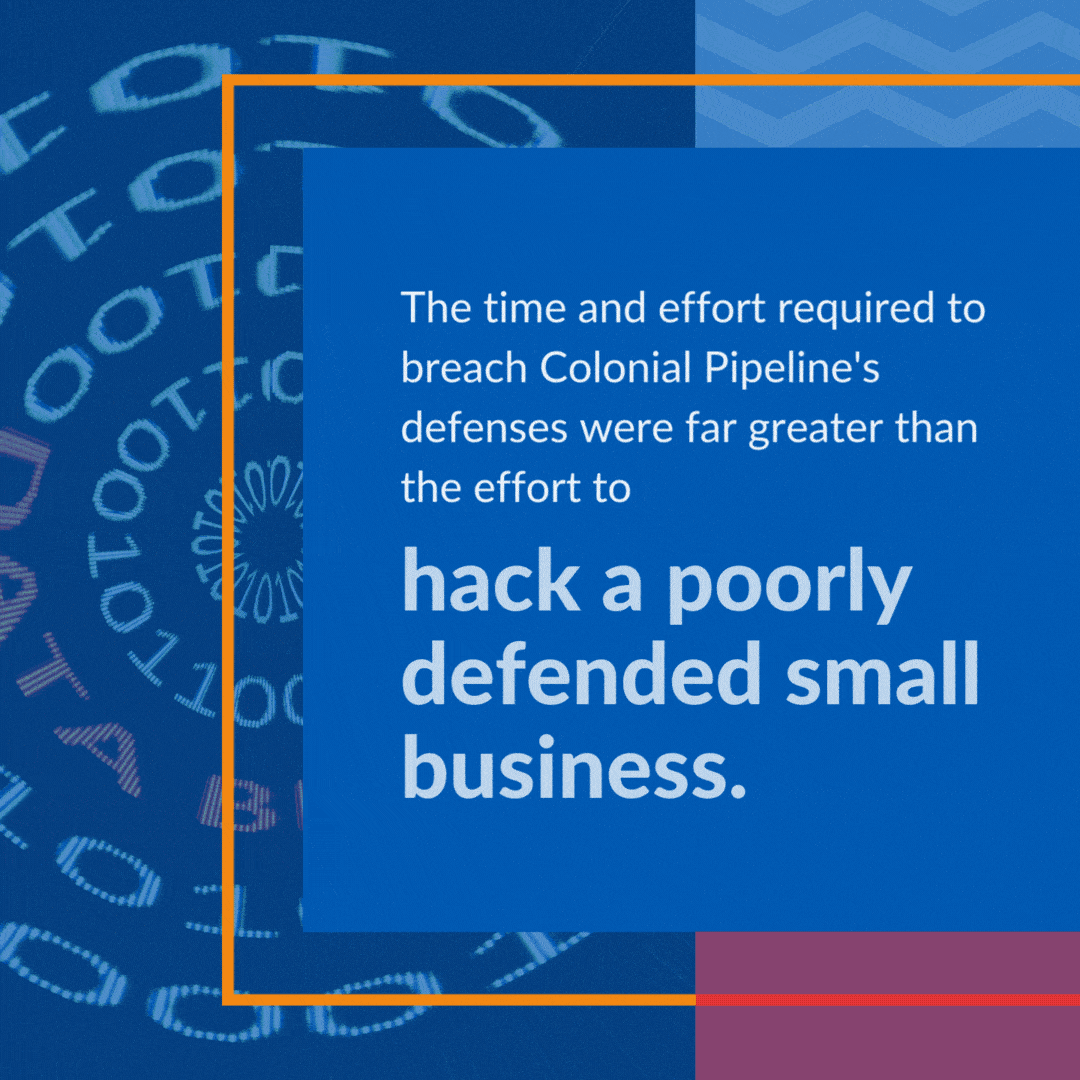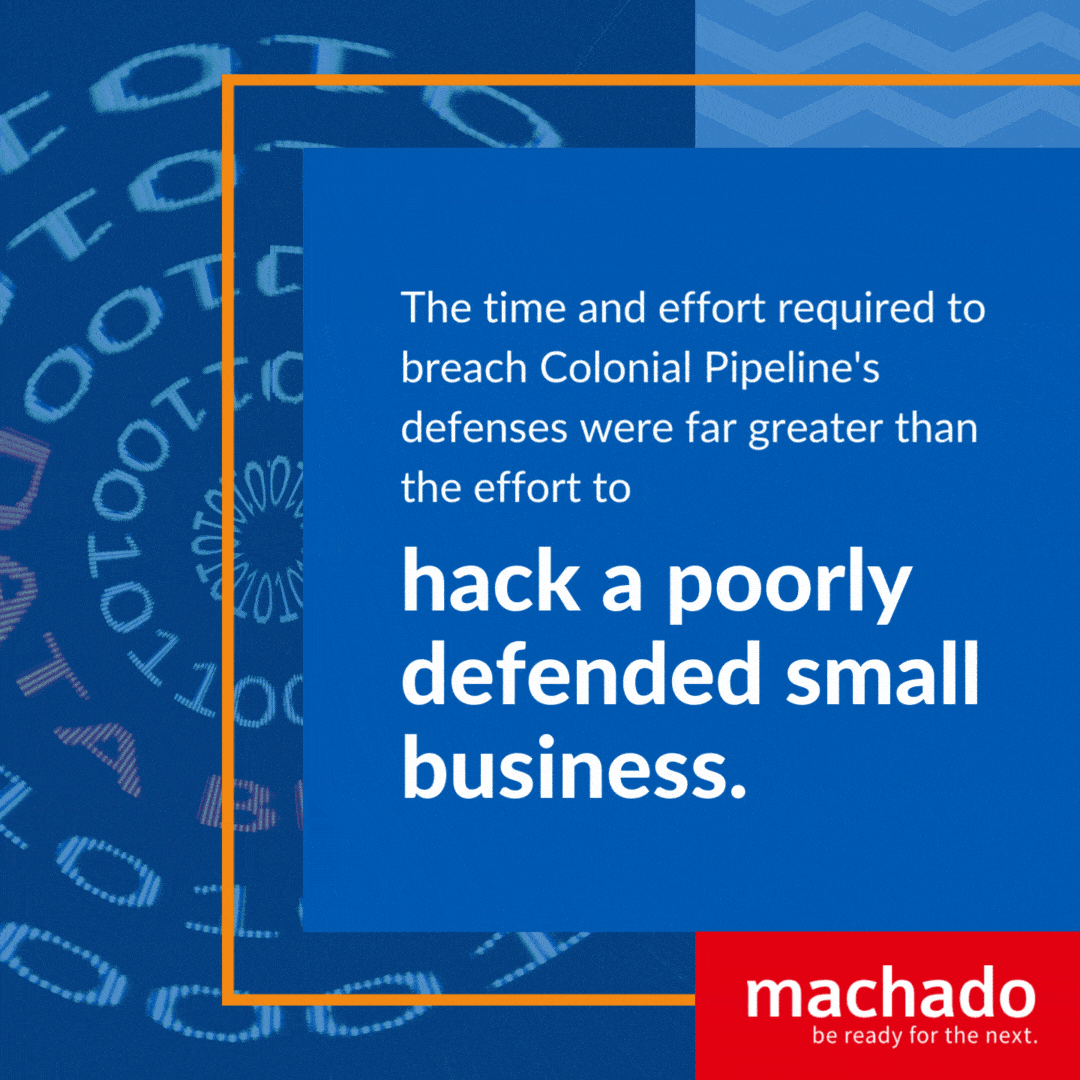
Take for example, the Colonial Pipeline hack. The company paid $4.4 million to the hackers, who netted even less because $2.3 million was eventually recovered. The time and effort required to breach Colonial Pipeline’s defenses were far greater than the effort to hack a poorly defended small business. This is why small businesses are targeted more than ever now.
Why Are Small Businesses Targeted?
According to the FBI, 2021 saw a 64% increase in financial losses because of cyberattacks, resulting in a total loss of $6.9 billion. The majority of those losses were among small and midsized businesses. The FBI Supervisory Special Agent Michael Sohn noted that many of these attacks could have been prevented with proper cyber hygiene.
Verizon’s 2022 Data Breach Investigation Report (DBIR) found that small businesses reported 2,065 incidents, while large corporations with over 1,000 employees reported 636. Actual data breaches totaled 715 for small businesses and 255 for large organizations. Small businesses were over three times more likely to experience a cyber incident than large companies.
The 2022 DBIR is the 15th report published by Verizon, but it is the first report that includes a special section on very small businesses (less than ten employees). They included the section to help small businesses from becoming a target through better security practices.
The researchers found that very small organizations lack “security professionals and cutting-edge technology to defend themselves.” And, they have limited resources to counter aggressive cybercriminals. In 2022, very small businesses had 832 incidents and 130 confirmed breaches.
As part of their report, the Verizon team listed the following tips for protecting a small business. These recommendations are basic to good cyber hygiene that every organization should practice:
- Use multi-factor authentication (MFA).
- Do not share or reuse passwords.
- Use a password manager.
- Change default credentials on all devices, including payment terminals.
- Install software updates promptly.
- Ensure vendors are practicing good cyber hygiene
- Perform scheduled backups.
- Confirm that all firewalls are turned on.
- Encrypt protected data.
- Use antivirus software.
- Restrict administrator accounts.
- Do not click on unsolicited texts or emails.
As a small business owner, how many of these recommendations are in place for your business? To help you out, let’s take a closer look at good cyber hygiene practices.
Download our free guide on staying protected from ransomware.Be Ready for the Next Cyberattack
What is Cyber Hygiene?
Cyber Hygiene involves basic practices that your business should perform to reduce your overall cyber threat exposure. They range from password management to email services. Let’s look at the 11 fundamental steps highlighted in the 2022 Verizon DBIR to improve your cybersecurity defenses.
1. Deploy Multi-Factor Authentication (MFA)
Many companies still require a username and password to authenticate a user; however, using multi-factor authentication requires additional information, making it more difficult for unauthorized people to gain access. For example, after a username and password are authenticated, the user could be required to enter a code sent to their cell phone.
The reasoning behind MFA is a hacker may steal employee credentials but won’t have access to their smartphones. Since half of all cyberattacks begin with stolen credentials, you can eliminate one of the primary pathways to a system compromise by deploying MFA.
2. Manage Your Passwords
Employees know that passwords protect against unauthorized access. They also understand what makes a strong password. The issue really isn’t with passwords. It’s with remembering them.
As a small business owner, invest in a password manager for your employees. With a manager, your employees don’t need to remember their passwords. That increases the odds that they will create stronger passwords.
3.Change Your Default Passwords
Devices come with passwords. Whether a printer or a payment terminal, devices connected to your network use default passwords such as password or 12345678 unless you change them. Failing to change default passwords is like leaving your door key under the welcome mat. It’s the first place a criminal looks when trying to break into a business or home.
Be sure your security policy includes a procedure for establishing and recording device-level passwords. Again, a password manager for company assets is a good place to keep the information.
4. Update Your Software Promptly
Software updates were once known as “patches.” These patches were incremental software changes, usually to create a flaw in the software. Whether an update or a patch, software fixes need to be installed as promptly as possible.
Many software updates include security-related corrections. When the updates are not applied promptly, you leave a vulnerability in place for hackers to exploit. For example, Microsoft Exchange Server had a known vulnerability that was patched shortly after its release in 1996. Microsoft issued security updates to correct the vulnerability in 2010, 2013, 2016, and 2019 releases of Exchange Server.
In 2021, China took advantage of that vulnerability, attacking many government agencies and infrastructure businesses that had not applied the update. If you do not have an update policy that stipulates how and when software patches should be applied, your business needs one to ensure it’s not caught unprepared.
5. Establish Vendor Security
As a small business, you are part of a supply chain that needs to be secured. As part of that process, you should confirm that your suppliers or vendors are practicing good cyber hygiene as well. A poorly defended supply chain means cybercriminals can enter the network at any point and have access to multiple companies in the chain.
Even an incident, which is only an attempt, can cost your business. In 2021, SMBs lost $212,000 because of suppliers. In these incidents, the small business shared data with suppliers and suffered financially when the vendor was attacked. The cost could have been much higher if the incident had been a breach.
6. Schedule Backups
You may back up your data, but how often do you run a full backup, and where is the backup stored? Have you tried to restore from a backup? If not, you may find that restoring from backups is not straightforward. If your business needs to be up and running within hours of a system compromise or natural disaster, you want to know before disaster strikes that you can meet the timeline.
The frequency of your data changes determines how often you should back up your system. You may need to do full backups weekly, but daily incremental backups may be enough to protect your data. Whether full or incremental, be sure to make two copies of a backup.
One backup copy is not enough, especially if it is stored on the same network as the production system. Cybercriminals look for backups before they start a ransomware attack and encrypt them along with the production system. You can leave one copy on the network in case you need it to restore files but store a second offsite.
The second copy should be stored in a location that is not connected to the internet. Without a connection, the information cannot be compromised. If you haven’t tried to restore your backups, now is an excellent time to test the process. It’s better to find a problem before you need to restore the data.
7. Check Your Firewalls
Firewalls are an essential component of any cybersecurity framework. Many devices have firewalls built in, but not all set the default to on. Part of a security policy should include checking that firewalls are on.
Your small business should also have a record of the firewall settings for the network firewall. You may not have been the one who set up the firewall, so knowing the configuration is essential to maintaining a secure network. Restricting access to the firewall is also necessary to prevent unauthorized changes from being made.
8. Encrypt Your Data
Depending on your industry, you may need to encrypt stored data to comply with cybersecurity regulations. Professional services such as attorneys or accountants hold data that can be used to identify an individual. This protected data needs to be encrypted or stored so that a person’s identity can’t be compromised.
If your business accepts credit or debit card payments, cardholder data must be encrypted if stored locally. The encryption minimizes the risk of a security breach that results in significant fines and penalties.
9. Use Antivirus Software
When was your antivirus software purchased? Does it receive regular updates? Hackers are continually developing new viruses. If your software does not receive regular updates, it can’t protect against viruses. The software should be able to check email attachments and remove cybersecurity threats immediately.
10. Restrict Your Administrator Accounts
Admin accounts give individuals access to everything on a device or network. If you or an employee is responsible for adding and deleting users or password management, do not use the admin account for regular activities. If hackers were to compromise an admin account credentials, they would have complete control of your digital assets and business operations.
Create a separate account for routine tasks such as answering emails, uploading documents, and searching the web. That way, stolen credentials are valid only for the user account. Admin accounts should only be used for managing the system.
11. Pay Attention to Email
Hackers love email. They use it to download infected software to company computers. They can send you to malicious websites and impersonate companies or individuals. Business email compromise (BEC) is an email-based scam that tricks the recipient into transferring money to a bogus account that the hackers have opened.
In 2019, hackers compromised a parish email. They used those credentials to monitor operations until they found a construction company that received payment via wires. They waited until a payment was made and then contacted the parish to say the payment was not received. The hackers gave them new payment information, and the invoice was paid a second time, resulting in a loss of $1.5 million. The parish was located in a small town with a population of 35,000.
Whether a profit or nonprofit organization, you need a process for verifying financial transactions. It’s also important to train your staff (and offer refresher courses) to think before they reply to an email or click a link.
Why Small Businesses Need Cybersecurity
As cybercriminals pivot away from large corporations, their focus shifts to small and midsized businesses because they assume you are under-protected. Don’t let your business be a soft target that requires minimal effort to compromise.
You can reduce your odds of being hacked by implementing cyber hygiene practices to reduce cybersecurity threats. Once you review the checklist above, you may realize that protecting your business will require more resources than you actually have available today and that having your staff work on cybersecurity will take away from your business operations.
Download our free guide on staying protected from ransomware.Be Ready for the Next Cyberattack
This is where a Managed Service Provider can help you. Let’s talk! Working with a team that understands the ins and outs of small businesses, as well as your unique needs will save you from sleepless nights worrying about the security of your data.