You’ve read the headlines– Colonial Pipeline: Hacked. SolarWinds: Update Server Compromised.
As a professional services firm, you may think you don’t have to worry about your security, or what might get your business hacked.
After all, bad actors aren’t interested in small or mid-sized firms, right? They’re looking for big-dollar targets with big-dollar payouts.
And besides… you’ve got IT support, right?
A lot of professional services firms like law firms, CPAs, investment groups and healthcare providers don’t have adequate coverage or don’t think they’re large enough to be a target for hackers.
This can be a costly misconception.
Why Professional Services Firms are Attractive Hacking Targets
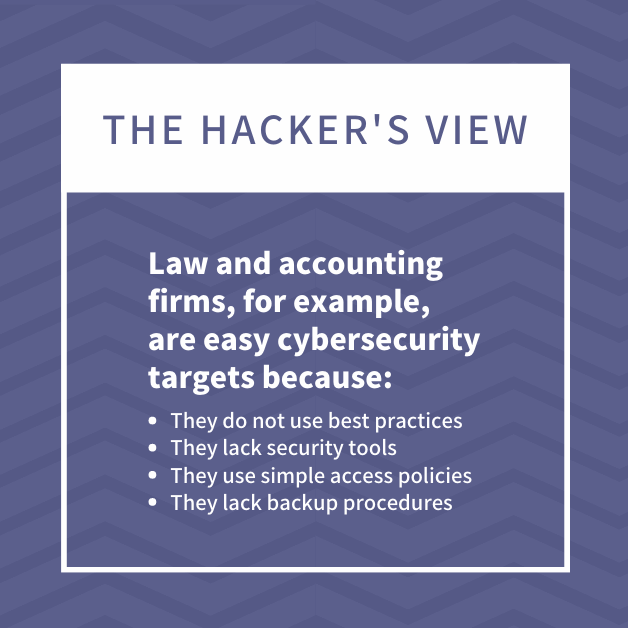
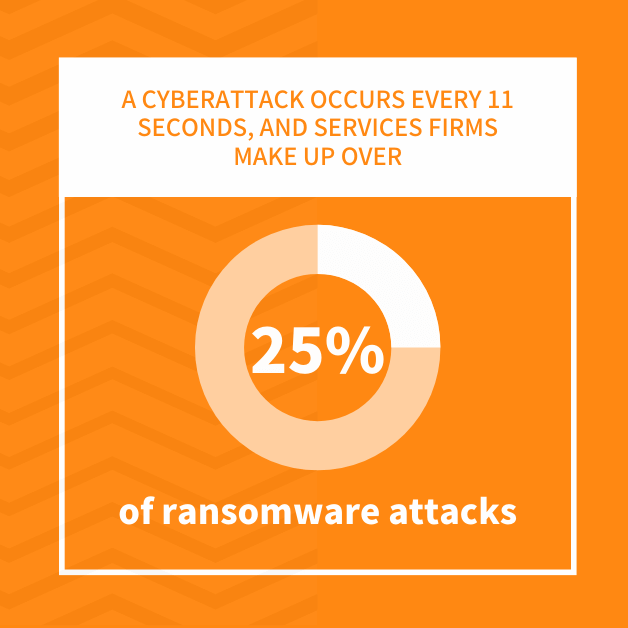
Professional services firms make up 14% of US businesses, but receive over 25% of ransomware attacks. Hackers view law and accounting firms, for example, as easy cybersecurity targets because:
- They lack dedicated IT personnel
- They do not use best practices
- They lack security tools
- They use simple access policies
- They lack backup procedures
To cyber criminals, every device connected to the internet is a potential access point. That’s why professional services firms need to ensure they have strong cybersecurity defenses to avoid getting hacked.
Cyber crime is big business, and cyber criminals are business people. They are looking for the best return on investment.
The news-making attacks are difficult to execute, take time, require more expertise, and do not guarantee a return.
But the professional services industry is a soft target that generates revenue with little effort. Typical professional services firms represent targets that offer a better return on investment. Their network vulnerabilities are easier to detect and faster to compromise.
In many cases, these firms are willing to pay a ransom, making the professional services industry a prime target for a security breach.
How To Keep Your System Safe and Avoid Getting Hacked
While some kind of cyber incident is more or less inevitable for firms, that doesn’t mean you have to let your system actually be hacked.
There are concrete steps you can take to ensure your information, and your client’s information, is safe from cyber criminals.
1. Stop Thinking You Won’t Have Your Business Hacked.
A cyber attack occurs every 11 seconds, so in reality it isn’t a matter of “if” but of “when” your business will experience a cyber incident.
For example, Phillip Galyen reported a cyber attack targeting the law offices of the Texas firm of Bailey & Galyen that exposed personal information on clients and employees. According to its press release, the data included information provided to the firm in the course of representation or employment.
That information may have included names, dates of birth, social security numbers, payment information, medical records, and insurance data. The incident was discovered on May 14, 2021, and is currently under investigation.
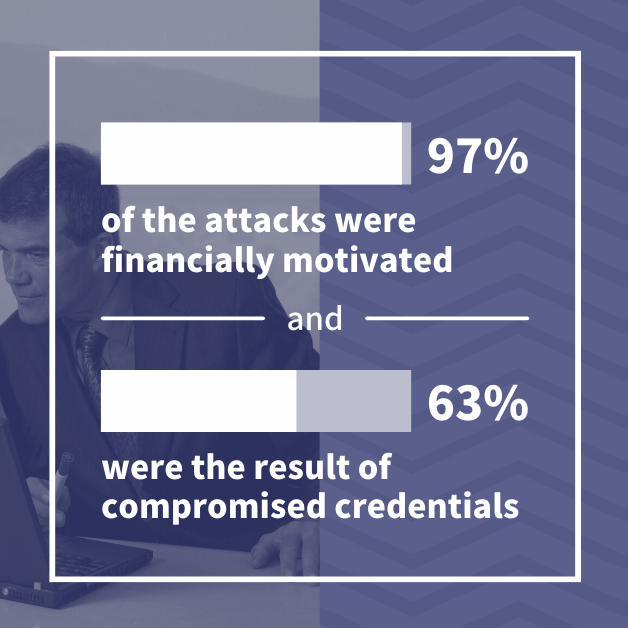
Verizon’s annual report on data breaches found that 74% of professional services attacks came from external sources.
The report also found that 97% of the attacks were financially motivated and that 63% were the result of compromised credentials. The report found that this sector relied heavily on internet-connect resources with its high-risk architecture.
Every state has its own set of cybersecurity reporting laws. Most states require that individuals impacted by the security breach be notified, and the hack is reported to the state’s attorney general– however only 11 states make that data public.
Without full transparency, it is easy for professional services firms to think they are not a target, which simply isn’t true.
2. Stop Making Excuses
It’s easy to say, “We don’t have the resources” or “I don’t have the time.” Even thinking “I’ll do it tomorrow” is an excuse if tomorrow never comes.
Most professional services firms have offices where they meet clients, vendors, and other third parties. These firms would never consider leaving their doors unlocked, or their client information left where anyone could see. Such actions would be considered negligent.
Yet, professional services companies leave their virtual doors open and client information exposed to any hacker who happens to pass by.
When firms do not keep their software up to date, they are failing to close the door on vulnerabilities that allow hackers to exploit the system.
If firms do not restrict access or do not encrypt crucial data, they are letting bad actors look at client information. These actions may occur in the virtual world, but they are as negligent as in the physical environment.
There’s no excuse for leaving your physical or virtual assets exposed to criminals.
3. Stop Using Easy Passwords
Compromised credentials are used in over 60% of cyber attacks. That’s why requiring strong passwords should be a standard policy.
The longer and more complex the password, the harder it is for hackers to guess. Use a minimum of eight characters that include numbers, upper and lower case letters, and special characters.
A typical pattern for compromise in the professional services sector leverages its reliance on the internet and its lack of adequate security precautions. Hackers are able to use stolen credentials to exploit a system vulnerability that ends with a ransomware attack.
With the ongoing rise in ransomware attacks, organizations should implement stronger password policies.
Multi-factor authentication (MFA) is an even better option for security. A user signs in using a known factor such as a password, and then an unknown factor such as a passcode is generated at the time of sign-in and sent to a device. Users enter the code to gain access to the system, creating a second layer of security that can help systems avoid getting hacked.
4. Stop Reusing Passwords
Forcing employees to change passwords frequently can weaken security. Many employees try to reuse passwords or merely add a number to the end of an existing one. Hackers use these bad habits as a way into a firm’s network.
Using a password manager can help– password managers are software applications that encrypt and store passwords. Instead of remembering hundreds of passwords, users only need to remember the password to the manager. The remaining passwords are accessed through the password manager.
Sticking with strong passwords stored in one secure location rather than a constant recycling of similar passwords can heighten the effectiveness of any cybersecurity protection.
5. Stop Being Highly Vulnerable
According to a 2021 report, 85% of cybersecurity compromises involve some kind of human element.
Whether it is a weak password or clicking on a suspicious link, your people are the easiest way in, but also your first line of defense.
Training employees on how to identify and report possible cyber attempts is crucial to a strong cybersecurity system.
Educate your staff on what phishing looks like, how to identify false email addresses, and what to do if they suspect a cyber attack is being attempted. Knowledgeable employees are essential to small business cybersecurity.
Consider a self-assessment questionnaire (SAQ) to help employees remain vigilant when it comes to cybersecurity. These periodic reviews are a way to reinforce a firm’s commitment to cybersecurity awareness.
The 2021 Data Breach Report highlighted the inability of professional services staff to withstand social engineering tactics. Only proper training can ensure that employees are up to date on the latest attack methods.
6. Stop Ignoring Your Network’s Health
Protected networks are healthy networks. Many firms fail to update their software or upgrade their hardware to ensure known vulnerabilities are patched. Yes, software updates take time, and they can lead to glitches or bugs, but the alternative is a compromised system.
Software and firmware updates are not just new features or improved operations. They also include patches or fixes for known weaknesses.
Many organizations fail to update their server software because of the impact it might have on the network. Not applying updates can have a more costly impact on network operations.
Assessing your network’s vulnerabilities is another way to ensure a system’s health. Look at having a cybersecurity audit to identify weaknesses and develop steps to strengthen them. Cyber criminals are continuously finding new ways to compromise a system, so regular audits should be part of any cybersecurity plan.
7. Stop Letting Your Antivirus Expire
No matter what gateway your firm uses to access the internet, any antivirus software that is “included” is not enough.
Hackers can customize their attacks. They are acquiring the ability to modify code after gaining access to obstruct detection. Antivirus software can check your internet traffic against a database of known malicious code and stop it from arriving on an employee’s desk.
Not only should a business keep an active antivirus solution, but it also needs to make sure the software is properly updated. Unless the software is maintained, it can not protect against the evolving network of malicious software.
8. Stop Thinking Your Phone is Secure
Bad actors can find phone hacking software on the internet for free so never assume your phone is not a target. Hackers can compromise phones through:
- WiFi and Bluetooth Connections – Disable WiFi and Bluetooth connectivity unless in use. Accessing these networks is as easy as accessing the internet.
- SIM Cards – SIM cards are the brains of a smartphone, and they can be hacked. You can password protect your SIM card by going into Settings>Cellular>SIM PIN on an iPhone. For Android phones, go to Settings>Lock Screen>Other Security Settings>Set SIM Card Lock.
- Unencrypted Data – Data stored on your phone may not be encrypted. Most phones come with data protection enabled, but you should check to ensure it is still active.
If you use your phone to access your work network or any business-related data, your phone needs the same level of security as a laptop or workstation. If hackers can gain access to your phone, they can worm their way to your firm’s network.
9. Stop Relying Only on Onsite Backups
How often is your system backed up? Weekly? Monthly? If you can’t recall, it has probably been too long. Yes, backups protect against cyber attacks, but they also ensure business continuity.
Ask yourself a few pointed questions, like:
- How much work would you have to do over if you never backed up your live system?
- How much time would be lost if employees could not access the system?
- Have you checked your backups recently to make sure that they’re actually working?
- Backups are the only way to ensure business continuity in case of a power outage or natural disaster.
Local backups may have worked in the past, but they are no longer enough to protect against a cyber attack. In the past, a ransomware attack was circumvented if companies had a backup. But today’s cyber criminals use ransomware that first disables locally stored backups before demanding a ransom.
That’s why onsite backups are no longer effective in countering malware attacks.Your backups should also be maintained offsite, so hackers cannot access them as part of their cyber attacks.
10. Stop Clicking on Links from Unknown Sources
Most employees know not to click on suspicious links, especially if they don’t recognize the sender. The problem is knowing and doing are not the same thing.
First, hackers have become more sophisticated. They have fooled tech companies such as Google and Facebook, so don’t assume that your staff will detect a possible threat unless you train them.
In the middle of a hectic workday, it’s easy to click on a phishing link without thinking. Make sure everyone knows what to do if they should mistakenly click on a suspicious link.
And if it does happen, don’t finger point! Employees won’t say anything if they are going to be chastised. That creates a bigger problem because the faster a potential attack is identified, the less damage is done.
Every inbox gets spam no matter how good the filter. When spam hits your inbox, delete it immediately. Many have a compromised link in the mail that allows viruses to be downloaded. No one wants to accidentally click on a spam link that gives hackers access to the system.
Don’t Be Tomorrow’s Cybersecurity Headline
These ten suggestions are actions your firm can take now to strengthen your security defenses, but these are only the beginning.
Remember the reasons hackers target professional services firms? The number one reason is a lack of IT personnel. Without access to cybersecurity specialists, you still lack:
- Security tools to help defend against attacks
- Established best-practices that ensure security safeguards are followed
- Strong access policies that use a least-privileged model
- Backup procedures that include offsite copies to protect against malware that targets backup and live systems
A cybersecurity consulting firm has access to tools that can assess and test network defenses before hackers attack. They can also help train your employees in best practices to minimize the risk of a human-assisted compromise.
And they are familiar with multi-factor authentication and least-privileged access models, so they help secure your environment. They can provide offsite backup services, so in case of a compromise, your system can be restored.
The right managed services provider can help keep you from having your business hacked and give you the extra security you need.