In 2020, dramatic shifts in how businesses operated drove changes in network infrastructure for both large and small companies. As you probably experienced, many of these changes took place without adequate analysis of security impacts because they needed to happen so quickly. This shift continued into 2021 as your IT infrastructure had to accommodate a hybrid environment. This resulted in traditional IT activities, such as the importance of server health checks and the need to backup your data, possibly not staying top of mind.
This year, your focus should be on updating your overall IT policies, including data backup requirements, to address the 2022 cybersecurity trends we are already starting to see. You need to ensure your policies and processes have been adjusted to address more sophisticated attacks tied to phishing and ransomware, as well as an increased interest from nation-states to hack your infrastructure. Most of all you need to perform cybersecurity and server health checks to verify your overall security posture. Here are the cybersecurity trends you should prepare for this year:
1. Disinformation Campaigns
If you’re outside the cybersecurity realm, misinformation doesn’t equate to cyber crime. How can reading fake news increase the risk of a cyber attack? According to a European think tank, cyber criminals exploit the same distribution channels, use similar tools, and target the same victims. Just as cyberattacks can be conducted by paid professionals, disinformation campaigns often rely on those same people to distribute false data.
Social media platforms increase the range of disinformation distribution. Cyber criminals leverage those channels to promote malicious websites containing malware. They feed into the fear and anxiety that people share to leverage an attack. For example, the pandemic saw an increase in the number of Covid-related websites that used baseless claims to drive traffic. Once viewers were on the site, hackers could download malicious software onto networks and mobile devices.
Disinformation opens more promising channels for cyber criminals. These criminals exploit people’s fears and tap into conspiracy-based sites to expand their potential targets. Whether the outcome is compromised network security or a damaged reputation, these criminals/influencers receive financial rewards for their efforts.
2. Supply Chains Disrupted
It was predicted early that supply chain attacks would be four times higher in 2021 than in 2020. Of the supply chain attacks between January 2020 and July 2021, 50% were attributed to advanced persistent threat (APT) groups. APT groups are individuals who use sophisticated hacking techniques to maintain continuous and clandestine access to a computer network or system. APTs are designed to remain undetected for extended periods.
Because of the complexity of APT attacks, most groups are often backed by nation-states or large organizations wanting access to critical information. The remaining 50% of supply chain attacks target smaller infrastructures and are financially motivated. These smaller attacks are more likely to gain access to deploy ransomware than to remain hidden.
Supply chain attacks look for the most vulnerable organization within a given supply chain. For example, healthcare systems must store all medical records in a government-defined format for rapid exchange of digitized information. Whether it is a large urban hospital or a small private practice, any entity keeping patient information must have the ability to transfer digitized records, electronically.
That requirement opens the door to cyber attacks. A recent article found that 73% of healthcare compromises were initiated within provider organizations – 187% increase over 2020. No supply chain is immune. Cybercriminals are always looking for the weakest link as a stepping stone to a larger compromise.
No matter the industry, companies need to assess their supply chain infrastructure to ensure all points are well-protected. For those in highly regulated industries, inadequate measures can impact cybersecurity compliance, resulting in financial fines and penalties. (We’ll link back to the other January blog here)
3. More Data Breaches
According to a report published in October 2021, the number of data breaches from January through September was greater than the total number of breaches in 2020. The researchers expect data breaches to increase in number and size in 2022. Phishing and ransomware will continue to be the dominant threat vectors for data breaches.
IBM and the Ponemon Institute’s annual data breach report found that remote work and length of attack were contributing factors to the overall costs. Because of the rapid pivot to remote workplaces, many organizations were ill-prepared when it came to establishing secure remote work environments. As a result, those companies paid a premium. On average, companies with remote workers paid $1 million more than those that did not.
The report also indicated that companies took an average of 287 days to detect and contain a data breach. That is seven days longer than in 2020. Companies that were able to detect and contain the breach in less than 200 days paid $1 million less in costs than those taking longer.
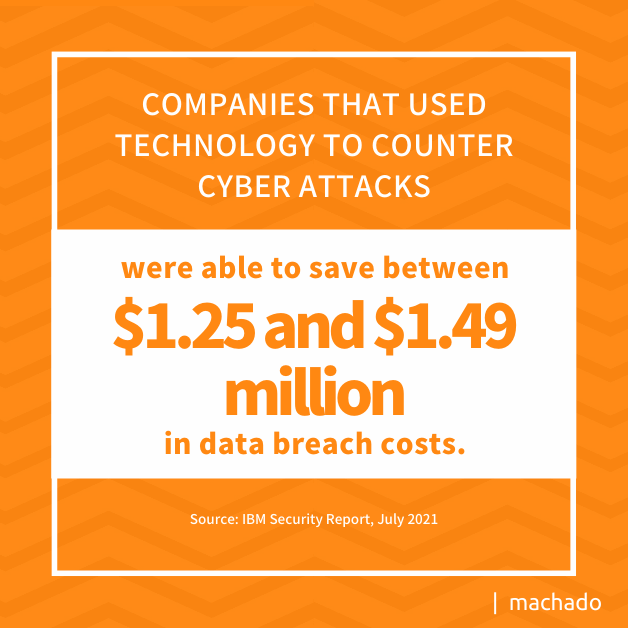
Countering these cyberattacks requires technology. Companies that used artificial intelligence, security analytics and encryption were able to reduce the cost of a breach. Companies that used technology to counter cyber attacks were able to save between $1.25 and $1.49 million in data breach costs.
4. Mobile Devices Targeted
Checkpoint’s 2021 report on mobile security noted the following:
- Mobile devices have become another entry point into a company’s network. With the rise in distributed workforces, more personal devices are being used for business purposes, making for an increased attack surface.
- Cyber criminals deploy new apps promising help or information on Covid as a means to place malware on a smartphone. Of the organizations surveyed, 46% had at least one employee download a malicious mobile application.
- Vulnerabilities exist in mobile devices that are not being addressed.
- Given the growing number of remote or mobile devices, many organizations use mobile device management (MDM) systems to help administer their networks. These systems are prime targets for cyber criminals. Breaching MDM systems enable hackers to distribute malware to all connected devices.
It’s important to know that ransomware is mobile. Black Rose Lucy has haunted Android devices since 2018. In its original form, the malware was used to extract information, but recent changes to the botnet have given it ransomware capabilities. The software resides in a video player app and when downloaded generates a ransom request. As you head into 2022, you need to conduct a cybersecurity audit of mobile devices that access your network.
5. Cloud Attacks Increase
Deploying cloud-based applications became a necessity as people continued to work remotely, but it didn’t take long before cyberattacks on cloud services increased. If cloud security is not properly maintained, cybercriminals can easily compromise a network. The Capital One data breach of 2019 happened because of a misconfigured firewall. The hacker stole 106 million financial records and the breach cost Capital One about $300 million. It’s important to conduct cybersecurity health checks whenever configuration changes are made to verify that the security policies are still in effect.
Breaching the cloud is no different from attacking an on-premise server. Hackers need usernames and passwords. With legitimate credentials, hackers can move throughout a network undetected because they appear to be authorized users.
Non-standard work hours add to the complexity of detecting unauthorized use. With more employees working from home, their hours don’t always fall within the standard workday. That makes it difficult for your IT department to establish baselines that can be used to detect unusual behavior.
Giving hackers the opportunity to meander through a network undetected allows them to learn about your company policies and key personnel. They use that information to create more realistic phishing attacks. Cyber criminals can also use that time to learn network configurations or plant backdoors that give them access after they’ve been detected.
6. Phishing Attacks Continue
Phishing is still a leading threat vector. In January 2021, there were almost 250,000 phishing attacks. This is an unprecedented number for only one month. Although many were contained, companies had to expend resources to thwart the attacks, burdening overworked IT staff. According to IBM, 33% of cyber attacks begin with phishing. So, why is phishing such a persistent threat? 
- Sophistication of attacks.
- Move to mobile.
- Ineffective training.
The so-called “white hats” of cybersecurity have a difficult time keeping up with the technology bad actors deploy. Their techniques have become more sophisticated and hackers have addressed weaknesses that help organizations identify possible attacks. Training employees has had limited results. With the threat landscape changing quickly and the sophistication of the attacks increasing, it’s difficult to keep employees informed on every latest threat.
Sophistication
Attacks are targeting email inboxes across an enterprise to gain a better understanding of the landscape. Cyber criminals scour the emails, looking for names and addresses of key personnel. They learn what information is being sent and received so they can create more convincing phishing emails from which to launch a ransomware attack.
Mobile Devices
Bad actors are moving away from servers and towards mobile endpoints. As mentioned earlier, mobile devices do not have the same level of security and may present vulnerabilities that can be exploited. More sophisticated scams such as downloading bogus apps open the way for ransomware to be inserted into a network.
Ineffective Training
The traditional methods of identifying and avoiding phishing attempts no longer work. Cyber criminals are better at covering their tracks, making it harder for attempts to be detected. Trying to keep employees trained on the changing cyber threats is virtually impossible, since most organizations have failed to fully train their staff on existing threats.
7. Ransomware Expands
The financial sector has long complained of the unregulated activities of cryptocurrencies such as Bitcoin. These digital currencies verify and record transactions using cryptography. The records are maintained in a distributed system making it difficult to tie account holders to accounts.
Because of its anonymity, cryptocurrency has become the payment mechanism of choice for cyber criminals. Most ransomware attacks require payment in Bitcoin. Without financial instruments such as Bitcoin, criminals would have difficulty shielding their funds from regulators. They would leave a money trail that could result in prosecution.
Although ransomware attacks existed before cryptocurrency, the attacks could not have reached the current scale without digital currencies. Companies such as Bitcoin provide the perfect mechanism for moving funds across borders and outside the regulated financial sector. Without a money trail, it is difficult to find and prosecute hackers.
Ransomware is a lucrative enterprise. It will continue to scale as long as a mechanism exists for protecting payments from outside scrutiny. Regulating cryptocurrencies may slow ransomware deployments, but it will not stop them. That’s why you must continue to back up your data to an offsite location. With backups in place, companies do not have to pay to get control of their data, making ransomware a less appealing threat.
8. Nation-State Threats Rise
Microsoft’s 2021 Digital Defense Report (MDDR) showed an increase in the number of nation-state activities over the last three years with a total of 20,500 nation-state notifications (NSN) being issued. An NSN notifies an organization or individual that a nation-state has targeted or compromised their infrastructure. Based on their analysis, the MDDR states that nation-state attacks focused on espionage and intelligence gathering rather than destructive attacks.
For example, the People’s Republic of China launched an attack on organizations with an on-premise installation of Microsoft’s Exchange Server. They identified a vulnerability and exploited it to extract information on industry sectors such as infectious disease research, law firms, higher education, defense contractors, and think tanks. Some cybersecurity experts believe that China has stolen enough information to have a dossier on every American.
How is Your 2022 Cybersecurity Readiness?
Whether through server health checks or cybersecurity audits, you need to be confident of your security posture in 2022. You should check your backup processes to ensure critical data is being stored offsite. Why should you back up your data if you continue to store it onsite? If a hacker can compromise your network, they also have access to your backups.
The upcoming year is positioned to deliver more sophisticated attacks from larger organizations and nation-states. Let’s discuss how working with Machado Consulting can help you be confident with your cybersecurity preparedness.