Over the past year, you’ve been hearing from us about the Cybersecurity Model Certification (CMMC) compliance requirements first outlined by the U.S government in 2019. While our focus has been primarily on how CMMC will impact manufacturing businesses, the reality is that all organizations connected to the military supply chain should plan to harden their cybersecurity, This is especially important to pay attention to now because the U.S. Department of Defense is mandating a new set of guidelines hailed as CMMC 2.0.
If you’re just catching up on understanding CMMC and are wondering why the sudden transition to CMMC 2.0, here’s some background to bring you up to speed. But first, keep in mind, if you’ve already been working on your CMMC preparation, that’s great! The good news is that you’re well on your way to aligning with the new CMMC 2.0 guidelines.
Background to Better Understand the Need for CMMC
Initially announced three years ago, the Cybersecurity Maturity Model Certification (CMMC) protocols were designed to bring wide-reaching defense policies under one umbrella. The stunning SolarWinds hack may have caused officials to rethink their initial rollout. In early December 2020, a prominent cybersecurity firm called FireEye reported the theft of ethical hacker applications. 
According to CMMC Accreditation Body board of directors chair Karlton Johnson, “A determined adversary with the right capabilities is going to find their way in, especially if they put all their resources to bear on it.”
Although the Pentagon insists its cybersecurity defenses were not compromised, upwards of 18,000 software users downloaded malicious applications. This unprecedented covert hack may have been operational for upwards of a year. And, it was reported only weeks after newly-minted DoD CMMC (version one) rules were set to take effect.
Worried contractors who conducted CMMC compliance due diligence were concerned about potentially hefty fines or having their contracts suspended. But the unique and duplicitous methods of these alleged Russian hackers led officials such as former Chief Information Security Officer for Acquisitions Katie Arrington to give them a pass.
“SolarWinds wasn’t normal. No one is going to take that against you and take your certification away against a nation-state actor penetrating in a way that has never been done before — absolutely not,” Arrington explained. “But if you come in, and there’s a cyber incident at your company, and it happened because you weren’t deploying your multi-factor authentication, then you do run a risk.”
What’s frightening — from a national security perspective — is that SolarWinds is not necessarily a direct DoD contractor. Still, the digital assets of nearly 40 defense companies were compromised. That’s why private-sector businesses need to buckle up and bring in a third-party cybersecurity professional to protect their valuable digital assets, customers, colleagues, and our national security by repelling enemy-state hackers. The DoD appears to be banking on CMMC 2.0 getting the job done.
Key Takeaways from Initial CMMC Compliance Measures
Painstaking efforts have been made to develop the DoD CMMC guidance, and people in the cybersecurity industry understood adjustments would be forthcoming. Many of the bedrock defenses and strategies will remain in place under new guidelines. However, business leaders can anticipate minor tweaks to some networks and major overhauls of others. These are top-line issues business professionals were required to meet under CMMC.
Who Needs CMMC certification?
More than 300,000 DoD contractors and outfits involved in the military-industrial base have been tasked with improving cybersecurity defense. Each operation is required to identify its CMMC compliance level and meet the standards. To remain in the supply chain, organizations are required to pass a third-party audit by a scheduled date.
Levels of CMMC Compliance
An entity’s use, storage, and transmission of Controlled Unclassified Information (CUI) correlated to one of five CMMC levels. These range from Level 1, also known as basic cyber hygiene for peripheral companies, to Level 5 defenses that are able to deter advanced persistent threats. The Russian hackers who infiltrated SolarWinds would fall into that class of criminal.
Ongoing Cybersecurity Measures
Businesses that achieve CMMC compliance are required to maintain their cybersecurity levels. The federal government mandated ongoing reporting to ensure companies don’t approach this as a one-off. That’s largely because organizations that fail to update software, antivirus packages or don’t provide ongoing cybersecurity awareness training pose a risk.
The fundamental thinking around cybersecurity will not necessarily change when CMMC 2.0 applies. But firms bidding on lucrative government work will need to meet the newly-minted CMMC 2.0 regulations. The alternative is to find yourself outside a profit-generating industry.
What Are Experts Saying About CMMC 2.0?
Pentagon officials are not sugar coating the impact the CMMC 2.0 mandate will have on defense contractors and supply chain outfits. David McKeown, deputy chief information officer for cybersecurity at the DoD, indicates that upwards of 80,000 businesses may need a third-party IT audit to meet the new standard. 
John Sherman, principal deputy chief information officer, echoed those sentiments when fielding questions about CMMC 2.0. He also indicated that greater emphasis would be placed on strengthening cybersecurity measures among the small and mid-sized business ecosystems.
“I can tell you what it means to me. It means raising the waterline of cybersecurity across the DoD to keep the Chinese and Russians, and other potential adversaries away from our critical data. This is basic hygiene to raise the water level to make sure we can protect our sensitive data so that when our service members have to go into action, they’re not going to have an unfair position because our adversary’s already stolen key data and technologies that’ll put them at an advantage,” Sherman reportedly said. “There’s a cost to your IP, there’s a cost to the U.S. government, and there’s a benefit to our adversaries if we don’t do something like this.”
Decision-makers at small and mid-sized organizations are probably wondering how this sudden shift affects them, given you are already in the midst of CMMC compliance. The new guidelines will build upon tried and true cybersecurity practices. It’s likely that the investment into protecting your valuable digital assets won’t be for naught. The updated government regulations would likely have required them anyway. Therefore, you are already on the path to CMMC 2.0 compliance and passing an IT audit. However, business leaders would be well-served to plan to improve their capabilities.
How is the New DoD CMMC 2.0 Compliance Different?
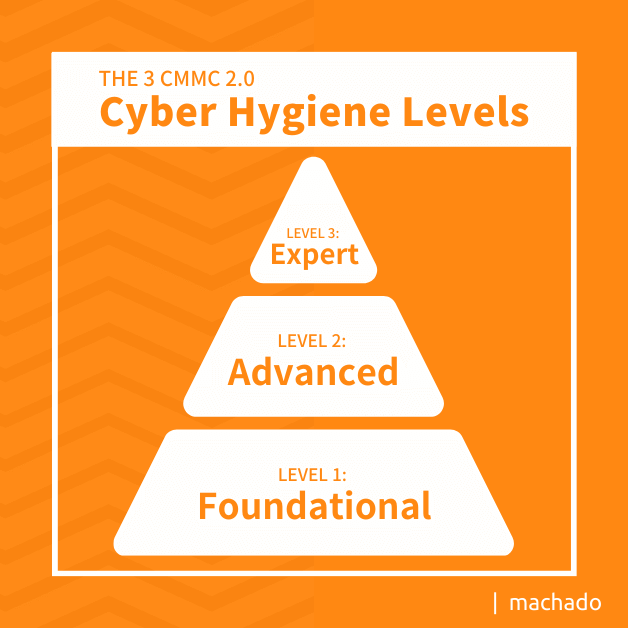
Some officials have floated the idea that CMMC 2.0 somehow relaxed the rules. Nothing could be further from the truth. The new regulations do, in fact, reduce the number of cyber hygiene levels from five to three. An increased number of small and mid-sized businesses that store, access, or transmit Controlled Unclassified Information (CUI) will likely require more robust cybersecurity. The following summarizes the three CMMC 2.0 cyber hygiene levels.
- Level 1 (Foundational): If your company neither receives, processes, or creates CUI, nor does it come in contact with high value assets (HVA), self-assessments may be appropriate. Any IT audit or cybersecurity penetration testing must be affirmed by the outfit’s leadership.
- Level 2 (Advanced): This level pertains to businesses that receive, process, or create CUI but not HVA. In some qualifying cases, an annual self-assessment may be an option. Others are tasked with passing a Certified Third-Party Assessor Organization (C3PAO) assessment.
- Level 3 (Expert): Any contractor that manages HVA may be subject to a government-run assessment. This level typically requires companies to develop cybersecurity defenses able to resist and react to advanced persistent threats.
Based on information released by the federal government, CMMC 2.0 appears to be something of a mixed bag. Some small and mid-sized organizations may not necessarily need to schedule a C3PAO analysis. By that same token, many others may need to improve their cyber hygiene above and beyond earlier expectations. Perhaps the companies that are now included in CMMC 2.0 Level 2 will experience the greatest confusion. Industry leaders need to make the right choice regarding self-assessments or C3PAO reviews. The wrong call could prove costly.
What You Need to Know About CMMC 2.0
When the Pentagon decided to bring wide-reaching cybersecurity guidelines under one roof, it was a lot to digest. Business leaders are usually laser-focused on providing goods, services, and materials in the DoD supply chain. Amping up cybersecurity defenses is generally a considerable distraction. That’s why bringing in cybersecurity professionals who follow government mandates and know how to implement them saves time and money. For the purposes of understanding the broad strokes of the impending CMMC 2.0 rollout, consider these critical takeaways from information released by the Pentagon.
- Once CMMC 2.0 is codified through rulemaking, the Department will require companies to adhere to the revised CMMC framework according to requirements set forth in regulations.
- Impact on DoD Contracts: CMMC 2.0 will not be a contractual requirement until the Department completes rulemaking to implement the program. CMMC 2.0 will become a contract requirement once rulemaking is completed.
- Mandated Costs: Costs are projected to be significantly lower relative to CMMC 1.0 because the Department intends to (a) streamline requirements at all levels, eliminating CMMC-unique practices and maturity processes, (b) allow companies associated with the new Level 1 (Foundational) and some Level 2 (Advanced) acquisition programs to perform self-assessments rather than third-party assessments, and (c) increase oversight of the third-party assessment ecosystem.
- Cyber Hygiene Levels: Once CMMC 2.0 is implemented, DoD will specify the required CMMC level in the solicitation and in any Requests for Information (RFIs), if utilized.
- Impact on Subcontractors: If contractors and subcontractors are handling the same type of FCI and CUI, then the same CMMC level will apply. In cases where the prime only flows down select information, a lower CMMC level may apply to the subcontractor. Compliance Deadlines: CMMC 2.0 compliance is only required in select pilot contracts, as approved by the Office of the Under Secretary of Defense for Acquisition and Sustainment.
How To Get Started to Meet CMMC 2.0 Standards
The first step to prepare for the CMMC 2.0 mandate involves conducting a thorough review of your cybersecurity defenses, as well as a comprehensive IT security audit.
You can request a free network security audit here.
Unpatched software, outdated antivirus applications, and employees not receiving adequate cybersecurity awareness training rank among the leading deficiencies. It may sound like fiction, but a SolarWinds intern reportedly used the password “solarwinds123” and posted it on GitHub for more than 12 months. That is precisely the lack of cybersecurity awareness training that disrupts businesses and poses a national security threat.
Meeting the CMMC 2.0 standards entails working with a cybersecurity expert, who can correctly identify the appropriate cyber hygiene level, craft a detailed plan of action, and help educate key stakeholders within your organization about hacking schemes. Strategies such as multi-factor login authentication, zero-trust user profiles, and performing a server health check can do more than check a government mandate box. They provide your organization with the tools to deter hackers and do your part for national defense.