It’s that time of year when people are distracted. You’re probably planning for the holiday season and might be a little more focused on checking off gift and invitation lists rather than thinking about your cybersecurity plans as we head toward 2022. Distracted people are less vigilant, so unless you’ve created a cybersecurity culture that makes excellent security hygiene a routine practice, you’re at greater risk at this time of year for a security incident. You might send out memos and hold security briefings to alert employees to current threats. You might be talking about how to improve your cybersecurity posture, but what businesses need now, as we close out the year, is a cybersecurity plan for 2022. The plan should address how your business can stay a step ahead of a growing number of cyber threats. Using the following as a cybersecurity checklist can focus a company’s cybersecurity efforts.
- Commit to Ongoing Security Awareness Training
- Optimize Your Security Tools
- Confirm Mobile Devices are in Your Plan
- Customize Security for Overlooked IoT Devices
- Pay Attention to Social Engineering Threats
- Schedule Cybersecurity Audits
- Revisit Your Cybersecurity Investments
- Expand Your Cybersecurity Resources and Expertise
While we still have a few weeks left of 2021, your cybersecurity plan for 2022 should be one of the top lists that you’re checking in December. Here are the 8 key items to have on your list:
1. Commit to Ongoing Security Awareness Training
Human error accounts for 84% of data breaches. Whether it is failing to apply updates or falling victim to a phishing scam, helping employees be better cybersecurity stewards is essential to any cybersecurity plan. However, the traditional training methods may not be the best approach. 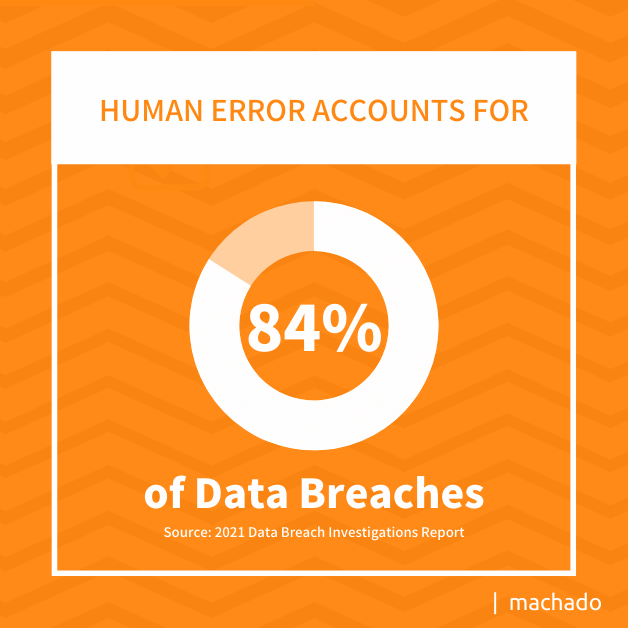
2. Optimize Your Security Tools
There are no shortages of security tools on the market. The problem is deciding what is essential for protecting digital assets. According to CISCO, a company should look at the following:
- Firewalls with Intrusion Protection. Firewalls monitor incoming and outgoing network traffic. They are the first line of defense, but they should not be the last. There are other tools that provide depth to a security plan.
- Domain Name Service Protection. Every system connected to the internet has a name/address. Being able to ensure a system is not communicating with a hacker or a malicious website can reduce the chances of employees clicking on false websites that download malware.
- Endpoint Detection. Every device connected to a network is a potential entry point for bad actors. Deploying advanced malware and anti-virus protection tools to include endpoints can reduce the chance of a network compromise. With more devices connecting remotely, endpoint detection and protection becomes a central component of any cybersecurity plan.
- Cloud-based Tools. Many businesses moved all or part of their networks to the cloud. Public clouds offer security solutions that can help defend against cyber threats. However, not all clouds are created equal and may not be PCI or HIPAA compliant.
- Email Gateway. Secure email gateways are part of a cybersecurity posture because cybercriminals continue to use email as a threat vector for the delivery of malware. Gateway tools should detect and prevent embedded code, phishing, and malicious URLs from entering a network.
These tools make it easier for in-house staff to monitor the network; however, the tools are only as successful as the people that use them. IT staff should receive the appropriate training to ensure the tools are being deployed properly.
3. Confirm Mobile Devices are in Your Plan
Mobile devices include laptops, smartphones, tablets, and wearables that are used remotely to connect to an organization’s network. Making sure that the connection is secure for transmitting data between a mobile device and the network is the focus of mobile device security. Any mobile device security process must address the possibility of an employee losing their device. 
- Management Platform. Depending on the number of mobile devices, IT staff can benefit from a management tool that provides a comprehensive view of all mobile devices.
- Virtual Private Network. VPNs, when used correctly, can provide a secure connection that shields traffic using the internet. All data moving across a VPN connection is encrypted for an added level of security.
- Secure Web Gateway. This tool defends against threats such as phishing and malware in real-time. It can help identify attacks in one location before they spread throughout the enterprise.
Mobile device attacks are likely to increase as more companies move to a hybrid work environment, where mobile connections will be the norm.
4. Security for Overlooked IoT (Internet of Things) Devices
IoT continues to be a cyber target. Because the IoT industry lacks standardization, not every IoT device has the same level of security features. When looking at deploying IoT products, companies should check the following:
- Updates. Many IoT devices do not receive frequent updates. When looking at devices, check the update history. If the device has been in the wild (real world) for years without an update, odds are it has vulnerabilities that are not patched.
- Passwords. IoT manufacturers use default passwords when shipping their products. The expectation is that companies will change the access credential before putting the device into production. Businesses need a procedure that stipulates a password change is required.
- Interfaces. IoT devices lack standards for how to interface into web, cloud, application, and mobile environments. As a result, the interfaces are often focused on ease of use rather than security. Without encryption and strong authentication, IoT devices become easy targets for hackers.
- Malware. Malware attacks on IoT devices increased 66% in 2020. Because of their weak security, IoT items provide an easy access point for cybercriminals to infiltrate a network and launch a ransomware attack.
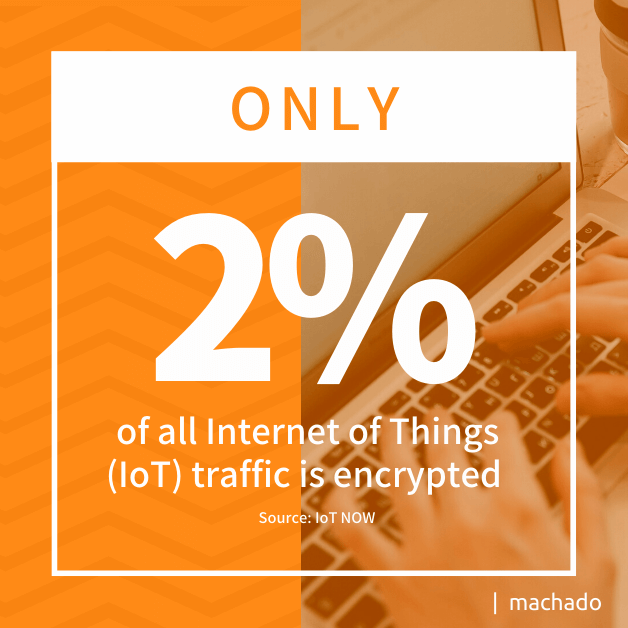
- Unencrypted Data. Only 2% of all IoT traffic is encrypted. Bad actors can monitor network traffic from an endpoint and access confidential information without detection unless endpoint protection is in place.
5. Pay Attention to Social Engineering Threats
Social engineering uses psychology to manipulate people into revealing critical information that enables a system compromise. The following three social engineering tactics will continue into 2022:
- Baiting. Hackers leverage human curiosity. Whether it is the possibility of a free download or a too-good-to-be-true offer, bad actors entice users to click on the link. Victims don’t need to try the download or respond to the offer. The virus is ready to deploy the minute the link is clicked.
- Pretexting. Cybercriminals pretend to be an executive or supervisor in an organization. They contact employees by phone, email, or messaging, asking for identifying data or directing a transfer of funds. Unless companies have policies in place to verify such requests, hackers can easily gain access to a network.
- Phishing, Bad actors have become adept at impersonating credible organizations. They may add an s to an email address, hoping no one will notice the slight change. Company logos may be added to emails to make it look like a legitimate request. Phishing is the most common social engineering threat because it works.
Keep in mind that hackers will even use social media to gain an employee’s confidence if they are targeting a specific organization.
6. Schedule Cybersecurity Audits
Cybersecurity audits identify possible vulnerabilities in a company’s security defenses. Security audits in conjunction with penetration and vulnerability assessments help strengthen an organization’s security posture. Security audits look at all aspects of an IT infrastructure, including operating systems, communications, data storage, physical servers, and data transmission and collection. Most audits are customized to address the specific infrastructure being audited. However, most cybersecurity audits include the following steps:
- Establish audit criteria. Review what is to be tested to ensure all critical systems are covered.
- Assess staff access. Document who has access to what information so the controls can be tested.
- Monitor network logs. Make sure systems are logging pertinent information on network activity.
- Identify vulnerabilities. Security audits should identify vulnerabilities that need correction, such as outdated passwords or unpatched software.
- Implement protections. Based on the results, establish procedures that strengthen defenses. These may include more frequent network audits or increased training.
Although cybersecurity audits can be performed in-house, most audits are performed by third parties. Security companies, like Machado Consulting, that offer cybersecurity auditing have the expertise to execute testing that meets compliance or regulatory requirements. For help conducting a cybersecurity audit, contact us to set up a free audit.
7. Revisit Your Cybersecurity Investments
Most companies view cybersecurity as a technical or IT problem and allocate financial resources accordingly; but, cybersecurity is an enterprise-wide concern. When a compromise happens, the impact is not isolated to IT, and the vulnerability may be the result of corporate-wide policies. When the focus is technical, the wrong questions are asked. Instead of addressing security needs as part of a list of IT requests, organizations should begin with what is required to protect digital assets. Deciding on how much to invest and on what is a business decision. It needs to undergo the same analysis as other business decisions, including a risk assessment. Can your company afford to pay the average ransomware amount of $133,000? How much business can an organization lose? 
- Detection and Escalation. This grouping covers the resources required to detect, escalate, and contain the threat. This area may involve outside parties to help with containment.
- Loss of Business. This area covers lost revenue, customer abandonment, and operational disruption.
- Notification. Communication costs for notifying customers and regulatory agencies. Public relations efforts to minimize the financial impact.
- Post-response. Companies incur legal expenditures, penalties, and fines as a result of the compromise.
Cybersecurity is not just an IT problem; it is an enterprise-wide concern that requires careful risk assessments to determine the level of investment.
8. Expand Your Cybersecurity Resources and Expertise
There are many reliable resources to help you understand the cybersecurity landscape. The US Department of Homeland Security offers a variety of publications, along with its Cybersecurity and Infrastructure Security Agency (CISA), on what is occurring in cyberspace. Any cybersecurity plan should include a list of resources that executives and employees can access to stay current on cybercrime. The Machado Consulting Blog is also a great resource that helps you to focus on your most pressing cybersecurity needs. You may also want to sign up for online cybersecurity alerts through various new sources that you regularly read online. Follow topics like cybersecurity, network security, hacks, and other topics to receive news as it hits the wires. Expanding your cybersecurity network is also a good goal in the new year. Get to know the experts in the field. They can be a great resource for your questions, share best practices, or even open doors to meet new potential employees to hire. Cybercriminals never sleep. There are always hackers actively working to compromise a system. That means new threats are constantly being deployed. Cybersecurity consultants can serve as a resource, helping organizations stay up-to-date on criminal activity. As the year comes to a close, Machado Consulting is here to help you create a cybersecurity plan for 2022 that:
- Covers critical areas such as mobile and IoT devices.
- Includes a training program that highlights social engineering techniques along with ransomware threats
- Invests in security tools and resources to help strengthen network defenses
- Outlines external and internal resources that can help
With a clear focus, 2022 can be safer for you than 2021.





