Experienced professionals who have earned essential cybersecurity certifications are in high demand. In fact, a growing IT security workforce shortage is reaching a critical mass that could impact cybersecurity compliance and threat deterrence far worse than the struggles of today’s freight hauling sector.
Remember the splashy headlines in 2021 about log jammed ports and upwards of 110 cargo vessels idling off the coast of California waiting to dock and offload? One of the core reasons supply chains became backlogged was due to an 80,000 truck driver shortage. Now, consider that the shortage of experts holding necessary IT cybersecurity certifications far exceeds that trucking industry workforce shortage.
According to Cybercrime Magazine, “Over an eight-year period tracked by Cybersecurity Ventures, the number of unfilled cybersecurity jobs grew by 350 percent, from one million positions in 2013 to 3.5 million in 2021. For the first time in a decade, the cybersecurity skills gap is leveling off. Looking five years ahead, we predict the same number of openings in 2025.” Additionally, the U.S. Bureau of Labor Statistics projects “information security analyst” will be the 10th fastest growing occupation over the next decade, with an expected growth rate of 31 percent compared to the 4 percent average growth rate for all occupations.
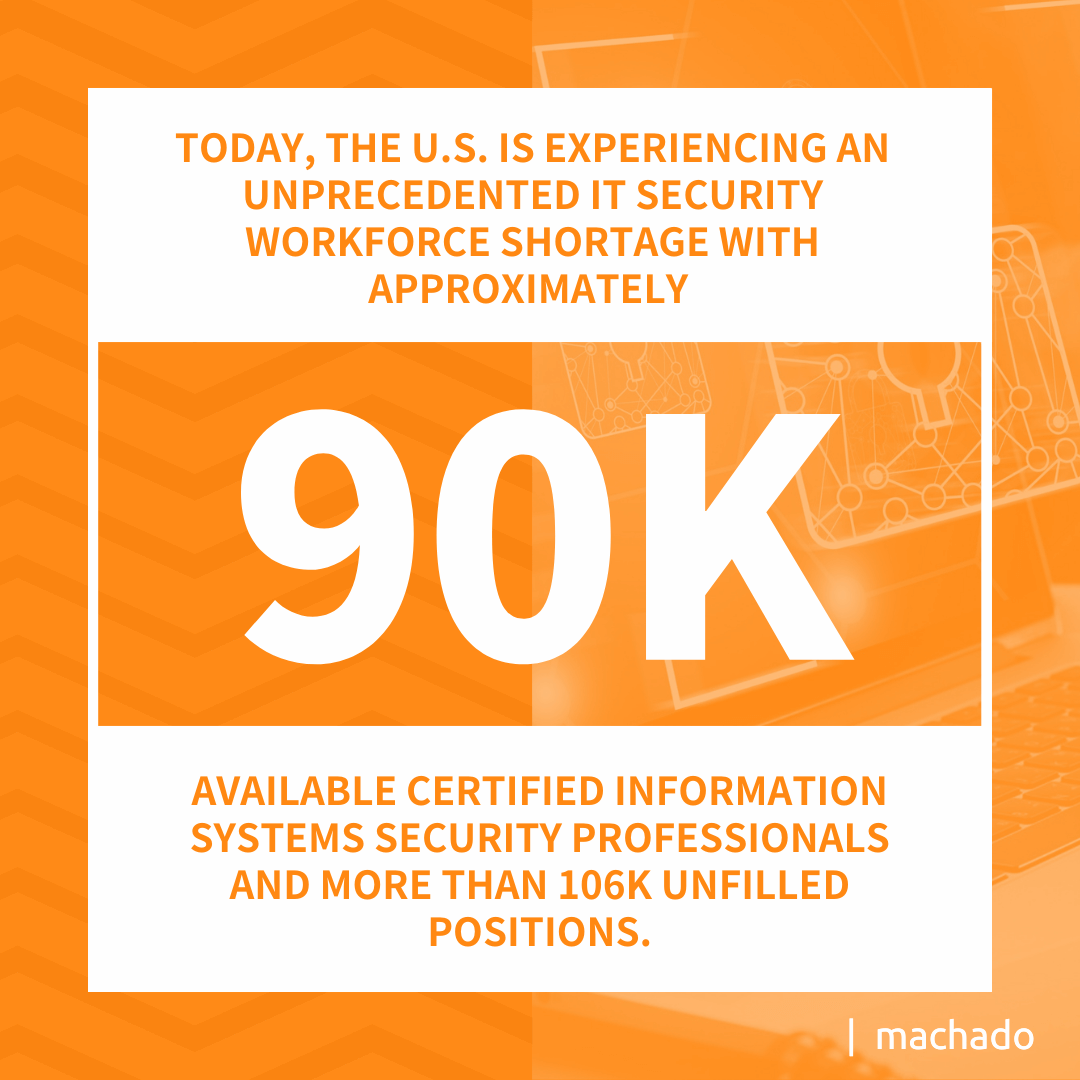
Today, the U.S. is experiencing an unprecedented IT security workforce shortage with approximately 90,000 available Certified Information Systems Security Professionals (CISSPs) and more than 106,000 unfilled positions. According to Cyber Seek, upwards of 1,053,00 cybersecurity professionals were employed in the U.S. However, nearly 600,000 positions remain vacant on a routine basis. That’s over a half million unfilled cybersecurity positions.
If an 80,000 truck driver shortage can derail major portions of the national supply chain, hackers must be champing at the bit to breach business networks in unprecedented ways. As a result, small, mid-sized, and even large businesses are seeing the need to collaborate with a co-managed IT partner with field experience and appropriate cybersecurity certifications. It’s either that or fall behind in regulatory cybersecurity compliance and become the low-hanging fruit for hackers to harvest.
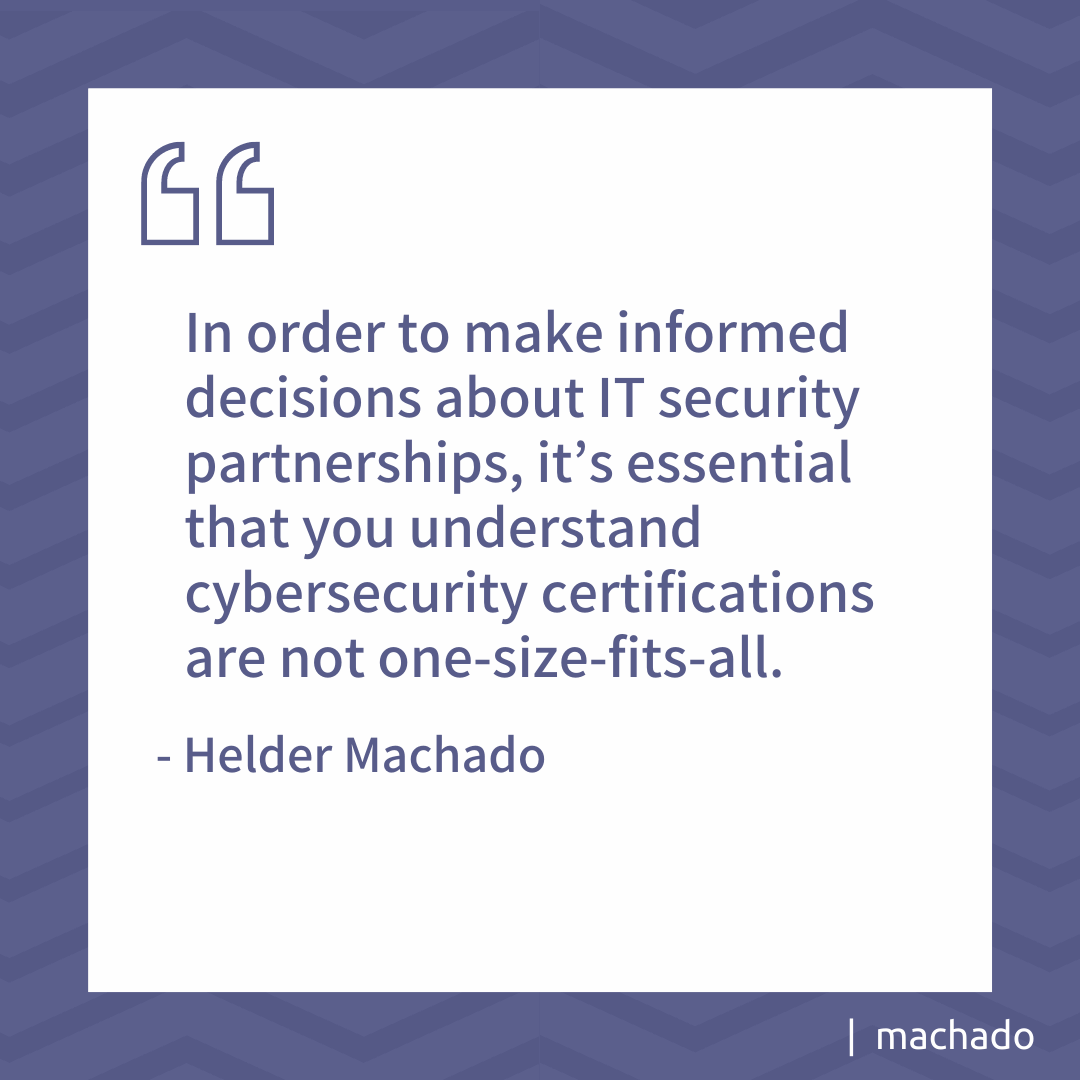
In order to make informed decisions about IT security partnerships, it’s essential that you understand cybersecurity certifications are not one-size-fits-all. There are wide-reaching certification concentrations that can generally be broken into two groups — professional or academic.
How Do Professional and Academic Cybersecurity Certifications Differ?
Cybersecurity certification programs generally serve two goals. They help train incoming technicians about ways to employ tools and technologies to protect systems and sensitive data. The other involves furthering the knowledge of experienced professionals to keep pace with emerging strategies and techniques to stay ahead of the latest methods being deployed by cybercriminals. You may find the following overview of professional and academic certifications useful.
Professional Cybersecurity Certifications
Also used to highlight proficiency in a cybersecurity niche, professional certifications are typically necessary to meet industry requirements and secure a position. The majority of cybersecurity job opportunities require some type of certification.
Earning these measures usually requires fulfilling prerequisites such as a certain amount of time working in the sector. For example, becoming a Certified Information Systems Security Professional (CISSP), considered the gold standard for cybersecurity certifications, generally calls for a minimum of five years of paid, full-time experience. It also requires (ISC)2 domain experience and at least one college degree.
There are seemingly endless lists of professional cybersecurity certifications. But it’s critical to partner with a managed IT cybersecurity firm that has acquired certifications from the most recognized and respected organizations in the industry. This is a short list of reputable organizations.
- The International Information System Security Certification Consortium (ISC)2
- EC-Council
- CompTIA
- Global Information Assurance Certification (GIAC)
- Information Systems Audit and Control Association (ISACA)
While these rank among the industry-leading outfits to get training and certification, others may offer select programs that serve a company’s unique interests.
Academic Cybersecurity Certifications
When vetting a third-party cybersecurity firm, it’s important to partner with an outfit that brings new and expansive skills to the equation. Your in-house technicians may already possess invaluable cybersecurity skills. Adding an outside partner to work with them, and creating a co-managed IT environment, can help expand your workforce’s practical knowledge base. This provides added value because a good cybersecurity partnership is like a rising tide that lifts all boats.
It’s not uncommon for small and mid-sized businesses to employ people who possess academic cybersecurity certifications to maintain system defenses. That’s mainly because these programs involve relatively short coursework and may not lead to a bachelor’s or master’s degree. This approach tends to benefit entry-level IT technicians and those with a college degree who are interested in accumulating knowledge.
Reaching out to an experienced professional to augment a relatively inexperienced technology department is a good way to harden your defenses while exposing newly-minted IT workers to advanced cybersecurity methods.
Why Cybersecurity Certifications are Essential
As industry leader you would be well-served to partner with a cybersecurity team that earned among the most critical training thresholds possible. Authorities on the subject, such as Julien Legrand, Operation Security Manager for the Paris-based Société Générale, ranks among the leading voices in the sector. He delivers speeches, works as a security leader for the French multinational investment bank, and produces technical writings. When interviewed about the value of cybersecurity certifications, he offered the following.
Legrand explained, “Certifications, therefore, serve to validate the knowledge and skills acquired when completing a cybersecurity course. This is important since potential employers require applicants to not only demonstrate knowledge of the positions they apply for, but also to provide proof they are certified.”
He added, “More importantly, obtaining a cybersecurity certification demonstrates a person’s initiative to complete assigned duties. Before earning a certification, a cybersecurity professional must complete various pieces of training to acquire the desired skills. Different certifications apply to a job’s relevance, and this shows employers that a certified expert is capable of undertaking actions that come with a particular field.” 
Which Cybersecurity Certifications are Mission Critical?
It seems as if countless IT security certifications exist, and more crop up every day. But industry experts such as Legrand and many others generally agree that a handful remains critical to securing a cybersecurity perimeter. These rank among the certifications many agree are mission-critical.
- Certified Information Systems Security Professional: Ranked among the highest cybersecurity certifications, earning the CISSP requires years of hands-on experience, study, and passing multiple exams. Those who possess this certification are considered among the most experienced and knowledgeable cybersecurity experts on the landscape today.
- CompTIA Certifications: CompTIA is the world’s leading technical association that provides four IT certification series that range from entry-level to expert. The CompTIA CySA+ is an intermediate-level cybersecurity certification that focuses on the candidate’s ability to proactively capture, monitor, and respond to network traffic findings. It also emphasizes software and application security, automation, threat hunting, and IT regulatory compliance.
- Certified Ethical Hacker: Gaining certification in this niche arena empowers a professional to use a garden variety and advanced hacking methods to penetrate a network and simulate a data breach. By duplicating the strategies likely used by online criminals, an ethical hacker provides organizations with a final report detailing vulnerabilities. This knowledge proves invaluable in closing gaps and protecting digital assets.
- SANS GIAC Security Essentials: The SANS Institute provides IT security training. Founded in 1989, the organization has trained more than 165,000 people. SANS subsequently formed the Global Information Assurance Certification (GIAC) program to serve its IT security certification wing. Highly respected, more than 30 specialized certifications are offered.
- ISACA’s Certified in Risk and Information Systems Control Certification: This enterprise-level risk management accreditation validates a cybersecurity professional’s experience in terms of live-action risks and deterrence. Gaining this certification indicates a managed IT cybersecurity expert can effectively respond to advanced persistent threats in real-time.
- Certified Information Security Manager: This advanced cybersecurity certification demonstrates a professional has acquired the experience and knowledge necessary to oversee an enterprise information security (infosec) program. Certification tasks individuals with passing a 150-question exam that covers information security governance, information risk management, information security program development and management, and information security incident management. To apply, an IT professional must have at least five years of experience in the field.
- Penetration Tester Certification: Ethical hackers are among the professionals who engage in penetration testing. Securing a cybersecurity certification in this niche ensures someone has the knowledge and skills to conduct surveillance on a network and its users. By exploiting the vulnerabilities presented by system gaps and through password attacks on those with network access, company leaders receive an in-depth analysis that pinpoints weaknesses.
- Certified Cloud Security Professional: Given the cost-effective use of Cloud-based networks, more and more companies transition away from physical in-house systems every year. Cloud certification has evolved into an almost standard measure of a firm’s knowledge base. Possessing Cloud Security certification demonstrates enhanced technical skills and knowledge regarding infrastructure, security, and best practices.
Along with these core cybersecurity certifications, experts often note that specializations for select organizations also deliver excellent value. This holds particularly true in the health care and finance industries and those working in the military supply chain, where cybersecurity compliance mandates, such as CMMC 2.0, can be stringent.
How to Select the Right Cybersecurity Partner for Your Needs
You can anticipate a significant reduction in cybersecurity workforce options in the coming years. The days of adding in-house IT staff members with advanced cybersecurity training will likely start to resemble a trucking industry without enough drivers to local retail shelves fully stocked.
“Although many cybersecurity companies and experts have been at the forefront warning about the vast shortage, research and surveys from reputable sources indicate the deficit will continue worsening in coming years,” Legrand said. “This, fueled by relentless attacks motivated by financial gains, requires industry leaders to take a proactive step to resolve the problem. Cyber adversaries are constantly devising more ingenious means of executing attacks.”
Your digital assets might not be on one of 110 ships waiting to dock at the Port of Long Beach. However, a growing cybersecurity workforce shortage means you need a trusted advisor to remain safe.
Contact us today to learn about the benefits of working with a trusted cybersecurity partner.
Selecting the co-managed IT partner with cybersecurity expertise starts with reviewing credentials such as certifications. It’s essential the firm’s experience and knowledge-based seamlessly fit your industry needs. Cybersecurity compliance experience and threat mitigation are foundational items. These are other key items to consider:
- What are the organization’s technical capabilities?
- Does the firm have a local or regional presence?
- Will the partnership involve real-time threat assessment and response?
- Do you feel comfortable about information sharing and privacy?
- Will the partnership benefit in-house staff members?
- What are the human metrics associated with this business relationship?
You need an IT partner who can fill security information gaps and mentor in-house IT staff members that adds value to the relationship. With the right guidance, your sensitive and valuable digital assets can enjoy the protection and determined cybersecurity necessary to do business in the digital age.