While it’s important to pay attention to the latest cybersecurity threats that can impact your IT infrastructure from the outside, it’s critical you also keep an eye on potential internal IT threats to your business.An often overlooked focus of an organization’s overall cybersecurity plan is the real issue of insider threats. Whether accidental or intentional, internal IT threats can be more prevalent and costly than external cybersecurity threats.
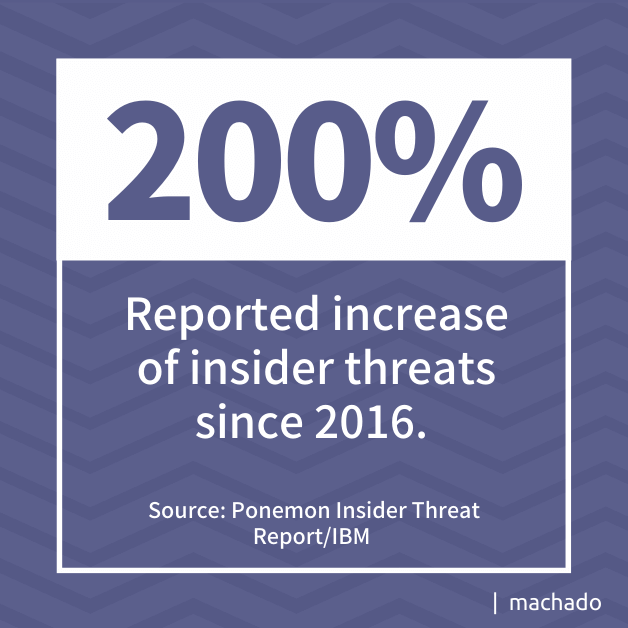
A 2020 IBM report on insider threats indicated a 200% increase in insider threats since 2016. The report categorized the threats into the following groups:
- Internal negligence. This group refers to employees, contractors, or authorized third parties accessing an organization’s network. These threats exist because insiders fail to follow or implement security best practices.
- Malicious intent. Individuals in this grouping purposely try to sabotage a network for financial gain or damage a company’s operations or reputation.
- Credential theft. Employees steal or allow third parties to gain access to privileged credentials for nefarious purposes.
Over 63% of insider threats came from internal negligence, with the remaining categories making up 37%. Although insider attacks are responsible for less than 50% of all cyberattacks, they cause over 80% of all data breaches. Here are five things for you to know about insider attacks to strengthen your cybersecurity preparedness.
1. What is the Cost of Insider Attack?
The cost of an insider attack depends on the size of the organization. Businesses with less than 500 employees averaged $7 million per attack. Corporations of 25,000 to 75,000 employees had an average cost of over $17 million. The costs were determined from the following categories:
- Investigation and escalation
- Incident response
- Containment
- Ex-post response
Armed with this information, organizations can strengthen their network security posture against insider attacks.
2. What is an Insider Attack?
The Cyber and Infrastructure Security Agency (CISA) defines an insider threat as one that occurs when internal entities use their authorized access to harm an organization’s resources, facilities, information, equipment, network, or systems. The internal user may be an unknowing participant in attacks related to:
- Espionage
- Terrorism
- Sabotage
- Leaked Information
- Criminal actions
- Remediation
Each of these internal IT threats have implications beyond the targeted organization and its internal cybersecurity.
Espionage
According to the Intelligence and National Security Alliance (ISNA), economic espionage costs the US 1% to 3% of its annual GDP, which in 2021 was $21 trillion. Nation-states are constantly monitoring government contractors for military intelligence. Foreign and domestic competitors collect data to help bring products to market faster and at a lower cost. Unfortunately, academia has become a target because of its more open sharing of research across disciplines. 
Cyberterrorism
For years, security analysts have struggled to craft a workable definition of cyberterrorism. Beginning in 2000, many organizations started using Dorothy Denning’s definition:
Cyberterrorism is the convergence of cyberspace and terrorism. It refers to unlawful attacks and threats of attacks against computers, networks and the information stored therein when done to intimidate or coerce a government or its people in furtherance of political or social objectives. Further, to qualify as cyberterrorism, an attack should result in violence against persons or property, or at least cause enough harm to generate fear.
Although the US government has not called the Colonial Pipeline attack an act of cyberterrorism, many within the cybersecurity community consider it terrorism. The intent may have been financially motivated, but the result was a Russian-backed disruption in a US supply chain that evoked panic.
Cyberterrorism can be about money and terror. Nation-states can pay hackers to disrupt networks. Or, they partner with criminal groups, letting the bad actors collect the funds but keeping the data. No matter the motivation, cyberterrorism has the potential to have a catastrophic impact on the physical and virtual worlds.
Sabotage
Sabotage is intended to damage or harm a system or data. These inside actors may erase critical information or change access controls to prevent users from performing their jobs. They may release information that can have negative consequences for a business or individuals within the business.
Saboteurs are not looking for financial rewards. Instead, they are looking to damage a business. According to a 2020 survey, 25% of consumers stop doing business with a company that has suffered a cyberattack. Over 66% trust a business less after a data breach. These statistics translate into lost revenue for employers.
Leaked Information
Leaked information does not have to be purposeful. It can happen because an employee sends a sensitive file to the wrong person or individuals get copied on emails that eventually end up in the wrong hands. How often do your employees just forward information without looking at the details? Even the most innocent actions can have adverse results if there’s a lack of employee IT security training.
When information is leaked because an employee is disgruntled, it’s sabotage. If information is stolen and leaked, that’s a crime. Lax security can often result in the inadvertent disclosure of secure data contributing to internal IT threats.
Criminal Activities
When employees have access to sensitive or proprietary information, they may be tempted to steal the data for financial gain. They may facilitate criminal elements by giving them access to a network. Sometimes, insiders attack a system for notoriety. Their goal is to become known within the hacker community as someone with skills.
Contractors or other third parties that have system access can use the permissions to install malware or viruses that damage or disrupt a network. Although you like to think of your employees as trustworthy, it’s important you consider the costs associated with an insider attack to understand the far-reaching impact of an internal compromise.
3. Which Insiders Become Attackers?
The Gartner Group classifies internal IT threats into four categories: pawn, goof, collaborator, and lone wolf. Each group has its identifying characteristics and motivators:
Pawn
Employees who are manipulated into risky security behavior through social engineering as pawns. Pawns are employees who are unaware that emails can be spoofed or that a recommended website may be malicious. As a result, they may be downloading malware from a questionable site or disclosing log-in information.
One of the most costly business email compromise attacks was against Facebook and Google between 2013 and 2015. A Lithuanian hacker created invoices that appeared to be from an Asian manufacturer the companies did business with. Employees did not question the invoices or changes in the payment processing, enabling the hacker to steal $100 million.
Goof
Goofs are ignorant or arrogant users who believe they are exempt from security requirements. They may not see the value in storing proprietary or trademarked data in secure locations or in an encrypted format. They are not intentionally malicious but can cause significant harm by bypassing security measures.
Goofs are not as careful as they should be when it comes to remote access, often using public Wi-Fi to connect to a server. They do not see the value of starting a VPN session to look at their emails quickly. These violations open the door to cyber criminals who are looking for an opportunity to gain access.
Collaborator
Collaborators are internal users who work with a third party to access a network for harmful purposes such as stealing intellectual property or trade secrets. An interesting example is the story about Greg Chung. In the 1970s, he stole trade secrets from the US space program and sent them to China. In 2010, he was sentenced to more than 15 years in prison.
Lone Wolf
Lone wolves are extremely dangerous insiders who have the expertise to cause havoc within an organization. Because they work alone, these insiders can often hide their activities from you.. The most notable example is Edward Snowden who leaked information regarding NSA surveillance activities in 2013-2014.
4. How to Detect Possible Insider Attacks
Researchers have studied insider attacks to learn how trusted employees become a threat. Their studies have identified the steps that take an employee from ideation to execution. Only pawns do not follow these steps. Even goofs go down a similar path because they see no reason to follow protocol.
- Ideation. Thinking about a cyberattack may start with a grievance. Employees may feel underpaid or devalued. Some employees may start wondering if they could accomplish a cyber compromise, while others may have personal concerns such as extreme debt that trigger the idea. For goofs, it’s most likely that they don’t think the rules apply or find them unnecessary.
- Preparation. Individuals begin researching the idea and may develop a plan. If they need training, materials, or equipment, they may start collecting the required items or expertise. In some instances, goofs will prepare a justification for violating policies.
- Exploration. Depending on the insider category, employees may look for like-minded people to recruit. External bad actors may attempt to recruit susceptible individuals from within an organization using social engineering.
- Experimentation. At this point, insiders are testing their plan. They may perform cyber surveillance to identify possible defense mechanisms.
- Execution. Bad actors exploit their position to execute an insider attack.
- Exfiltration. Individuals attempt to escape, evade detection, or hide their involvement.
While traveling this path, most insiders will exhibit behaviors that might indicate a possible threat. These changes may be the result of personal or organizational triggers.
Personal
For example, individuals who are upset with their employer can become angry and contemplate revenge. Employees may have addiction or financial problems that require additional income. Sometimes, people enter or remain in toxic relationships that allow for manipulation and encourage risky behaviors.
Organizations
Organizations play a role in insider attacks. They may have lax security procedures or provide access privileges to everyone. Do you store data in unsecured locations? If so, you may present a belief that security does not appear to be a priority.
Behaviors
Once employees start down the path of insider threats, they may change their work behaviors. Individuals may access information that is outside their job responsibilities or ask to work from home more frequently. They may work odd hours or on weekends when fewer employees are working. Insiders may retain files locally or make unnecessary copies of files.
5. How to Prevent Insider Attacks
You can take steps right now to reduce the possibility of a successful insider attack. Our IT security experts at Machado Consulting can even help you to get started. Some of our top recommendations to prepare against internal IT threats include:
- Monitor behaviors. There are tools to track user behavior and alert personnel to any changes that might signal a potential threat. In fact, regular server health checks can help you to proactively identify internal IT threats before they become a problem.
- Purge accounts. Create policies that systematically remove accounts that are not used, especially accounts tied to terminated employees.
- Educate employees. Training individuals on how to detect possible cyberattacks can mitigate the risk associated with social engineering or user manipulation.
- Strengthen Authentication. Adopt multi-factor authentication and consider a zero-trust architecture.