Manufacturing consistently ranks among the most targeted sectors in terms of cyberattacks and the number of annual data breaches continues to rise. Despite suffering nearly a quarter of all incidents globally, too many manufacturers are behind the cybersecurity curve and remain a high priority for cybercriminals. By investing in determined cybersecurity and meeting the compliance requirements for the manufacturing sector, you can frustrate garden variety and sophisticated hackers alike.
Let’s review the 6 things thought leaders need to know in 2023.
1. Current State of Cybersecurity in Manufacturing
The overall level of cybersecurity confidence in manufacturing does not appear positive based on recent studies. A report published during the World Economic Forum Annual Meeting indicates only 19 percent of leaders are confident in their organization’s cyber resilience. Security Scoreboard, an outfit that assigns ratings, gave 48 percent of manufacturing corporations a grade of C or lower.
“Security ratings are a trusted barometer of cyber resilience and the time is now for policymakers and organizations to make cyber risk measurement mandatory,” Aleksandr Yampolskiy, co-founder and CEO of Security Scorecard, explained. “Cyberattacks in the last 10 years have gotten much worse, more complex, and increasingly have targeted critical infrastructure, thereby undermining the public’s trust in the cyber resilience of our global economy.”
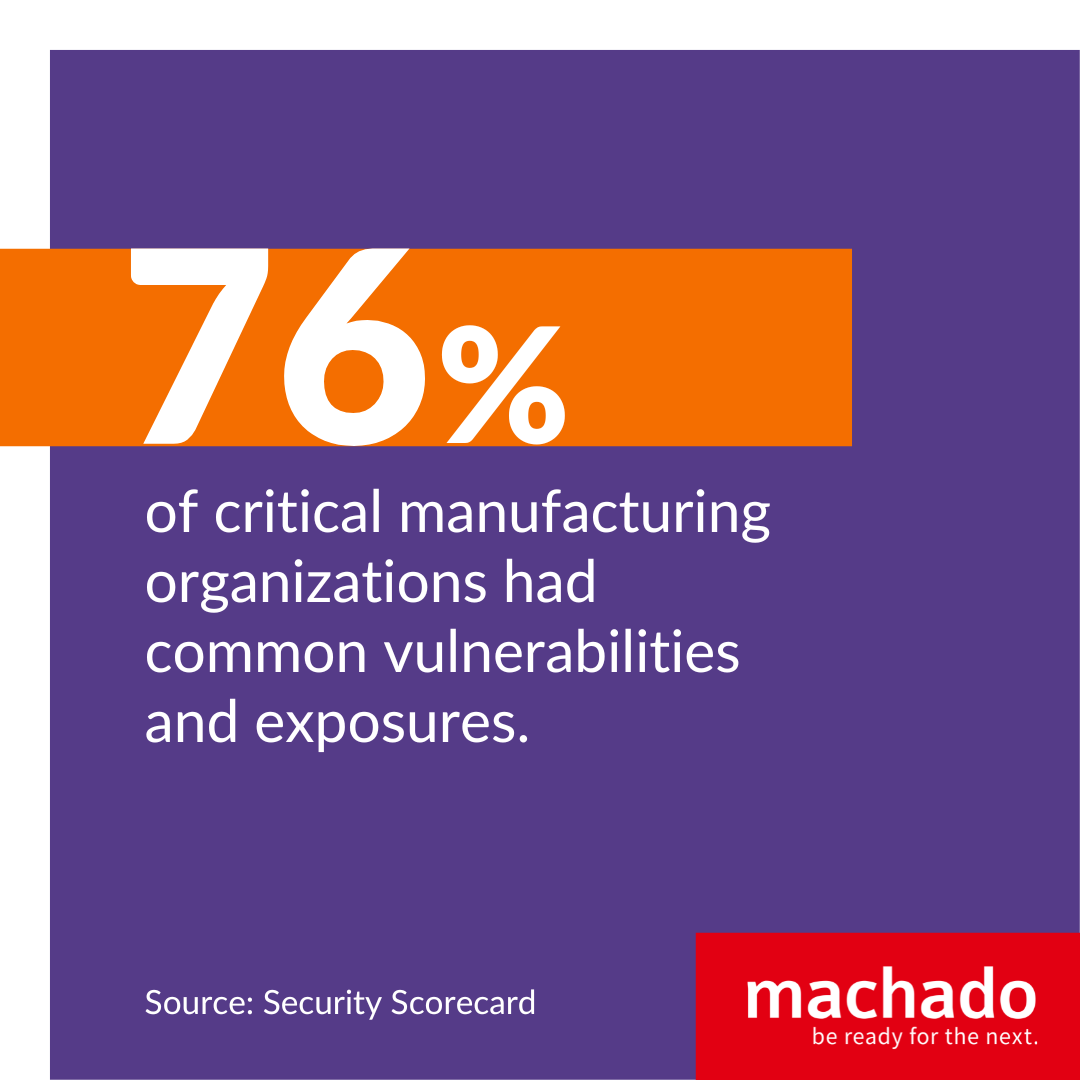
The report also pointed out that 76 percent of critical manufacturing organizations had common vulnerabilities and exposures. And more than one-third of systems possessed some form of a malware infection. These are considered the top threats facing the manufacturing industry today.
- Malware Infections: The popularity of Cloud-based networks presents unique challenges. As data moves back and forth from the Cloud, hackers try to take advantage of unsecured endpoint devices, remote users who connect to public Wi-Fi, and other vulnerabilities.
- DDoS Attacks: Distributed Denial of Service (DDoS) attacks involve the flooding of business networks with malicious requests. Hackers typically employ a cluster of devices to overwhelm a system, leaving legitimate users boxed out. Business leaders would be well-served to have cybersecurity professionals maintain a reserve internet connection with a separate pool of IP addresses. It may also be prudent to have internet traffic monitored 24/7.
- Human Error: Upwards of 95 percent of all data breaches are the result of an employee making a mistake. Hackers use social engineering and clever schemes to entice workers into downloading a ransomware file or clicking on a malicious link. This story persists year-over-year and calls for business leaders to invest in cybersecurity awareness training.
A recent Gartner report supports the conclusion that cyber hygiene and regulatory compliance are becoming something of a litmus test when doing business with other organizations. It shares, “By 2025, 60 percent of organizations will use cybersecurity risk as a primary determinant in conducting third-party transactions and business engagements.”
Many of the ongoing vulnerabilities experienced by manufacturers can be cured by maintaining their cybersecurity compliance posture. Government regulations and industry standards have been developed to protect valuable and sensitive digital assets.
2. Key Manufacturing Compliance Standards
The majority of manufacturing companies are tasked with adhering to cybersecurity and privacy regulations, laws, and industry standards. These mandates are often promulgated by federal, state, municipal, or tribal bodies. This is a short list of privacy and cybersecurity compliance requirements for manufacturing companies.
- International Traffic in Arms Regulations (ITAR): Amended in 2020 by the U.S. Department of State, ITAR regulates the export of military-relevant arms, technology, and information. Organizations that fail to comply with ITAR standards are subjected to penalties and fines.
- Payment Card Industry Data Security Standard (PCI DSS): Credit cards and bank account information is highly sought after by hackers. To protect this valuable information, compliance is typically mandated through merchant contracts.
- Sarbanes-Oxley: Passed by Congress in 2002, the federal law requires publicly traded organizations to craft and enforce formal data security policies.
- General Data Protection Regulation (GDPR): Applied internationally, the GDPR requires U.S.-based organizations to maintain heightened cybersecurity compliance regarding the collection, use, and transmission of personal identity information of EU residents.
The Federal Trade Commission Act: The FTC enjoys sweeping authority over consumer information. Companies must maintain industry-standard best practices or face onerous fines and penalties.
Organizations that participate in the military industrial base are subject to among the strictest and most complex cybersecurity mandates. In recent years, the U.S. Department of Defense brought a wide range of cybersecurity measures together. Known as the Cybersecurity Maturity Model Certification, or CMMC, the rollout is expected to impact direct defense contractors and military supply chain outfits in the coming months.
3. What Does CMMC Compliance Entail?
In response to the well-funded advanced persistent threats sponsored by enemy regimes, the U.S. Department of Defense (DoD) decided to streamline cybersecurity regulations by bringing them under one umbrella. The mandate is designed to protect controlled unclassified information (CUI) stored and transmitted by contractors, subcontractors, and peripheral outfits. Foreign hackers pilfer off this data in hopes it provides clues to our overarching national security plan.
When the full weight of the CMMC comes to fruition, the mandate is expected to impact more than 300,000 organizations. Upwards of 80,000 will be required to have a third-party assessment performed to prove they are in full compliance with the following applicable CMMC level.
- Level 1: Considered the “Foundational” level, it applies to businesses that handle Federal Contract Information. Companies can anticipate meeting standards based on 17 controls to protect against unauthorized network users.
- Level 2: Considered “Advanced” cybersecurity, this level focuses on protecting CUI. In many respects, it mirrors compliance standards outlined in NIST SP 800-171 that many military supply chain businesses previously followed. But with CMMC, organizations will be required to demonstrate compliance in advance.
- Level 3: This “Expert” level standard is meant to deter the Advanced Persistent Threats rival nations such as Iran, Russia, and China pay to steal American national security secrets and intellectual property. Operations that handle CUI can anticipate passing a CMMC audit that involves more than 130 of the toughest cybersecurity controls.
Failing to have an audit completed at your organization’s corresponding cyber hygiene level will likely result in losing lucrative government contract work. The DoD’s final CMMC rule is expected to be published in March. That means the framework could begin to appear in requests for information and requests for proposals as early as May. Business leaders who have not prepared for the CMMC rollout, or are unsure about which level applies to their handling of information, are urged to enlist the support of an expert who understands the requirements of CMMC.
4. Compliance with Industry-Specific Regulations is Essential
The importance of understanding the niche cybersecurity regulations that apply to your business and attaining compliance cannot be understated. For example, one might not anticipate the Health Insurance Portability and Accountability Act (HIPAA) applies to manufacturers of medical devices. It most certainly does and outfits that fail to follow its stringent Privacy Rule face significant consequences.
On that note, Gartner recently placed globally expanding privacy regulations among its Top Five Trends in Privacy Through 2024.
“By year-end 2024, Gartner predicts that 75 percent of the world’s population will have its personal data covered under modern privacy regulations. This regulatory evolution has been the dominant catalyst for the operationalization of privacy,” Gartner VP Analyst Nader Henein reportedly said. “Since most organizations do not have a dedicated privacy practice, the responsibility for operationalizing these requirements is passed onto technology, more specifically security, under the umbrella of the CISO’s office.”
It may also come as something of a surprise, but upwards of 47 U.S. states have enacted their own cybersecurity measures. Manufacturers may be required to promptly notify state agencies in the event of a breach. Some state laws call for the heightened protection of sensitive personal data you might not expect to apply to a manufacturing plant. Those are reasons why decision-makers work with a cybersecurity firm to ensure their organization meets or exceeds industry-specific regulations.
5. Cyber Insurance is a Must for Manufacturing Businesses
I outlined the reasons why coverage is crucial in a recent article called What is Cyber Insurance and What Should I Look for in My Policy? In the piece, we take a deep dive into insurance coverage areas and note that 48 percent of businesses only purchase a policy after they’ve been hacked. While that analysis provides valuable information about selecting the right cyber insurance policy for your operation, let’s go further and talk about compliance.
Like other forms of insurance, this coverage requires policyholders to meet certain obligations. If someone got into a car accident while their license was suspended or they were intoxicated, the insurance carrier would likely deny their claim. Similarly, a business liability claim might be rejected if the property wasn’t adequately maintained and that negligence contributed to an injury.
The same holds true of cyber insurance policies. Should an organization fail to meet government regulations or industry standards to deter cybersecurity threats, the money invested in cyber insurance coverage may be wasted. At the end of the day, cybersecurity compliance is not just a box you check. Maintaining the robust defenses articulated in these guidelines provides benefits such as full coverage in the event of losses incurred from a data breach.
6. Ongoing Training and Consultation Matters
The growing number of cybersecurity threats is a concern for businesses of every size. Although multimillion-dollar ransomware attacks on large corporations make splashy headlines, 43 percent of attacks are leveled against small businesses. And when a small or mid-sized organization gets hacked, 60 percent shutter within six months. That’s why organizations such as the U.S. Small Business Administration (SBA) publish best practices on how to help avoid a breach, such as the following.
- Safeguard your internet connection by encrypting information and using a firewall.
- Insist remote workers use a Virtual Private Network (VPN) to prevent detection by hackers.
- Enable multi-factor authentication (MFA) for network users.
- Use antivirus software and keep all software updated.
Perhaps the best advice the SBA offers is to provide employees with ongoing cybersecurity awareness training. When your valued employees learn how to spot phishing emails and recognize suspicious links, they become a cybersecurity asset instead of a liability.
It’s also essential to onboard an experienced cybersecurity firm with expertise in handling the challenges of the manufacturing sector. A cybersecurity expert can perform penetration testing to determine your organization’s strengths and vulnerabilities. The detailed report that accompanies the assessment can be used as a baseline to develop a comprehensive cybersecurity plan. It’s also a perfect jumping-off point to bring your operation into regulatory compliance.
Download your free cyber insurance compliance checklist today.Be Ready for the Next Audit
If you are concerned about gaps in your cybersecurity or unsure about aspects of your compliance requirements, it’s time to assess your defenses. Let’s talk and create a plan to ensure you and your team enjoy the sense of security and benefits that come with cybersecurity compliance.