News of the Apache Software Foundation’s Log4j security vulnerability started to make headlines in mid-December 2021 and could have wide-reaching ramifications throughout 2022. While already on the radar of security experts, the fact that hackers are exploiting a Log4j vulnerability has the experts worried. You should be, too, because it may impact your business if you aren’t paying attention and taking appropriate action to secure your IT infrastructure.
Log4j ranks among the common software applications used across platforms as an open-source logging product. It effectively serves as a library used by millions of organizations running online services. The Log4j vulnerability, also known as Log4jShell, provides hackers with a pathway to penetrate network security, steal valuable data, lift passwords, and infect systems with malware.
What has cybersecurity professionals particularly troubled is the fact that Log4Shell requires only basic hacking skills to exploit entire systems. If you own or operate a small or mid-sized company, here are 6 crucial things you need to know to protect your livelihood.
1. What is the Log4j Security Vulnerability?
Distributed at no cost by the non-profit Apache Software Foundation, the Log4j framework makes a record of what users do on a given device while also tracking application behaviors. The product has been downloaded into millions of computers around the world. It remains a popular tool for data collection across wide-reaching business networks, platforms, and even other applications.
Maintained by volunteers at non-profit Apache, company officials are unable to estimate how many devices could be impacted by the Log4j vulnerability. That’s largely because its particular use and insertion make it nearly impossible to track comprehensively. The experts at both the Cybersecurity and Infrastructure Security Agency (CISA) in the US and the UK’s National Cyber Security Centre (NCSC) anticipate individuals remain at heightened risk that Log4j is embedded in personal devices and routinely used online services. Organizations should expect a wide range of Cloud-based servers, applications, corporate networks, and hardware to employ Log4j. That’s why CISA and the NCSC recently warned businesses across the US and UK that the Log4j vulnerability could evolve into a hacking storm.
“The Log4j issue has the potential to cause severe impact to many organizations. As cybersecurity experts attempt to detect which software and organizations are vulnerable, attackers start to exploit the vulnerability. Initial reports indicate this is likely to include remote control malware and ransomware. However, the situation is fluid and changing regularly,” the NCSC reportedly stated.
The Log4Shell is a vulnerability that stems from a flaw with a popular Javascript library that logs error messages. Even low-level online criminals can potentially penetrate the cybersecurity defenses of companies and individuals using the flawed software. Given the disruption caused by the 2021 Colonial Pipeline ransomware attack, US cybersecurity officials have also issued an alert.
“A flaw in widely used internet software known as Log4j has left companies and government officials scrambling to respond to a glaring cybersecurity threat to global computer networks,” the Wall Street Journal reports. “The bug could enable potentially devastating cyberattacks that span economic sectors and international borders, according to security experts.”

2. What Do I Need To Do About This Cybersecurity Vulnerability?
If the Log4j vulnerability goes unpatched, malware, ransomware, and brute force attacks remain on the table. Cybersecurity compliance experts and other specialists indicate the attack barrier ranks among the easiest to overcome. As a “pre-authorization” issue, bad actors need not even log in to a system. A digital assailant can penetrate an affected device or network by deploying text messages or running a string of code in a chat window.
“Log4j vulnerabilities present a severe and ongoing threat to organizations and governments around the world,” Easterly explained. “We implore all entities to take immediate action to implement the latest mitigation guidance to protect their networks. CISA is working shoulder-to-shoulder with our interagency, private sector, and international partners to understand the severe risks associated with Log4j vulnerabilities and provide actionable information for all organizations to promptly implement appropriate mitigations.
The seriousness of this flaw to everyday people, including you and your business, cannot be understated. Major corporations with enterprise-level cybersecurity may be impacted. These reportedly include corporations such as Amazon, Apple, Tesla, IBM, and Twitter, among many others. Small and mid-sized outfits often have fewer resources to firm up defenses. Given the worldwide scale of this threat, cybersecurity compliance experts and government officials are warning business leaders to take determined measures that include the following:
- Cybersecurity Audit: Thoroughly vet every application, system, and platform that possesses public-facing internet connectivity. If you don’t know where to start, the security experts at Machado Consulting can help you prepare a comprehensive plan that includes cybersecurity and network audits, as well as server health checks. It’s crucial to place sensitive data under a cybersecurity microscope now. Personal identity records, credentials, and financial data are typically high-value targets for nefarious hackers.
- Remote Infrastructure: Organizations pivoted to increased remote workforce capability during the peak of the pandemic. Industry leaders have largely kept off site and hybrid workforces in place. The number of people working from anywhere could exceed 36.2 million by 2025. Although online talent continues to trend, cybersecurity professionals need to review routers and personal devices. Again, this is an area where the experts at Machado can help your organization today. Remote infrastructure has emerged as a link in an organization’s cybersecurity defenses, and the Log4j vulnerability must be proactively addressed.
- IT Server Health Check Apache Log4j: Defending against the Log4Shell flaw differs from the way common malware is usually eradicated. While many malicious applications can be rendered harmless by employing enterprise-level antivirus programs or following patch-over instructions, Apache Log4j creates too many vulnerabilities. Decision-makers would be well-served to enlist the services of an experienced cybersecurity specialist to identify cybersecurity risks and cure security gaps.
Industry leaders may want to consider placing the entire workforce on alert. Surfing risky websites, clicking on suspicious electronic messages, or downloading a seemingly safe application can open the door to more IT vulnerabilities. Implementing portions of a cybersecurity crisis plan may be appropriate to convey the significant danger posed by the Apache Log4j flaw. 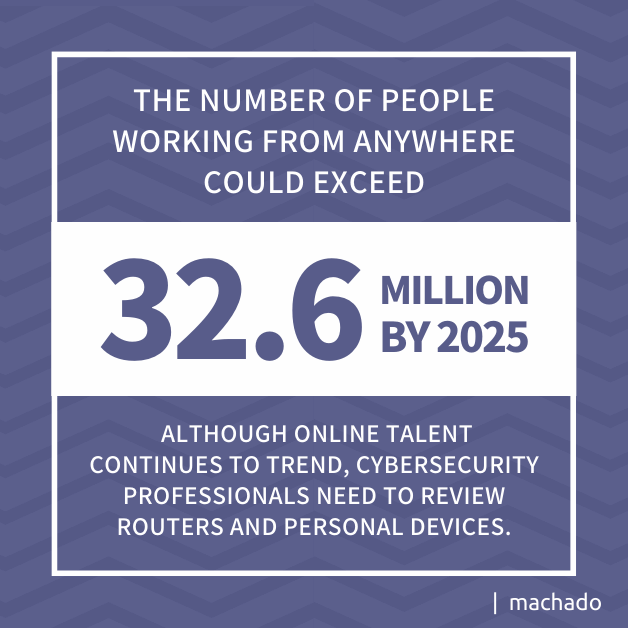
3. When was Log4j Vulnerability Identified and What is Being Done?
Although you may feel sour toward the Apache Software Foundation in the wake of a global cybersecurity risk, its volunteers were quick to sound the alarm. News reports indicate a member of Alibaba’s cloud security team found the flaw and communicated the finding to Apache on Nov. 24, 2021. Fixes were promptly considered and implemented. However, news of the Log4Shell flaw went viral after members of Minecraft video game’s cybersecurity staff shared information in a blog post on Dec. 10, 2021.
“Modified clients and third-party launchers might not be automatically updated. In these cases, we recommend following the advice of your third-party provider,” a Minecraft post reportedly stated. “If the third-party provider has not patched the vulnerability or has not stated it is safe to play, you should assume the vulnerability is not fixed, and you are at risk by playing.”

“We have observed many existing attackers adding exploits of these vulnerabilities in their existing malware kits and tactics, from coin miners to hands-on-keyboard attacks. Organizations may not realize their environments may already be compromised,” the software giant’s post reportedly states. “Microsoft recommends customers to do additional review of devices where vulnerable installations are discovered. At this juncture, customers should assume broad availability of exploit code and scanning capabilities to be a real and present danger to their environments. Due to the many software and services that are impacted and given the pace of updates, this is expected to have a long tail for remediation, requiring ongoing, sustainable vigilance.”
Organizations such as CISA, the National Security Agency, and the FBI are taking action to increase awareness and investigate data breaches. The global nature of the compromised Apache application has officials in nations such as Australia, Canada, New Zealand, and the UK on high alert as well. Although large companies are taking steps to inform the general public, this vulnerability has wide-reaching implications across an untold number of platforms.
Patches have been issued, but the ubiquitous nature of the Log4Shell requires ongoing efforts on the part of individuals and organizations. Essentially, outfits that store valuable data on in-house networks, devices, or in the Cloud are best served by bringing in a third-party cybersecurity firm immediately. In other words, it’s important for you to take proactive measures for your own business.
4. Where Can I Learn More and Get Help to Address Potential Threats?
Updates regarding the Log4j vulnerability continue to trend on technology and cybersecurity news sites such as ZD Net, Tech Crunch, and Gizmodo, as well as mainstream media outlets such as CNBC and the Wall Street Journal. While these resources help business professionals with access to current information, proactive measures at the local level remain critical.
Businesses are advised to reach out to third-party cybersecurity firms. Local cybersecurity experts such as Machado Consulting in Worcester possess the knowledge and experience to conduct audits, close vulnerabilities, and vet your remote infrastructure. Consulting firms bring a laser focus to bear that goes beyond the responsibilities of in-house IT professionals. Determined cybersecurity that defends against Log4Shell and the next wave of online attacks requires business owners and decision-makers to harden their defenses or get harvested along with the other low-hanging fruit.
5. Is Log4Shell Really a Threat to My Small Business?
No doubt, you often see splashy headlines about multi-million hacks and ransomware attacks. These big-money reports typically focus on Fortune 500 corporations and almost imply hacks are not necessarily directed at small businesses. Nothing could be further from the truth. According to resources such as Cyber Security Magazine and others, the statistics indicate small and mid-sized organizations are at heightened risk of a breach.
- Upwards of 43 percent of data breaches target small and medium-sized businesses.
- More than 60 percent of small and mid-sized organizations suffered at least one attack in the last year.
- Approximately 40 percent of small businesses suffered at least 8 hours of downtime from a severe attack.
- About 83 percent of small and mid-sized outfits are not financially ready to sustain a hack.
- Over 90 percent of small businesses have not purchased cybersecurity liability insurance.
Small and mid-sized organizations sustain average losses of approximately $108,000 per breach or $150 per stolen data file. More than 60 percent of small companies shutter their doors within six months following a cybersecurity incident. Common reasons involve revenue setbacks, irretrievable data, and a tarnished industry reputation. 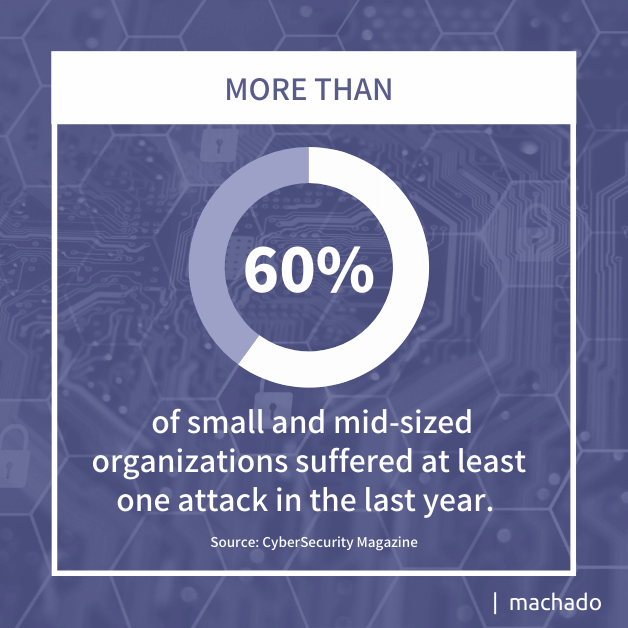
6: How Can I Protect My Business?
The worldwide and real-time connectivity provided by the internet allows businesses of all sizes to compete on a level digital playing field. Reaching otherwise unavailable markets to shop goods and services increases an organization’s bottom line. Small and mid-sized operations also enjoy access to talent pools outside their employee commuter radius.
But with these benefits comes the risk of a hacker halfway around the world exploiting vulnerabilities such as the Log4jl. Large corporations have the resources to maintain a team of cybersecurity professionals to monitor their defenses. Small and mid-sized companies can match their ability to deter threats by partnering to protect their digital defenses with an IT security expert like Machado. These are solutions a third-party cybersecurity consultant routinely offers.
- Cybersecurity awareness and training for employees and stakeholders
- Cure vulnerabilities and close cybersecurity gaps
- Secure remote infrastructure and devices that connect to the network
- Ensure daily backups are conducted, and critical data is stored in secured locations
- Limit employee login access to select areas of the network
- Conduct an IT server health check/Apache Log4j audit
- Ensure organizations meet industry cybersecurity compliance guidelines
- Bring company leaders together to craft a cybersecurity response plan of action
The Log4j danger stands as just the latest in a long trail of threats that endanger small, mid-sized, and large corporations. Hackers reportedly level upwards of 2,200 daily cyberattacks, and that number could exceed 800,000 this year. As a business leader you should be concerned right now about your organization becoming the low-hanging fruit for a foreign cybercriminal. Let’s talk about how your business can be better protected from security threats in the months ahead. We can start with a free cybersecurity or network audit to identify your immediate risks and put together a plan to not only better protect your data, but to also help you and your IT leaders sleep at night.





