Compelling headlines about so-called “Russian Hackers” may lead you to believe Moscow poses the most imminent threat to American national security and businesses. However, a recent FBI cybersecurity alert from FBI Director Christopher Wray and the UK’s MI5 Director General Ken McCallum indicates that China presents the most insidious and determined threat to American companies and our way of life.
“The greatest long-term threat to our nation’s information and intellectual property, and to our economic vitality, is the counterintelligence and economic espionage threat from China. The Chinese government sees cyber as the pathway to cheat and steal on a massive scale,” FBI Director Wray recently shared. He went on to explain,”Chinese hackers are consistently evolving and adapting their tactics to bypass defenses. They even monitor network defender accounts and then modify their campaign as needed to remain undetected. They merge their customized hacking toolset with publicly available tools native to the network environment — to obscure their activity by blending into the ‘noise’ and normal activity of a network.” 
- 1 out of 5 companies suffered Intellectual Property theft from Chinese hackers, according to a 2019 CNBC report.
- The China threat to intellectual property theft runs between $225 billion to $600 billion annually, according to an IP Commission Report.
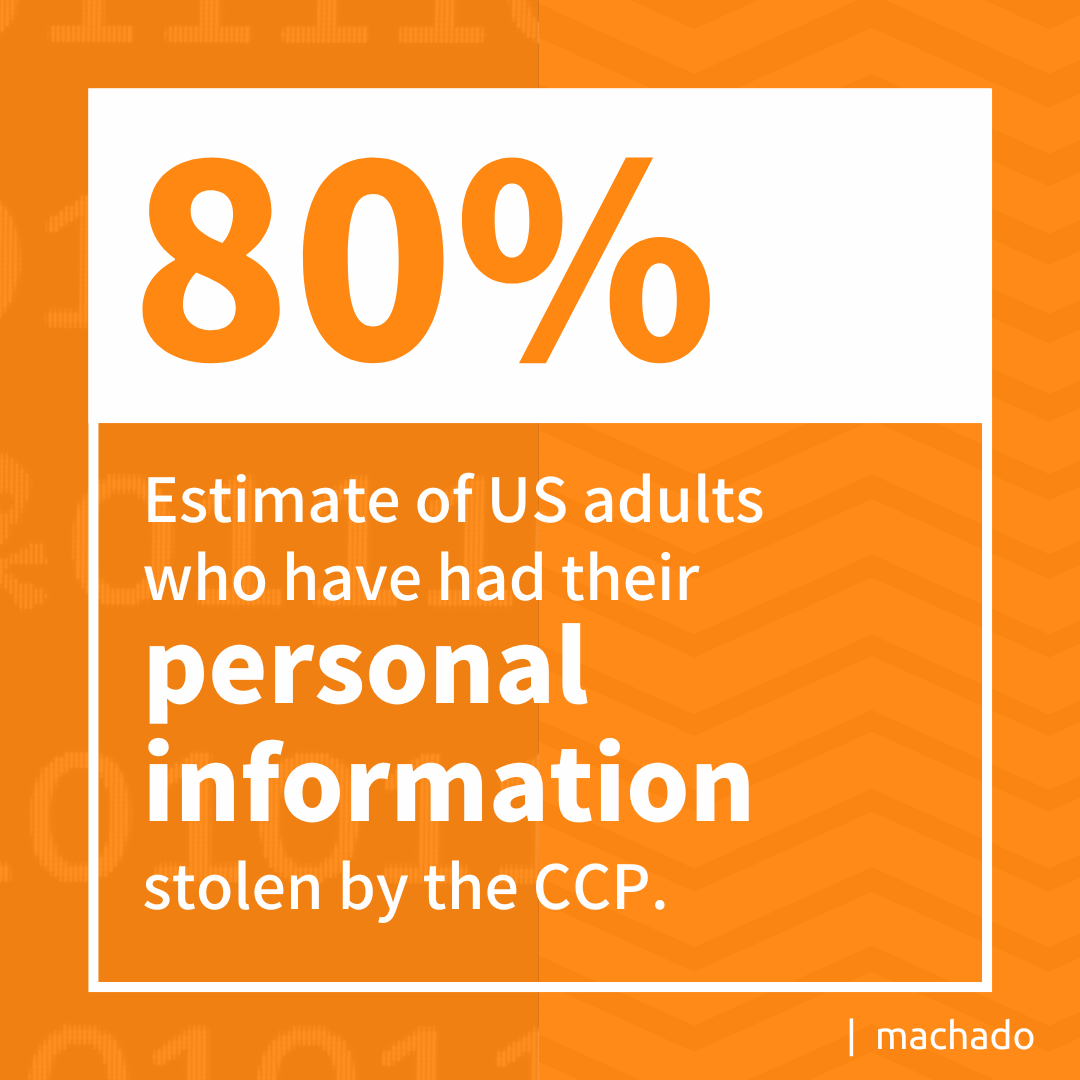
- An estimated 80 percent of American adults have had their personal information stolen by the Chinese Communist Party (CCP), according to a report in The Hill.
1. What is MI5, and Why Would the FBI Work with this Organization?
Military Intelligence, Section 5, aka MI5, is the United Kingdom’s primary domestic and foreign counterintelligence wing that acts in conjunction with other agencies. With a staff that exceeds 4,400 people, MI5 likes to promote itself as an organization of “ordinary people, who do extraordinary things.” Truth be told, MI5 is a counterintelligence agency tasked with investigating and neutralizing threats within its borders and abroad. That makes them something of a blend between America’s FBI and CIA. Its mandate to track espionage through cybersecurity attacks, monitor weapons of mass destruction, thwart terrorism, and focus on internet bad actors makes MI5 a natural partner to combat the growing China threat. As CCP cybercriminals pool their resources, US and UK leaders must respond in kind with defensive measures.
2. Critical Concerns Outlined in July FBI Cybersecurity Alert
July’s MI5 and FBI cybersecurity alert brought the critical China threat into focus. The announcement by Wray and McCallum may not garner a spotlight on prime-time cable news. Lack of critical coverage and not enough experts weighing in are precisely why small and mid-sized business leaders require support from experienced cybersecurity experts.
“If you are involved in cutting-edge tech, AI, advanced research, or product development, the chances are your know-how is of material interest to the CCP,” McCallum recently said. ”And if you have, or are trying for, a presence in the Chinese market, you’ll be subject to more attention than you might think. It’s been described as ‘the biggest wealth transfer in human history.’” 
- Covert Theft: In 2021, Chinese intelligence officer Shu Yenjoon was convicted in a US court on charges of economic espionage and theft of trade secrets from the American aviation industry. Shu was part of a prolific Ministry of State Security network targeting global aerospace corporations.
- Exploitation: The US stopped issuing visas to researchers from People’s Liberation Army universities in 2020 due to thievery. The UK implemented reforms that resulted in 50 PLA-linked students abruptly leaving the country.
- Information Gathering: The CCP has intelligence gatherers pose as legitimate diplomats. The Asia power leverages a vast network of people loyal to the CCP to accumulate and relay valuable data back to Chinese officials. The program has been exposed as the “thousand grains of sand.” Spies penetrate organizations working on cutting-edge technologies and hand the information over to the CCP to gain industry and national security advantages.
Perhaps the greatest China threat to American companies stems from cyberattacks. A hacker sitting in a state-sponsored computer facility or Beijing café typically has the deceitful skills to breach the network defenses of small and mid-sized operations. These cybercriminals may work for the CCP or sell your information on the Dark Web for cryptocurrency payoffs. Either way, your valuable and personal data will be compromised.
3. Why is the FBI Cybersecurity Alert Suddenly Cause for Alarm?
The China threat outlined by Wray and McCallum is by no means a recent phenomenon. Chinese hackers supported by the CCP, as well as rogue actors, have been targeting American and European companies for more than a decade.
A watershed moment occurred in 2010 when internet giant Google went on the record indicating it had been hacked by China. But what was unhelpful during that period was that 34 other American companies remained silent. According to NPR, technology theft and other unfair business practices originating from China are costing the American economy more than $57 billion a year,” and that figure is expected to grow. 
4. What are Agencies like the FBI and MI5 Doing to Counter China Threat?
The MI5 and FBI cybersecurity alert was a giant step in addressing preventable cyberattacks from CCP actors.
“Today is the first time the heads of the FBI and MI5 have shared a public platform,” McCallum said in July. “We’re doing so to send the clearest signal we can on a massive, shared challenge.” The challenge he was referring to is China.
Both MI5 and the FBI work diligently to identify and disrupt cyberattacks from Chinese hackers, among others. In essence, a seemingly covert war is being fought on the internet by these and other agencies against China, Iran, Russia, and other rogue nations. But the lack of jurisdiction to prosecute criminals in other countries effectively reduces the power for the FBI and MI5 from bringing thieves to justice.
While the FBI acts as a shield to protect US businesses from cyber intrusions, small, mid-sized, and large corporations need improved self-defense measures. Now that business professionals are keenly aware of the China threat, you have two choices. Either harden your cybersecurity defenses or get plucked like low-hanging fruit.
5. What Should You Do to Prevent a Chinese Cyberattack?
Immediately, you should take some proactive steps to implement basic cybersecurity hygiene. One is to begin using complex login credentials and passwords. You should also deploy the latest antivirus software and update firewalls, as well as your software applications. Such measures offer at least rudimentary defenses. But robust cybersecurity typically requires working with a managed IT firm with cybersecurity expertise to strengthen your operation in the following ways:
- Create Patching Policies and Procedures: Hackers wait patiently for you and your IT staff members to make missteps. Unpatched applications are an open door to exploit systems.
- Address Insider Threats: If you own or or work at an organization working on technological innovations, medical developments, or other cutting-edge innovations, internal threats must be considered. There are wonderful Chinese-Americans working in US companies. But be wary of members of the CCP posing as researchers. If you suspect a corporate spy, contact the FBI.
- Deploy Penetration Testing: One of the best ways to close cybersecurity gaps is to work with professionals to simulate infiltrations. An ethical hacker mimics the techniques used by cybercriminals to exploit cracks in your network’s armor. Once identified, they can be secured before the wrong person discovers them.
- Secure Crucial Assets: Re-imagine your digital network to put high-value assets and trade secrets out of the reach of cyber thieves. This entails placing data in a secure location that cannot be accessed by outsiders. Hard drives not linked to the internet may be a solution, in some cases.
- Update Cybersecurity Awareness Training: The notion that foreign hackers leverage only next-gen hacking techniques is something of a myth. Online thieves are fully aware that employees with little or no cybersecurity knowledge are likely to make a critical mistake. That’s why email phishing schemes remain one of the most common ways hackers target small and mid-sized organizations. Employees need to know how to identify electronic messages laced with malicious applications if they are to serve as the first line of defense against the China threat.
- Set Up Ongoing Cybersecurity Monitoring: You may believe that as a small or mid-sized organization that you don’t possess the financial bandwidth for ongoing monitoring and response. Managed IT firms with expertise in cybersecurity generally work with growing businesses to provide budget-friendly service agreements. This process allows companies to strategically invest in cybersecurity on a need basis.

6. Where Can I Get More Information to Deter China Hacking Threats?
The recent FBI cybersecurity alert serves as a nationwide warning that industry leaders in every sector are tasked with galvanizing their defenses. The FBI and MI5, among others, work tirelessly to obstruct and repel our enemies from pilfering off trade secrets, sensitive personal data, and intellectual property. However, it’s up to members of our business community, like you, to ensure our networks are secure and we are ready to respond to the China threat.
Federal agencies, like CISA, publish alerts during periods of heightened threats after the fact. That’s why the managed IT professionals and cybersecurity experts at Machado provide proactive services to deter hackers. Our team works with your in-house staff members to augment company capabilities and share information about the latest hacking trends.
Contact us today to learn about the benefits of working with a trusted cybersecurity partner.
We provide deep dives into networks, effectively checking the health of your servers and networks, to identify and close cybersecurity gaps. Our experienced team stays abreast of the latest schemes and delivers the cybersecurity awareness needed to make your valuable employees a frontline defense. If you’re concerned about getting hacked by China or another bad actor, let’s talk soon to discuss how, together, we can develop the determined cybersecurity you deserve.




