As cybercrime becomes more sophisticated, you need to reconsider how you view cybersecurity. Do you take active, reactive, or proactive cybersecurity measures when it comes to protecting your business from cyber threats?
An active approach prepares your business for an attack. Although defenses may be in place, your team focuses on what actions to take once an attack actually happens. A reactive approach is just that – you take action after the breach happens. For example, you may not have even known your network was compromised until you need to react to a problem. Like most businesses, you probably take more of an active approach when it comes to protecting your business. While that’s a good approach, there’s a better way. When you take proactive cybersecurity measures, you strengthen your cybersecurity posture to minimize the risk of a cyberattack to begin with.
A proactive cybersecurity strategy includes specific actions to reduce your risk and the impact of a cyber threat against your business. Following are proactive cybersecurity measures that can help you stay ahead of cyber threats against your business:
7 Proactive Cybersecurity Measures Keep Your Business Safer
1. Implement a Zero-Trust Framework
Zero-trust is a cybersecurity concept that assumes every request for network access is a potential threat. Without a zero-trust framework, organizations authenticate a user without restricting access to network resources. For example, marketing employees start their day by logging on to the network. Once authenticated, they are free to access resources that have little to do with their jobs such as financial data or client information. Part of a zero-trust approach is limiting access based on the concept of least privilege.
Least privilege means restricting employee access to those resources necessary to do their jobs. For example, establish permissions so only accounting personnel can access financial information. Limit accounts payable personnel to specific modules in the accounting software. If an employee needs access to added data to prepare quarterly reports, grant access only for the time the data is needed.
Remote workers pose an added threat when it comes to user authentication. How does a business know that the remote employee isn’t a hacker? Multi-factor authentication (MFA) should be part of every zero-trust framework. With MFA, users log on with traditional credentials, but an added verification step is required before access is granted.
For example, many online financial services send a passcode to users’ smartphones after they have entered their usernames and passwords. The passcode must be entered before access is granted. Although hackers may compromise user credentials, they are unlikely to have a user’s cell phone to receive the passcode. The added step in authentication helps ensure that users are who they say they are.
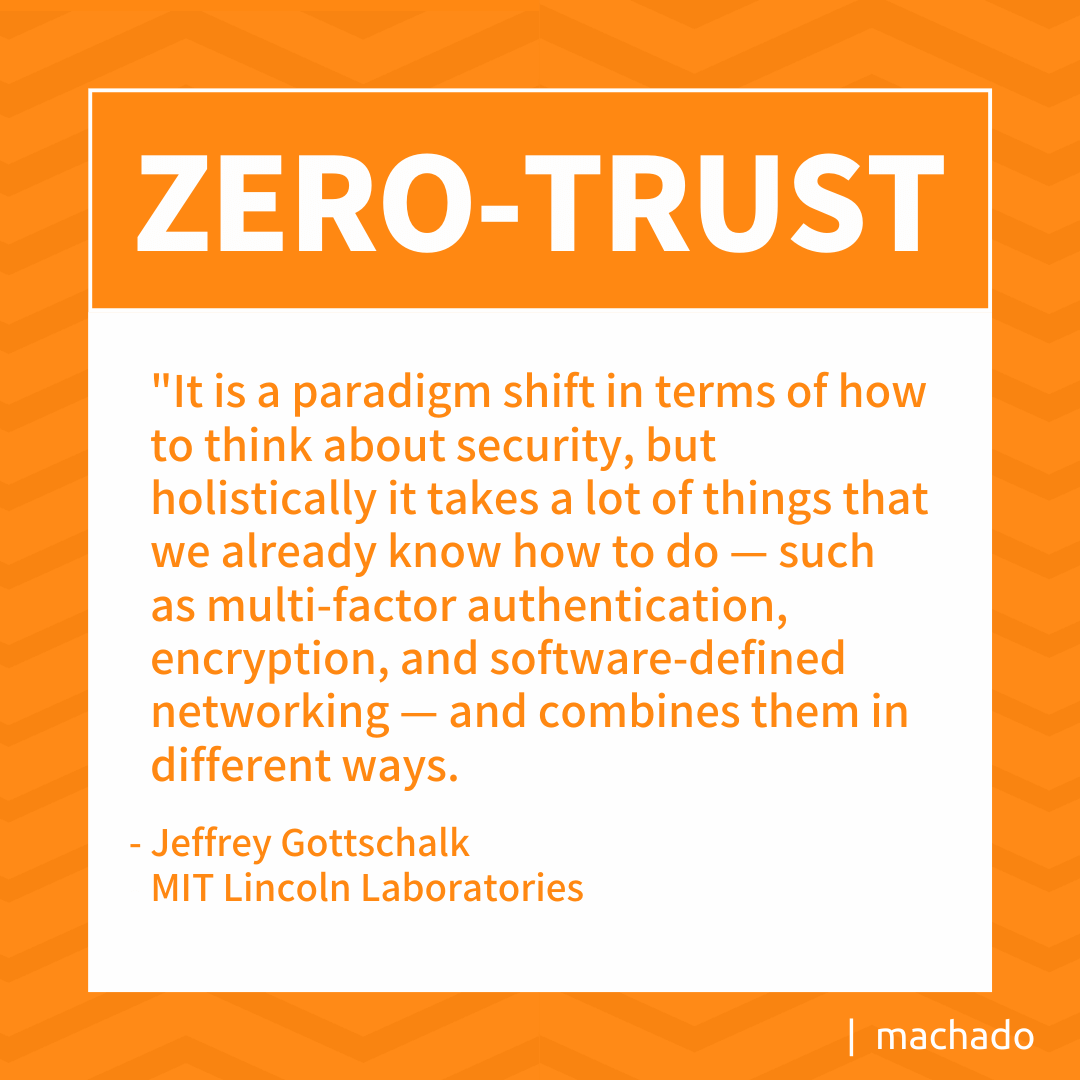
MIT Lincoln Laboratory recently completed a study on zero-trust architectures to define the term and to better understand the misperceptions around the concept. One of these is that a zero-trust architecture requires all new equipment and locks down systems so they are not actually usable. According to Jeffrey Gottschalk, at Lincoln Laboratories, “It is a paradigm shift in terms of how to think about security, but holistically it takes a lot of things that we already know how to do — such as multi-factor authentication, encryption, and software-defined networking — and combines them in different ways.”
2. Schedule Software Updates
Cybercriminals work 24/7 to discover new ways to compromise a system, and software providers spend an equal amount of time trying to prevent them. When a vulnerability is identified and a patch becomes available, software companies such as Microsoft and Apple provide security fixes as part of their software updates. If the updates are not applied, systems remain vulnerable to attack.
The 2021 attack on Microsoft’s Exchange Server illustrates the long-term impact of lax software update policies. Exchange server was released in 1996 as an on-premise solution. Although Microsoft issued four updates between 2010 and 2019, the company could not guarantee that the updates were applied. The potential vulnerability became a national security issue when China was identified as the source of the attack, requiring the White House to appeal to organizations to apply the updates immediately.
Not only do companies need to ensure their software updates are applied promptly, but they also need to verify that third parties with system access have updated systems. A 2022 report found that 27% of ransomware attacks were delivered through third-party access. Cybercriminals often target small and mid-sized businesses they believe are more vulnerable to gain access to other systems.
3. Backup Your Data
Your system backups require more than a copy of a production system. They require offsite storage of backups. Having a system backup continues to be the fundamental component for minimizing the impact of a ransomware attack; however, the backup can no longer reside in the same location as the production system. Today’s cybercriminals ensure that backups are unavailable before launching an attack.
Although Ryuk ransomware attacks have been around in some form since 2018, modifications have made it an aggressive ransomware that hackers tailor to specific targets. A key component of the attack is the disabling of any system copies or automated backup processes to reduce the chances of a target refusing to pay the ransom. These background tasks are performed before the ransomware is launched, making an active or reactive cybersecurity strategy ineffective.
Proactive cybersecurity measures focus on system backups with the understanding that they are also a critical component of any disaster recovery or business continuity plan. Cyber compromises are not the only reason for operational disruption. Natural disasters and human-initiated catastrophes can impact operations. Having offsite system backups can reduce downtime and ensure your data security.
4. Use Antivirus Scanners
You’re probably familiar with anti-virus scanning software such as McAfee and Norton. In fact, these solutions have become so common that businesses may not realize scanners are not all equal. Some solutions compare incoming threats against a known list of viruses; others scan for advanced persistent threats (APTs) for more comprehensive protection.
Phishing emails are still the most common delivery method for ransomware. Whether the emails contain malware or a link to a malicious website, hackers count on a harried employee to accidentally click on a link or download an attachment. With anti-virus scanning, embedded viruses can be detected and removed reducing the chance of infection.
The Sophos 2021 survey on the State of Ransomware found the following:
- 37% of organizations were hit with a ransomware attack.
- $170,404 (US) was the average ransom paid by a mid-sized business.
- 65% of a company’s data was recovered after paying a ransom.
The U.S. ranked third in the world for the number of ransomware attacks. Having a robust anti-virus scanning solution should form the basis of your proactive plan for network security.
5. Implement Endpoint Monitoring
Endpoint monitoring has become a critical component of a cybersecurity strategy. With the rise in remote workers and internet-of-things (IoT) devices, what’s happening at the edge of a company’s network increases its vulnerability to cybersecurity threats. In 2021, cybercriminals exploited weaknesses in endpoint detection beyond 2020 attempts. While script-based attacks continue to be the primary attack method, browser-based attacks are increasing as more companies continue their hybrid work environment.
Many organizations are not equipped to protect against cybersecurity threats at the edge. They lack real-time visibility of their endpoints and have limited ability to respond quickly to a possible threat. Recent research discovered the following:
- On average, IT spends 36 hours a month on endpoint monitoring.
- Over 40% of companies take at least a week to distribute critical patches, and close to 40% take more than a week.
- Nearly 35% of IT respondents said they lacked visibility at their endpoints.
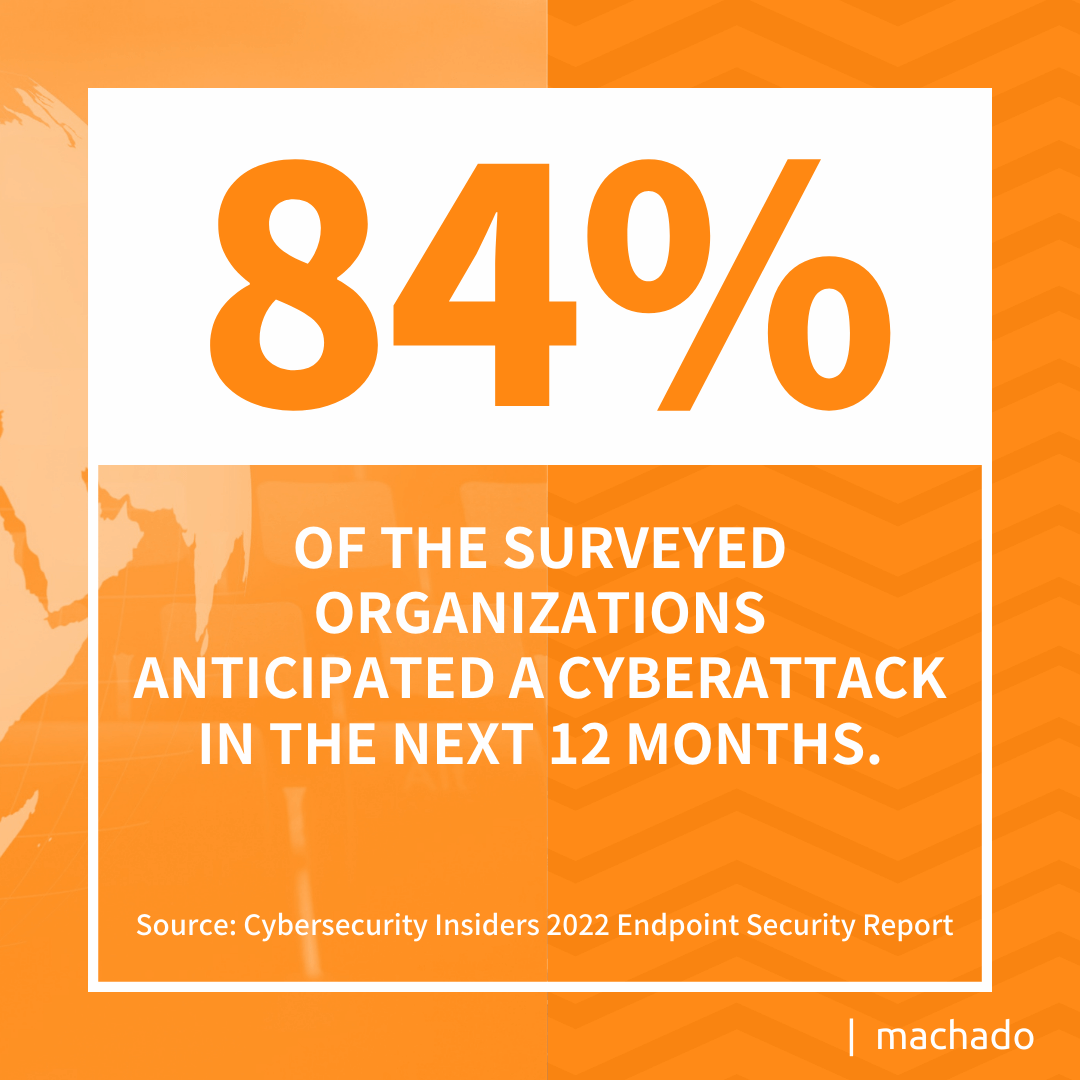
Limited resources can make it difficult for companies to maintain a comprehensive endpoint monitoring program. The same limitations create a challenge for delivering critical updates quickly. Given that 84% of the surveyed organizations anticipated a cyberattack in the next 12 months, your need for endpoint monitoring has become a vital part of proactive cybersecurity measures.
6. Refresh Ongoing Employee Training
Believe it or not, your employees present the largest threat to cybersecurity, and they also serve as the last line of defense to your network. That’s why it’s essential that you make security training an ongoing process. Today’s cybercrime tactics change faster than experts can design ways to protect against them, often making yesterday’s training almost obsolete.
According to IBM’s annual Cost of a Data Breach report, 95% of compromises are the result of human error. That may include anything from improper system configuration to clicking on malicious links. With proper training, many of these errors could be avoided. Adequate training makes the difference between responding or not to a bogus email address that initiates a business email compromise (BEC) attack.
Training must include everyone from the top and down. This includes the CEO and members of the executive suite to your back office employees and, in some cases, even contract workers who may have access to your network. Employees need to understand password management and how to protect mobile devices from compromise. They need to know the latest phishing or smashing tactics, so that they do not fall victim. IT departments need training on current trends and threats to ensure their cybersecurity strategies protect against the latest threats. IT personnel can check security websites such as CISA to ensure they are up to date on cybersecurity threats.
7. Deploy AI-Powered Network Monitoring
Most people are aware of the cybersecurity labor shortage. The latest data suggests the U.S. had 435,000 unfilled positions at the beginning of 2022; as more companies continue to operate with limited resources, the chance of a successful cyberattack increases. One way to ease the pressure is to deploy Artificial Intelligence (AI) based monitoring solutions.
Financial institutions and credit card companies have been using AI to analyze data from multiple sources in real time for years. This technology alerts people when a transaction is outside their routine. Maybe, it’s a different store location or a larger amount than usual. Whatever the deviation, the AI tool generates an alert.
AI-based cybersecurity tools perform the same functions for potential cybersecurity risks. For example, they collect data on every user on the network. When users deviate from their normal behaviors, the AI tool notifies IT. Alternatively, AI tools can be configured to prevent a user from attempting unauthorized access.
AI systems can go beyond analyzing user behavior. They can look at network behavior. Suppose a given endpoint suddenly shows increased traffic. The AI tool could notify cybersecurity specialists or shut down the connection until the behavior can be investigated. The solution not only identifies a potential threat, but it also shuts down the threat until staff is available to address the behavior.
If organizations have difficulty delivering updates promptly, AI can oversee the distribution. Tools can evaluate the criticality of the update and assess the potential threat risk before initiating enterprise-wide delivery. Letting an AI solution keep applications current improves security and frees resources from routine tasks. With AI capabilities, specific builds can be delivered when patches must be applied. Ultimately, this all fits nicely for your focus on proactive cybersecurity measures.
How to Get Started
Sometimes the best proactive cybersecurity measure is admitting your business lacks the resources that adequately protect your infrastructure. When that’s the case, you want a partner with the expertise to keep your network secure.
Contact us today to learn about the benefits of working with a trusted cybersecurity partner.