Not a day goes by lately when you’re not hearing about the advancement of Artificial Intelligence (AI) and how it’s changing our world in real-time. Take for instance, ChatGPT which launched in November 2022 and became the fastest-growing app in just two months. This transformation is raising questions about how AI can be used in any number of functions to help your business. One of those questions is “how is AI changing cybersecurity?” To set the stage as we address this question it’s important to know that part of the increase in cybercrime is the steady hacker-adoption of AI-based tools. Cybercriminals are busy using AI to create deepfake data, build better malware/ransomware, and use AI-based password guessing. Not only does AI evaluate potential attack surfaces faster than humans, but it also detects patterns that humans cannot see. Those patterns can lead to more sophisticated attack vectors. With AI-based tools, hackers can reach more potential victims, using more complex attacks. Given that global cyberattacks increased by 38% in 2022, it’s no wonder that cybercrime is projected to touch 45% of all businesses in two years with the help of AI-assisted tools. 
What is Artificial Intelligence (AI)?
Artificial Intelligence uses machines to simulate human intelligence processes. The technology ingests training data to look for patterns and correlations that mimic the three cognitive skills of learning, reasoning, and self-correction. Examples of Artificial Intelligence include machine learning (ML), natural language processing (NLP), and deep learning.
How is AI Being Used?
AI can be used in the following three areas of cybersecurity:
- Detection: This involves network monitoring, vulnerability scanning, and other methods for identifying a possible compromise. It means continuously looking for weaknesses that cybercriminals can exploit.
- Prediction: In other words, looking at patterns to identify possible weaknesses and assess the likelihood of the vulnerability becoming an attack. Prediction requires analysis of large datasets to be effective.
- Response: This refers to how organizations react to cyberattacks, including how quickly they can shut down a potential threat.
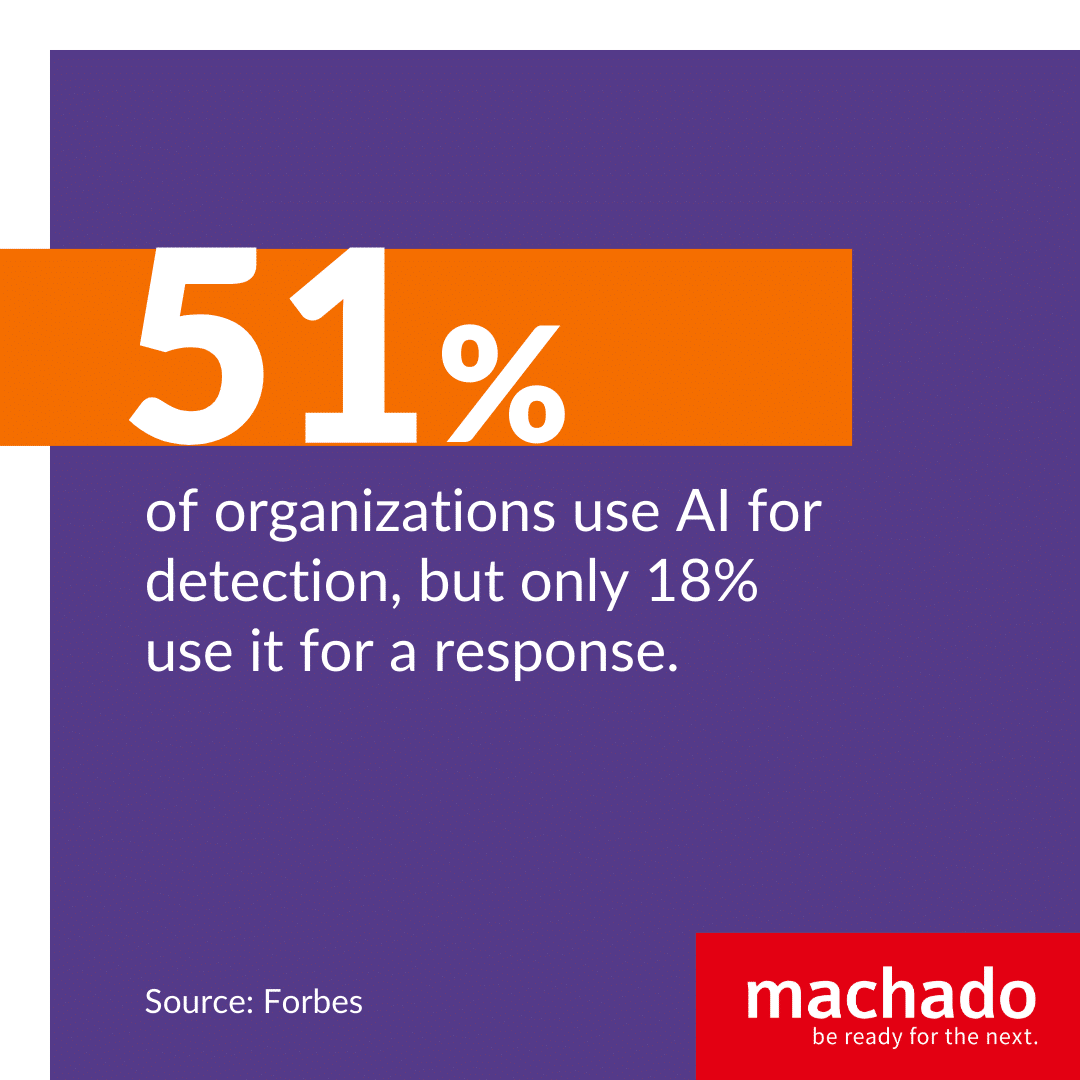
Recent studies found that 51% of organizations use AI for detection, but only 18% use it for a response. Network security was the most common AI use case, with 75% of enterprises indicating they used AI-based platforms. About two-thirds of companies use AI for data security, but only a little over half deploy it for endpoint security.
What Are the Top Cybersecurity Threats?
Although the lists may vary slightly, most predictions of the top security threats include the following:
- Malware
- Ransomware
- Internet of Things (IoT)
- Supply Chain Attacks
- Phishing
Other areas of security concern include cloud and data security. According to McKinsey, cybercriminals are no longer lone wolves, but sophisticated organizations that incorporate the latest AI technologies in their coordinated attacks. They warn that no organization is immune. Small and midsize businesses, municipalities, and government agencies face the same risks as large corporations.
How Can AI Strengthen Your Cybersecurity Defenses?
Artificial Intelligence is rapidly becoming an essential component of cybersecurity. Its ability to analyze millions of data points and predict outcomes are crucial to protecting against cybersecurity threats.
Here are eight ways AI can help strengthen your cybersecurity:
1. Threat Detection and Response
Machine learning (ML) can identify patterns quickly by processing large data sets. Once the technology knows the standard pattern, it can check for changes in the pattern that might indicate a potential cybersecurity threat. If the ML program has access to real-time data, it can adjust its findings based on the continuously updated information. Monitoring user behavior also helps establish pattern recognition. High-risk activities that occur outside of normal business hours could indicate a possible compromise. Many AI-based detection tools can also respond to potential threats. They may be configured to kill the process or lock out the user. Many will send alerts to IT for resolution.
2. Vulnerability Management
Every system has weaknesses, but weaknesses are not equal. Standard vulnerability scanners may identify flaws, but many do not prioritize them. Vulnerability tools may also generate a significant number of false positives, depending on how precise the settings are. In both instances, the results can take up IT’s time as they try to eliminate them. AI-based tools can prioritize the vulnerabilities, so staff is focused on the high-risk weaknesses. AI is also better at identifying false positives and eliminating them before they appear on a list of concerns to resolve. With a prioritized list, IT personnel can target the most severe weaknesses to harden network security.
3. Anomaly Detection
No matter the size of your business, your network experiences anomalies — those events that are outside the norm. Maybe, it’s unusually high traffic or a lack of data from a remote device. Depending on the size of your network, these events may go unnoticed. While a remote device may stop sending data because of a power outage, it could also be an indicator that hackers are attacking the device. As networks become more complex with cloud and on-premise environments, they become harder to monitor. With AI, data coming from different points on the network can be quickly analyzed, and alerts can be sent when anomalies are identified.
4. Task Automation
IT environments have numerous time-consuming and repetitive tasks as part of their daily operations, many of which can be automated. Whether it’s running daily backups to addressing credential failures, automation can free IT staff for higher-value tasks. It can also improve security operations. A small business may not have the resources to respond to multiple security alerts, especially if a significant number of false positives occur. Rather than risk a possible attempt, let AI add intelligence to automated functions. When an anomaly is detected, AI can respond. When a device stops working, let AI handle the troubleshooting and repair. As AI systems gain more data on network devices, they can provide device-specific troubleshooting tests to determine the possible problem. The program can issue a repair ticket based on its evaluation. AI can be trained to grant limited access to digital assets based on privilege settings. For example, accounting needs to provide a month-end report that requires data outside its normal domain. Based on pre-configured settings, permission could be granted to designated personnel during the first five days of the month automatically. The automated process maintains system security without human intervention.
5. Phishing and Spam Detection
Spam is more than an annoyance. It is also a security risk. Because spam doesn’t always end up in a Junk or Spam folder, it adds to the clutter in everyone’s inbox. It increases technology fatigue as people sort through their emails. Fatigue is what hackers live for. When employees are tired, they make mistakes. They click on links they shouldn’t or respond to emails without checking the sender. AI can help monitor emails. It can look for specific words or phrases that indicate a potential risk for phishing threats. It can automatically stop an employee from clicking on a suspicious link. Because AI can process emails faster than humanly possible, it can detect questionable emails and remove threats before they hit an inbox.
6. Predictive AI
Predictive AI uses its cognitive skills in rapidly-changing environments to arrive at conclusions based on evolving patterns. AI can assess real-time data to identify the most effective way to stop an in-progress attack. It can predict the most likely steps a hacker might use to complete a compromise. With this knowledge, cybersecurity personnel can execute a response plan that minimizes the risk of a catastrophic breach. More hackers are looking at employees as an entry point into a network They try to manipulate them to bypass security measures. Predictive AI can look at behaviors and patterns to predict a possible compromise. They can combine email evaluations with network activity to assess the likelihood that an event is a precursor to an intrusion attempt. AI can improve supply-chain security based on third-party behavior. It can also suggest changes in operations that can strengthen the network perimeter and inform decisions on incident response processes. Using enterprise-wide data, AI predictive models can minimize the risk of a third-party compromise.
7. Endpoint Protection
Cybercriminals love endpoints because many of the internet of things (IoT) devices lack strong security. As more organizations deploy more endpoints, the more vulnerable their networks become. It’s much harder to monitor 200 devices than it is to watch two — unless your network uses AI-based endpoint protection. A Ponemon Institute study found that 68% of organizations have experienced one or more successful endpoint attacks. About 81% of respondents said they experienced an attack involving malware, and 21% said their attacks involved compromised or stolen devices. AI-enabled endpoint security solutions quickly monitor devices connected to a network. They can determine if an activity is or is not approved. If it appears suspicious, AI can reclassify the activity to unapproved and stop its execution. For example, AI solutions can develop a “black or do not execute” list or a list of “allowed” actions. They can use that as the foundation for detecting malicious activity at endpoints. Alternatively, IT environments could deploy Zero Trust architecture that prohibits execution until the source has been verified. Combining the two approaches could execute anything on the ‘allow’ list but wait for authentication for all other processes or requests.
8. Malware Hunting
For the most part, malware protection involves detecting malware and then isolating it; however, a proactive approach looks at hunting for malware. Instead of looking for malware signatures, hunting tools monitor behavior, looking for anomalies. The tools look for activities such as:
- Resource usage. Unusually high use of CPU or memory can indicate a possible malware attack.
- Data transfer. Significant transfer of data to an external host can indicate an in-progress attack.
- Login Activity. Atypical logins at unusual times can show bad actor attempts to access the system.
Creating an AI-based hunting tool takes significant processing power to collect sufficient data to model standard operating behavior.
Getting Started
Layered security is the recommended approach for any enterprise. Many cybersecurity regulations are developed to ensure that multiple solutions are applied. Layering processes, people, and technology provides multiple defenses to counter a single attack. If cybercriminals circumvent one obstacle, they have added roadblocks to overcome. Download our free guide on staying protected from ransomware.
Be Ready for the Next Cyberattack
Need Help?
A recent survey found that IT leaders are concerned about employee burnout because of budget cutbacks and escalating cyberattacks. In fact, almost 40% of respondents were already experiencing burnout. Finding the best cybersecurity strategy for protecting your people, as well as your business requires a certified partner with deep expertise that includes the know-how to use the powerful AI tools covered in this article. Machado’s team will help you create a strategy to protect your digital assets. We also offer co-managed IT services to help protect your people from possible burnout. Whether you need help with a cybersecurity strategy or a server health check, we’re ready to help you. Let’s talk today to start securing your business.