“My business was hacked!”
Those words are spoken too often by entrepreneurs and industry leaders before they finish their first morning beverage. Half-awake and reeling with the panicked images in their minds, victims of cyber attacks typically repeat the same phrase over and over in their minds, “by business was hacked.”
Those words replay like a song you just cannot get out of your head.
What seems counterintuitive to many professionals is the fact they took reasonable cybersecurity measures to avoid being hacked. A cybersecurity professional gets a phone call or text message from someone telling them, “thieves hacked my business.”
Some wake to drained bank accounts, credit cards maxed out, hijacked personal identity records, or worse. Sometimes sophisticated hackers deploy ransomware and seize control over an organization’s entire network.
Although the shock of digital crime can feel overwhelming, it’s actually not surprising when you consider the following statistical data:
- Since 2001, business losses due to cyber crime have risen every year
- Upwards of 96% of attacks leveraged phishing and spear-phishing schemes
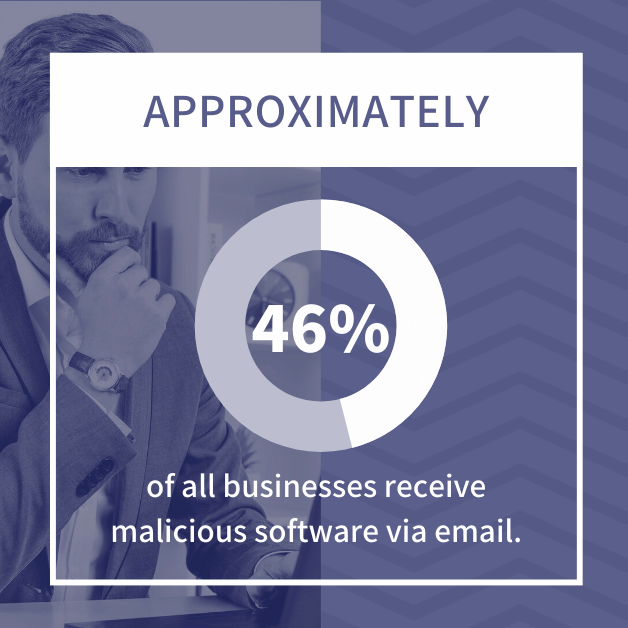
- Approximately 46% of all businesses receive malicious software via email
- Nearly 30% of all users will open at least one phishing email
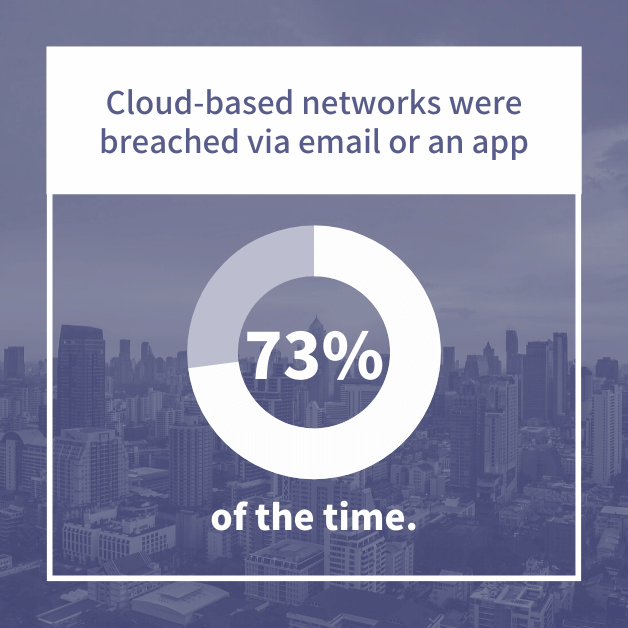
- Cloud-based networks were breached via email or an app 73% of the time
- Human error ranked as the number one reason that data breaches occur year-over-year
This veritable mountain of cyber crime data would seem to indicate business decision-makers should throw up their hands and surrender.
Nothing could be further from the truth. In fact, implementing a determined cybersecurity strategy that includes awareness training can deter many bad actors. That’s largely because hackers typically cast a wide net in hopes of an employee making a mistake or identifying outfits with weak defenses.
Seasoned cybersecurity professionals don’t subscribe to the notion, “hope for the best and plan for the worst.” Instead, they know to plan for the worst and then plan to respond to the worst.
Hackers remain a persistent threat who adapt to the latest defenses and create new schemes to compromise the digital assets of honest business people.
We should all operate under the assumption that one morning you’ll wake up and say out loud, “my business was hacked.”
After that, we’ll be in a foot race to protect every asset possible and repel the incursion. Here are the 10 mission-critical things that need to happen quickly.
1. Isolate and Protect Impacted Systems
During the initial moments of crisis, business professionals often react by contacting key stakeholders regarding the cyber crime.
On the one hand, they want to identify the culprit and have the criminal arrested and prosecuted (a highly unlikely scenario). On the other hand, entrepreneurs and other decision-makers actively seek support.
But what many may not realize is that hackers are not necessarily smash-and-grab thieves. Although you just discovered the business was hacked, digital thieves can operate under the radar for days, weeks, months, even years.
In the infamous Marriott Hotel Group breach, hackers compromised the identity records of more than 500 million people over a 4-year period.
The point is that cyber criminals operate with impunity and are not afraid that you have detected them. They may mine your data until pushed out.
Perhaps the best initial defense to rid your network of a hacker’s presence is to cut it off from the internet. By taking your business offline, you unilaterally forced a ceasefire.
2. Contact and Notify Key Stakeholders of the Breach
Using a secure device, contact your team members and let everyone know you deliberately took the network offline.
Too often, employees panic when systems go down that the business is closing or other nightmarish ideas. Let everyone know that you are leading a charge to vet the system, identify any compromised data, and will respond in kind.
Once your staff has been contacted, promptly communicate with all financial partners that the system was breached. Credit card companies, banks, lending institutions, and others must understand recent transactions need to be reviewed, and everything must be frozen until further notice. The next tier of communication involves alerting insurance carriers and lawyers there is a problem.
3. Implement Your Incident Response Plan (IRP)
Hardened cybersecurity defense and an IRP go hand in hand.
Business leaders should put stringent defenses in place, educate team members with access to digital assets, and plan to respond to the worst-case scenario.
If you have already developed an IRP, trigger all the tenets at this juncture. If you have yet to complete one, the following are common elements to consider.
- Communicate the duties of all incident response team personnel.
- Identify tools, resources, and vital technologies necessary to respond to a breach.
- Craft a business continuity strategy to restart operations swiftly.
- Create a redundant digital asset backup and recovery policy.
One of the common missteps decision-makers sometimes make involves only conveying the IRP to IT professionals. By enlisting the support of department heads and key stakeholders, the IRP can be implemented more quickly while your outfit remains vulnerable.
If you don’t have an IRP or an existing one hasn’t been updated, time is of the essence.
4. Perform a Security Audit to Identify Impact to Your Systems
Security audit policies are increasingly becoming part of the overall strategy of small, mid-sized, and large companies. They outline the methods and practices an organization uses to test and assess cybersecurity strengths and weaknesses.
Given the “my business was hacked” scenario, chances are at least some best practice requires reconsideration. These are security deficiencies that are routinely uncovered:
- Insufficient software patches and updates
- Lack of enterprise-level antivirus software and firewalls
- Unsecured endpoint devices
- Failures to encrypt electronic messages from mobile devices
- Remote workforce members without access to Virtual Private Networks (VPN)
- Lack of password complexity
Although a one-time security audit is an immediate necessity under exigent circumstances, regularly scheduled reviews are advisable.
Responding to cyber crime may be part of the business landscape, but there’s no reason to needlessly position your company as the low-hanging fruit.
5. Require Passwords Changed at Regular Intervals
It’s not uncommon for business people to wonder how often they need to change passwords. A reasonable time frame typically runs between 60-90 days. Password changes are also only as good as their strength and privacy.
One example of a massive password error involved the Solar Winds hack that reached high-level government agencies. An intern reportedly used SolarWinds123 and then posted the weak password on GitHub. This disaster highlights how human error is responsible for upwards of 95% of hacks.
These rank among the best practices to employ concerning company passwords:
- Passwords should be at least 8 characters long and utilize letters, numbers, and symbols.
- Passwords should never be stored on an online platform.
- Passwords must never be shared with even trusted colleagues.
- Companies would be well-served to leverage two-factor authentication.
Other ways to improve password security involve password managers and audits. Systems can also be set up to reject the repetitious use of employee passwords.
6. Review Systems for Backdoors and Unauthorized Accounts
Even when hackers pilfer off millions of dollars in assets or cause disruption, the mainstream media does a relatively poor job of coverage. We see exciting, click-bait headlines but few details about how cyber criminals and hacker organizations operate. The cursory details about ransomware attacks fail to educate everyday people about persistent threats.
Cyber criminals may not just slip in and out of your system overnight. It can take an average of 197 days for a company to discover a hack and nearly another 70 to right the ship in many cases. A confident hacker can create a backdoor or fake employee account that allows them unfettered access to your network.
It’s not unusual for a digital burglar to penetrate a system, create a phony username and password, and lay in wait for more valuable information. When someone screams, “my business was hacked,” the initial breach could have actually transpired months ago.
7. Perform Software and Firmware Updates on All Systems
When hackers are not trying to bamboozle your employees with malware-laced emails, they are often targeting software and firmware vulnerabilities. Failure to patch and update them creates a pathway.
Those alerts and prompts to update software and firmware should not be treated as annoying productivity delays. Many involve shoring up the programs because a clever hacker discovered a way to breach them.
Before rebooting your business system, make certain an IT or cybersecurity professional performs all system updates. The alternative could be another data breach.
8. Recover Data from Backups
Part of a well-conceived IRP involves the redundant backing up of digital assets.
The word “redundant” is usually thought of as a bad thing in business. But in terms of digital files, the more places you store files out of a cyber criminal’s reach, the better your chances of survival.
A robust backup strategy may involve backing up data on multiple Cloud-based platforms. Secure hardware such as desktops and laptops that can be easily taken offline may prove fruitful.
Utilizing portable backup drives that are not connected to the system or internet could make them virtually untouchable.
All of these devices and platforms require vetting because clever hackers sometimes like to play a game of hide-and-seek. They could slip in malicious code that helps them get back into your network even after they are dispelled. Once a cybersecurity professional gives the thumbs-up, uncompromised digital files can be uploaded.
9. Restore Operations to Pre-Hack Days
Successfully identifying a threat, expelling the cyber criminal, and preparing the data and system for a reboot may leave an operational gap. Safety concerns may require default settings to be leveraged that point the system back to a secure point in time.
If the bad actor or breach was thwarted through early detection efforts and alerts, the operation may be able to resume productivity by turning back the settings a day or two.
But ongoing breaches in which the threat hid within your digital ranks for weeks, months, or years, create a substantial dilemma.
It’s essential to restore operation to pre-hack settings. But precisely when that occurred and the negative impact on your organization will need to be determined.
Restoring operations poses a significant challenge that calls for expert analysis to make an informed decision.
10. Train Your People About Cybersecurity
The year-over-year statistics about cybersecurity breaches consistently indicate that about 95% of hacks are the result of human error. That figure may give entrepreneurs and business leaders pause, knowing their livelihood is in the hands of newly-minted employees and interns.
But your workforce can also be a front line asset if they are properly trained. Cybersecurity awareness training allows team members to identify phishing schemes they otherwise might not recognize. Rather than rank among the nearly 30% who open malicious emails, they can stand with the 70% who do not.
Ongoing cybersecurity education can be integrated into weekly or monthly schedules by including short podcasts about emerging threats. Having your staff take 5-10 minutes to watch a video heightens their awareness. It also sends a message that industry leaders are serious about cybersecurity vigilance.
The hard numbers make it abundantly clear hackers will only grow increasingly bold in the coming years. Data breaches reportedly cost U.S. businesses an average of $8.64 million in 2020, an increase from $8.19 the year prior.
Because hackers are in it for the money, your operation needs to plan for the worst and then plan to respond to the worst.
If you feel your organization is not adequately prepared for a cyber attack, or if you’ve already been hacked, contact us today.