If you’re like any leader with a small business, you’re tasked with leveraging dwindling resources to further your company’s goals. Included in that is the hazy effort of allocating resources, and setting IT budgets with an eye on cybersecurity.
Industry leaders typically walk a fine line that involves allocating enough of their monthly and annual budgets to ensure determined defenses remain in place against other commitments.
But the essential question every decision-maker really needs to be answered is whether you can actually take steps to avoid being hacked.
The truth about the rising tide of cyber attacks garnering national headlines may frighten you.
Professional Hacks Are Here to Stay
The facts are that it appears no organization possesses the hardened defenses to prevent high-level threat actors from penetrating their system.
The dust-up from the Colonial Pipeline ransomware attack sets an example that even large corporations with seemingly robust resources can fall prey to sophisticated hackers such as DarkSide. With the fuel supply on the Eastern seaboard stymied, the gas lines and pumps that ran dry burned an image in the minds of everyday Americans.
Unfortunately, no one is immune to cyber attacks.
In the wake of the Colonial Pipeline breach, officials in the federal government were forced to admit they cannot fully stop hackers. They are now pivoting to urge private-sector organizations to strengthen their cybersecurity defenses.
“The first thing we have to recognize is this is the reality, and we should assume, and businesses should assume, that these attacks are here to stay and, if anything, will intensify,” U.S. Commerce Secretary Gina Raimondo reportedly said. “So, it is clear that the private sector needs to be more vigilant, by the way, including small- and medium-sized companies.”
If anything, Secretary Raimondo speaks truth to power about the current state of global cybersecurity. Hackers continue to devise strategies to adapt and overcome the best-conceived platforms, cybersecurity policies, and responses.
If there’s any doubt that the feds are dropping any façade that once existed about protecting small, mid-sized, or large corporations, consider the following statistics regarding cyber attacks.
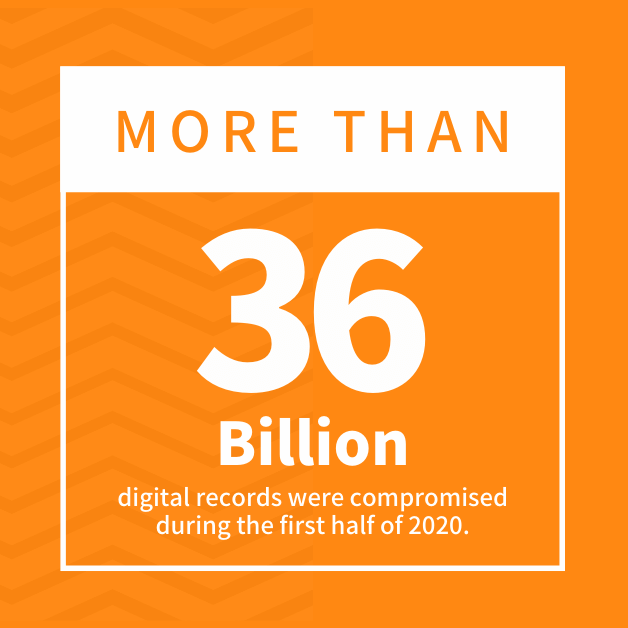
- More than 36 billion digital records were compromised during the first half of 2020.
- Malware infections increased from 12.4 million in 2009 to 812 million in 2018.
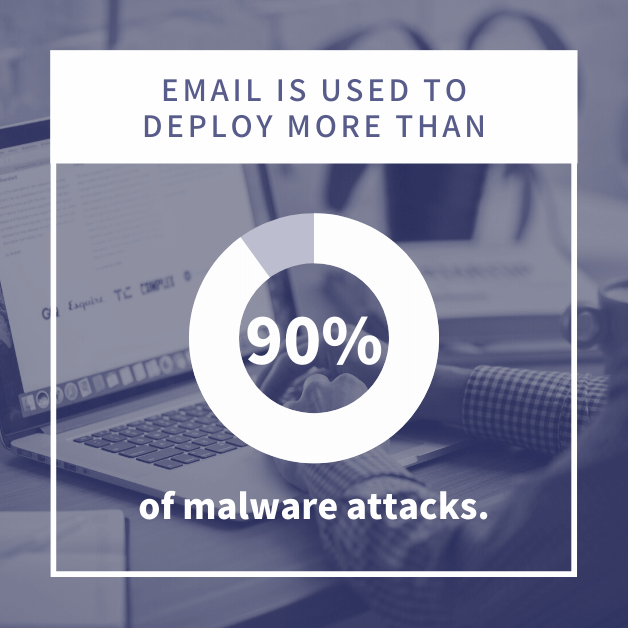
- Email is used to deploy more than 90% of malware attacks.
- More than a quarter-million malware samples are crafted every day.
- Nearly 90% of organizations worldwide experienced sophisticated spear-phishing attempts in 2019.
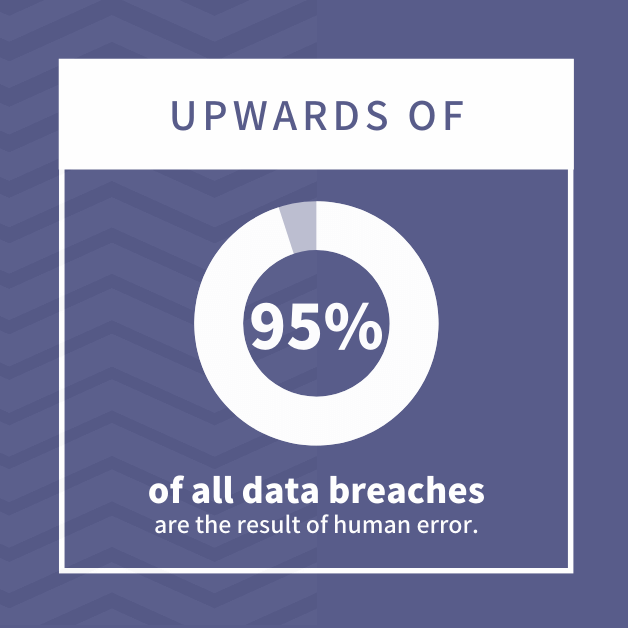
- Upwards of 95% of all data breaches are the result of human error.
Although the Colonial Pipeline hack garnered widespread media attention due to its tangible economic impact, it doesn’t even rank among the top 15 worst hacks.
Small and mid-sized organizations that want to avoid being hacked may want to think about the fact that most hackers prefer to target the low-hanging fruit rather than big companies with substantial investment into cybersecurity.
Regardless of what anyone in the IT and cybersecurity industry says, it’s abundantly clear that neither government agencies nor private-sector organizations can fully prevent a cyber attack.
To avoid being hacked, you must demonstrate that you are not the low-hanging fruit and stand ready to respond to an online incursion. That’s why it’s recommended private-sector outfits adopt the NIST Cybersecurity Framework.
What is the NIST Cybersecurity Framework?
The National Institute of Standards and Technology (NIST) functions as a non-regulatory government agency that works diligently to enhance technology and drive cybersecurity standards.
In this area, NIST develops standards that help federal, state, and private-sector organizations comply with the Federal Information Security Management Act (FISMA).
In recent years, NIST has been used as the bedrock for the U.S. Department of Defense’s Cybersecurity Maturity Model Certification (CMMC) that requires contractors and those in the military supply chain to meet cybersecurity expectations.
Although businesses such as accounting firms, healthcare organizations, and other privately-run businesses do not necessarily require federal CMMC certification, the NIST Cybersecurity Framework offers ways of thinking that can help outfits avoid being hacked.
The NIST approach does not necessarily have to drain a small or mid-sized company’s technology budget. But adopting its principles and procedures can harden your cybersecurity defenses to prompt hackers to spend their energy elsewhere.
The following 10 recommendations are concrete ways for your business to maintain its cybersecurity and avoid being hacked.
1. Identify All of Your Assets
It’s essential to understand that digital assets are not necessarily limited to items such as bank account numbers, industry secrets, or patents, among others.
Digital assets could mean anything, including video content, e-commerce platforms, and electronic messages. If a hacker can steal or ransom a digit file, it ranks among your assets.
The first step in defending your company from a cyber attack calls for a complete inventory of what needs protecting.
2. Perform a Risk Assessment
The NIST Cybersecurity Framework outlines the methods and tools necessary for a thorough risk assessment. Its underlying idea measures the most vital digital assets against potential threats.
Industry leaders typically contract with a third-party cybersecurity firm to run breach scenarios against a system without employee knowledge. This “ethical hacker” practice is typically followed by an analysis of strengths and weaknesses.
By understanding the baseline defenses, vulnerabilities can be shored up, and cybersecurity policies may be updated. Only by knowing what a digital thief views as low-hanging fruit can an outfit raise the bar and avoid being hacked.
3. Provide Awareness and Training
Year-over-year, human error continues to be the overwhelming cause of cybersecurity breaches.
For example, the headline-grabbing Colonial Pipeline and Solar Winds infiltration of 2020 were reportedly the result of employee mistakes. In many instances, employees fail to employ strong passwords, change them on a regular basis, or recognize an email is laced with malicious software.
Untrained staff members routinely fall for sophisticated spear-phishing schemes that gain someone’s confidence and then exploit their access to the network. The only solution to reducing human error is ongoing cybersecurity awareness training. An organization’s employees are its front line defenses.
4. Maintain All Software, Hardware, and Firmware System Updates
While targeting staff members through email remains a bad actor’s preferred weapon, software, hardware, and firmware deficiencies increase the likelihood of a breach.
People outside the technology sector often understand those routine software updates as a way to fix bugs. That tends to be only partially true.
Software and other manufacturers in the tech sector also patch items to prevent cyber intrusions. As manufacturers identify hacking schemes to penetrate their products, updates are launched to help consumers avoid being hacked.
That’s why updating software, hardware, and other IT platforms is essential to prevent blunt-force attacks.
5. Deploy a Security Information and Event Management (SIEM)
Enterprise-level cybersecurity may require an organization to possess the ability to track digital activities that transpire in their environment.
The SIEM system has evolved over more than a decade. When deployed by private businesses, it can deliver security-related incident reports.
These generally include failed attempts to log in to a network and malicious activities. In addition, a designated individual or group may receive real-time alerts about emerging threats.
6. Provide Daily, Weekly, and Monthly Monitoring Updates
When business leaders take a moment and compare their approach to profit-driving processes and cybersecurity, they often see a glaring difference.
For example, department heads routinely provide daily, weekly, and monthly reports indicating efficiency, cost, and offer projections for their department. This proactive approach has proven long-term benefits.
By contrast, cybersecurity is too often based on a reaction to after-the-fact incidents.
The NIST Cybersecurity Framework calls for the accumulation and assessment of ongoing data. The information generated from SIEM, among other pathways, offers keen insight into the frequency and methods used by threat actors.
It can also lead to taking preventative measures that result in your organization having the digital wherewithal to avoid being hacked.
7. Develop an Incident Response Plan
Although the goal is to avoid being hacked in the first place, the troubling statistics about data breaches and ransomware attacks indicate every business should have a response plan in place.
Your incident response (IR) plan should highlight precisely what team members are required to do in the event of an attack. A well-conceived IR plan brings all of your key stakeholders into the process of deterring a threat and protecting at-risk digital assets.
In addition, an IR plan provides guidance that allows each team member to act decisively and minimize the time required to batten down the hatches, so to speak.
Here are some elements of a determined IR plan worth considering.
- IR Vision – Begin by working with an experienced cybersecurity professional to outline a defense philosophy. Consider publishing a mission statement for your IR plan that brings critical personnel to the table in an intellectual and inspirational fashion.
- IR Detection – Work with IT and cybersecurity specialists to ensure ongoing incidents can be detected, monitored, and documented.
- Roll Out the Process – A robust IR plan tends to be increasingly successful when it is identified as a formal aspect of everyone’s duties. Emphasize the necessity of reporting even low-level attempts to breach your network.
- Execute Your IR Plan – Consider holding high-level meetings with various team leaders to cover the details of the plan. Be specific about how each department is expected to participate and respond under duress. Once leadership team members are onboarded, orchestrate small group meetings.
Lastly, working with a third-party cybersecurity expert can allow you to simulate cyber attack attempts. Simulating these attacks ranks among the best ways to determine your organization’s and staff members’ preparedness.
8. Test Your Plan at Least Annually
Experienced cybersecurity firms use a method called penetration or “pen” testing that mirrors the ways hackers might search for vulnerabilities and exploit them.
This strategy helps industry leaders determine whether employees require additional cybersecurity awareness training, software and other products need to be updated, and other vulnerabilities exist.
Essentially, pen-testing lets you know whether you rank among the low-hanging fruit or enjoy reasonably secure defenses.
Perhaps one of the greatest reasons so many small, mid-sized, and large corporations suffer devastating breaches is they treat cybersecurity as a one-off process. The NIST Cybersecurity Framework indicates that ongoing compliance with cybersecurity regulations and guidelines promotes improved digital asset safety.
Hackers work tirelessly to adapt and overcome the latest defenses by crafting new digital weaponry. As a response, an organization would be wise to pen-test its cybersecurity at least annually, if not more frequently.
9. Backup All Critical Systems Locally and Offsite
Part of every IR plan involves securing digital assets out of the reach of online thieves.
It’s not uncommon for the victims of ransomware attacks to pay the demand and then not receive a decryption code. For this reason, redundant backups are one of the best ways to overcome any intrusions.
By putting up-to-date data in multiple Cloud spaces, physical equipment, and portable drives, you minimize the assets that can be stolen, locked, or destroyed.
10. Review and Test Your Backup Plans Regularly
Backing up critical data remains an ongoing process. Like patching software and providing ongoing cybersecurity awareness training, the moment it takes a backseat is when vulnerabilities surface.
Securing digital assets on a monthly or even weekly basis may not support a robust repatriating of your network after an attack. That’s why it’s important to make backup policy reviews an ongoing requirement.
Does Your Cybersecurity System Need a Second Look?
After considering these NIST Cybersecurity Framework suggestions, how many can you say with certainty your organization meets? If you feel you can check off 9 with confidence, your organization likely enjoys reasonably secure defenses.
But the fewer items you check, the more likely you represent the low-hanging fruit. So rather than get plucked by a cyber criminal, call us, and harden your defenses today.