Paying the ransom from a ransomware attack is one of those things that people go back and forth on. Should they pay it, or shouldn’t they? It is usually advised not to pay ransoms. But with these unprecedented times, businesses may have no other choice. Because of the pandemic, businesses are already struggling to stay open, never mind having a ransom held over their heads.
Just as COVID-19 has weakened balance sheets, it has also weakened IT infrastructures. With some many people working from home, remote networks have been hastily set up across the country. When misconfigured or left unprotected, these networks provide hackers a perfect opportunity to sneak in undetected.
A recent victim of a largescale attack was Garmin, a GPS tech company. They were reportedly infected with ransomware and forked over $10 million to restore the encrypted data. As a result of the initial attack, Garmin suffered a massive service interruption. Their customers’ data was also potentially compromised, though the company claims it was not.
Garmin chose to pay their ransom, but it still leaves us with the question, Should you?
Should You Ever Pay a Ransom?
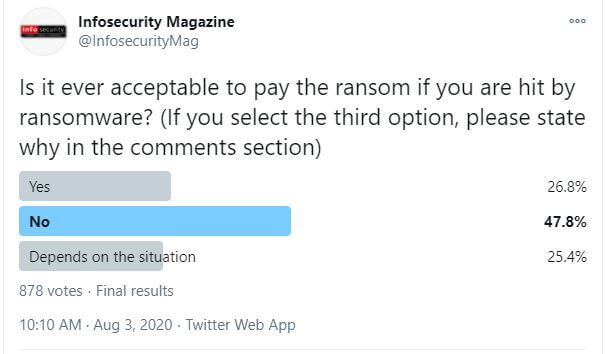
This question went out on Info Security Magazine’s Twitter as a poll. 878 people responded and the results are as follows: 47.8% said no to paying ransomware while 26.8% said yes and 25.4% opted for “depends on the situation.” This was just a poll of the public, but it offers some insight to how people think.
As a quarter of respondents said, paying a ransom depends on the situation. If, for example, a company doesn’t have their data backed up and a hacker gets ahold of it, there is no way for the company to restore their data without paying the ransom. For business-critical data, this could make the decision to pay obvious. But on the other hand, if your company has security measures in place and a way to retrieve backed up data, then you have a leg up over the hackers. In this way, data backups are more important than you might have thought. They can be the difference between paying a large sum of money or not.
Even if paying a ransom makes financial or operational sense, it can also have wider ramifications beyond just your situation. In fact, some experts believe paying ransoms encourages more bad behavior. When you pay a ransom, you’re giving the hacker what they want. This encourages them to go on and try to collect more ransoms. Jim Zuffoletti, CEO of SafeGuard Cyber, argues that it is bad policy to pay a ransom because it makes you an easy target for other hackers. If the first guy was successful, why not the next? And the next, and the next, and the—well, you get the idea. Zuffoletti offers some baselines steps to follow for better security practices here.
There could also be a situation where the ransom being demanded is less money than it would cost the victim if they didn’t pay. Dan Raywood explains that the Baltimore ransomware attack was a case where the ransom was $76,000 and the City refused to pay it. In the end, it cost them $18 million to rebuild their network. Of course, at the time, they didn’t know how much money the reconstruction would cost, but that is something that companies need to think about before making a decision on paying a ransom.
A good strategy might be to weigh out your choices and figure out what the costs could be before anything ever happens. Another idea is to hire IT support to protect your company. The low monthly costs are nothing compared to having to rebuild your entire network. Whatever you do to prepare though, if you’re infected with ransomware, you still face a tough decision: do the brave thing and deter future attacks by not paying the ransom, or save the company from potential disaster by paying?
In some cases, companies might not be able to afford any downtime, so paying the ransom is top priority. Let’s say that this is the case and you have not backed up your data. You therefore make the decision to pay the hacker’s ransom. That may be all well and good, but after paying up, you discover that the person demanding the ransom isn’t even the one who breached your security. In this case, paying the ransom gets rid of that ransom, but there’s nothing stopping the original hacker(s)—or even some third group—from demanding more. In other words, you’ve made yourself poorer but no safer. You’ve still got to expend more resources to patch the holes in your network. This is one reason why some people say never to pay a ransom: you may not even be fixing the problem at hand.
Demanding Ransom is the Last Step, Not the First
It’s helpful to understand that getting infected with ransomware is actually the last thing to happen in an attack. Before this can happen, an attacker needs to gain access to your systems. Luckily, there are ways to secure your networks. Steve Ranger lists his top three tips tips: the first is understanding your system’s weaknesses, especially when it comes to remote desktop protocols (RDP). One of the most common network vulnerabilities during COVID-19 is remote desktop protocol links being left open to the internet. These need to be secured in order to keep your network safe from intruders.
You also want to make sure to have 2FA enabled for your accounts and servers to add an extra layer of security so only you can get in. Ranger’s last tip is being able to identify when there is an intruder. One tipoff could be discovering unexpected software tools on your networks. These could have been placed there by hackers, possibly through phishing emails. Since the lockdown of your data is the last thing that happens, you have time to dig around, identify there’s been a security breach, and stop the hacker from getting any further and ultimately encrypting your data and holding it for ransom.
Overall, if you have the knowledge to stop a hacker before they infect your system with malware—or, better yet, keep them out entirely—then the best thing to do is not pay the ransom. As we have seen, however, the conversation appears to be changing. Businesses which are struggling during the pandemic are especially vulnerable. This includes health care organizations which are already under siege. Hackers have no qualms about kicking you while you’re down, and ransomware might just be the never weapon they use to capitalize on your struggles.
Pandemic or no pandemic, ransomware or no ransomware, a trusted IT partner could be just the reliable support you need in order to keep your business safe and efficient. MSPs like Machado Consulting do this by helping you streamline processes, cut-out wasteful spending and technology, connecting your employees in the office and across the world, and—perhaps most importantly—securing your networks in a way that doesn’t leave you encumbered. You can reach us here or by phone at (508) 453-4700.