The state of cybersecurity compliance is under a microscope right now, with more attention than ever coming from government entities at the State, Federal, and Global levels. Until recently, awareness of cybersecurity incidents relied primarily on businesses to self-report network intrusions and data theft. This has been due to lack of regulations for cybercrime reporting.
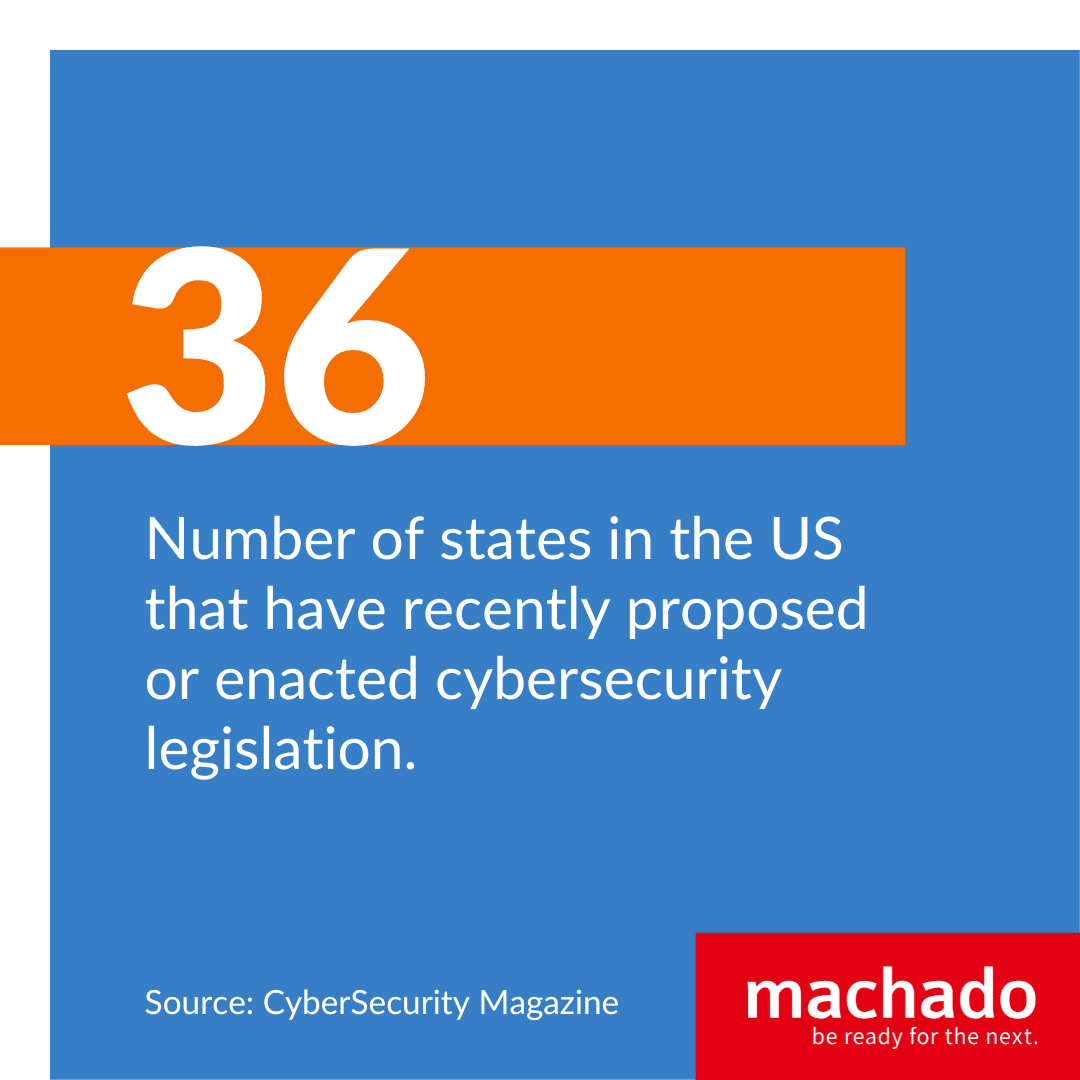
According to a recent article in the Harvard Business Review, “In the United States, a whole suite of new regulations and enforcement are in the offing: the Federal Trade Commission, Food and Drug Administration, Department of Transportation, Department of Energy, and Cybersecurity and Infrastructure Security Agency are all working on new rules. In addition, in 2021 alone, 36 states enacted new cybersecurity legislation Globally, there are many initiatives such as China and Russia’s data localization requirements, India’s CERT-In incident reporting requirements, and the EU’s GDPR and its incident reporting.”
The new focus to create more cybersecurity regulations comes at a time when the world is losing almost $200,000 every second or $12 million every hour to cybercrime (that figure doesn’t include indirect damages resulting from attacks on infrastructure, healthcare, or energy). This is driving governments around the globe to create new regulations to improve cybercrime reporting and threat awareness. 
- Businesses do not want the hassles associated with filing a report.
- Companies do not want to lose customer confidence – a cybersecurity intrusion is a potential Public Relations nightmare.
The introduction of cybersecurity legislation around the globe is an attempt to improve cybercrime reporting. It’s important to note that cybersecurity compliance for these new regulations is not one-size-fits-all. For organizations located in a given jurisdiction, cybersecurity compliance could become mandatory. For businesses selling to residents in certain countries or states, security requirements may apply. Noncompliance to these new regulations can result in severe penalties, so it’s important for you to know how your business may be impacted based on where your business and your customers are located.
Be Ready for the Next Cyberattack
Download our free guide on staying protected from ransomware.
Global View
In April 2022, India issued updated CERT-In incident reporting requirements. This update expanded the types of incidents that require mandatory reporting and stipulated a six-hour window from the time of discovery to incident reporting. The regulations apply to companies doing business in India, regardless of where the server is located. Failure to comply can result in fines or imprisonment.
Australia passed similar legislation that took effect in July 2022. Critical cybersecurity incidents must be reported within 12 hours and non-critical incidents within 72 hours. The ruling applies to critical sectors such as communications, healthcare, finance, and energy. The minimal financial penalty is $11,000.
The European Union’s General Data Protection Regulation (GDPR) was enacted in 2016 and put into effect in 2018. It gives EU residents the “right to be forgotten.” Residents may request the removal of their personal data from any website regardless of where the company is located. Failure to comply can result in a fine of one million Euros or 2% of a company’s total revenue. 
Federal View
When President Biden issued his executive order on cybersecurity in May 2021, he directed agencies to institute policies to strengthen US cybersecurity defenses. To that end, departments and agencies have been developing new cybersecurity requirements.
Federal Trade Commission
The FTC only required sector-specific breach notifications, with some attacks going unreported. As of May 2022, entities suffering a breach, regardless of the sector, have an obligation to disclose the incident to help mitigate harm arising from a cyberattack. This change expands the FTC’s oversight of cybersecurity to any industry sector.
Stock Exchange Commission
The SEC wants publicly traded companies to disclose to clients any cybersecurity risk regardless of its significance. They want businesses to report any significant cybersecurity incident to the SEC within 48 hours of discovery. The commission defined significant as any incident that substantially harmed an investor, client, or advisor.
Food and Drug Administration
The FDA is waiting on public commentary on a proposed initiative on vulnerability management. Specifically, the FDA is contemplating a software bill of materials (SBOM) that requires companies to know the cybersecurity defenses of their software suppliers.
Federal Departments
The Department of Defense (DOD) has a Cybersecurity Maturity Model Certification (CMMC) in place for all companies wanting to do business with the department. Other departments, such as transportation and energy, are working on their guidelines for implementing security measures and reporting incidents. As government departments and agencies continue to work on cybersecurity regulations, companies of all sizes must be cognizant of the changing landscape of cybersecurity compliance.
State
In the US, 36 states have proposed or enacted new cybersecurity legislation in the last few years. Three of those states are in New England and include MA, RI, and NH.
Massachusetts
Massachusetts has grappled with data privacy and security for years. The legislature has several pending actions to establish and operate a more coordinated effort through the Massachusetts Information Privacy and Security Act (MIPSA). The legislation limits how companies can use personal information, giving consumers more control over their data. It is designed as a comprehensive solution to protect consumers and companies. The Act provides for an opt-out clause for consumers where appropriate. Violations may result in a fine, plus individuals can litigate against companies that they believe violated their rights. The law applies to data brokers as well as other businesses. The group has the ability to enforce the regulations and assess fines.
Rhode Island
Rhode Island has pending legislation that would create a cybersecurity incident response group. The group’s responsibility would be to establish breach-related protocols for agencies and public entities to notify the response group within 24 hours of a breach or a suspected incident. Businesses would have up to 15 days to notify individuals.
New Hampshire
New Hampshire enacted a law in August 2022 that requires any political entity, including vendors, to report all cybersecurity incidents to the Department of Information Technology. Cyber incidents are any occurrence that jeopardizes the integrity, confidentiality, or availability of stored data and applies equally to towns and cities.
California
California has the most stringent cybersecurity laws for data privacy in any state. Many states, such as Massachusetts, are modeling their government regulations after the California Consumer Privacy Act of 2018 (CCPA). Under the law, consumers have a right to know what information is being collected, to ask that information be deleted, and to opt-out of the sale of their data.
How You Can Prepare for New Regulations
For organizations falling under SEC jurisdiction, their preparation begins in the boardroom. Under new cybersecurity regulations, the Board of Directors has a responsibility to ensure that cybersecurity defenses are in place. A knowledgeable cybersecurity expert should assist the board in evaluating security risks, and executives should ensure that the company’s infrastructure supports a strong cybersecurity posture.
Business leaders can no longer place the responsibility on someone in IT. They must ensure that the resources are available to protect and defend their infrastructure. They must implement effective cybersecurity policies that revolve around readiness, response, and remediation.
1. Readiness
Being prepared with a proactive IT approach is the best response to a cyberattack. Vulnerability assessments identify your existing cybersecurity capabilities and prioritize weaknesses based on risk. Road maps are developed to illustrate how organizations get from where they are to where they need to be. This fundamental process can form the basis for reporting requirements.
Reporting isn’t just about a specific incident. It’s also about an overall defense posture and governance. As part of a cybersecurity plan, companies need to outline the capabilities and processes they have and then address reporting requirements that include cybersecurity compliance. It’s essential to have a cross-functional security team to build a company-wide security mindset.
Within the security team, organizations should identify individuals who are responsible for monitoring ongoing legislation. Staying current on compliance trends makes it easier to integrate the final regulations into an overall plan. Refining existing processes is much faster than having to develop them.
2. Response
How does your organization respond to a network security breach? Who is responsible for containment? Who notifies the Board and reports to the appropriate authorities? What will your cyber-insurance policy cover? Without a plan, responses could be delayed or people could be working at cross-purposes to minimize the threat.
For example, if your business has connections with India, what happens when no one notifies India’s cyber authorities that an incident occurred within the six-hour window? Companies are assessed fines. In extreme cases, executives could be incarcerated. A formal incident response plan should include the following:
- Identify escalation protocols for different cyber threats.
- Indicate the potential security impacts based on industry and government regulations.
- Stipulate the procedures required to adhere to industry standards.
- Discuss the roles and responsibilities across all departments during a security incident.
- Describe the communication procedures to follow to keep stakeholders informed.
- Prepare a plan for notifying individuals if their information was compromised.
- Develop a communication plan for informing government agencies of a network security breach that complies with cybersecurity regulations.
- Set measurement strategies for testing response effectiveness.
- Maintain an up-to-date list of contact information for the response team.
Cybersecurity professionals may be the only individuals who understand a comprehensive incident response and reporting plan, but everyone should be aware of the part they play in its implementation. Educating staff about cybersecurity threats and prevention is essential to developing a security-minded workforce.
3. Remediation
Remediating a cybersecurity breach means limiting the damage to business operations by addressing the threat quickly and effectively. Threats that go unnoticed can leave systems inoperable. Remediation tries to detect and contain network security incidents before they compromise operations.
A response plan should reference the remediation process to follow based on the type of security threat. Sometimes killing a process is not the best approach to mitigating a security threat. Hackers can remain in the system after a single process is stopped. While IT personnel may think the threat has been contained, hackers are continuing to compromise the system.
Remediation must focus on detecting the cause of the compromise, so it can be contained. Having remediation processes outlined in advance of an incident ensures that best practices are followed and that critical information is retained for analysis. Remediation should take into account the cybersecurity compliance requirements for all applicable industry and government regulations.
Are You Ready?
Complying with cybersecurity regulations can be a full-time occupation, especially as businesses expand beyond their local markets to include national and international customers. But, ignoring the requirements can have financial consequences for business operations. Fines and penalties are usually on top of the cost to respond and remediate a network security breach.
Creating a cybersecurity action plan with a co-managed IT provider that specializes in cybersecurity compliance can reduce your in-house burden of staying current on developing legislation. The right partner has the experience and expertise to help with vulnerability assessments. They can help devise a road map and plan to keep your organization in compliance and assist in developing reporting processes to meet compliance standards. Are you ready to learn more about how you can maintain your cybersecurity compliance with the latest regulatory standards? Let’s get started today to create the right action plan to protect your business.
Be Ready for the Next Cyberattack
Download our free guide on staying protected from ransomware.